Home » Technology » Networking (Page 3)
Category Archives: Networking
Game Changer: Hooking Up Facebook with Incredible PBX

There aren’t many VoIP discoveries that get us this excited about the future of telecom. But merging with 1.5 billion users plus Facebook’s enormous talent pool and technology resources is definitely something worthy of your attention. What a Facebook marriage with the VoIP platform could mean for the future of telecommunications is nothing short of earth-shattering. Few people still have home phones. Almost everyone has a Facebook account and a cellphone. If VoIP solutions for businesses fail to take those last two sentences into account, commercial PBX’s days are numbered… and it’s not a big number.
So why integrate Facebook Messenger into your PBX? The screenshot above says it all.
Think of the possibilities. Using Facebook Messenger on your smartphone or desktop PC, you could query a CRM database running on your VoIP server and instantly connect to anyone in the world by making a free call or sending a free text message. Using Facebook Messenger, you or any designated employee could receive instant alerts when a new voicemail or fax arrived on your PBX. Using Facebook Messenger, the Call Center possibilities are virtually endless as documented here. Using Facebook Messenger, you as an administrator could literally manage your entire fleet of PBXs from the convenience of your smartphone… anywhere in the world. While the Facebook Messenger platform does not independently support phone calls between its users today, it’s just a matter of time. Look at the name of the product. Is there any doubt where this project is headed given the fact that Apple already supports free calling with Facetime, Microsoft supports free calling with Skype, Google supports free calling with Google Voice, and Amazon supports free calling with its Echo platform?
Facebook integration is revolutionary in another way as well. It heralds the arrival of chatbots to do the heavy lifting for telecom businesses as well as system administrators. Just as ATMs revolutionized banking, chatbots are poised to do much the same thing for communications and Internet support. Down the road, we’ll document how to take advantage of this chatbot technology using Facebook Messenger.
We need to learn to walk before we can run. So today we’ve developed a Facebook webhooks integration project for Incredible PBX® that is perfect for administrators, whether you manage a home PBX or a dozen PBXs for an organization. We’ll get to some of the other possibilities in future articles. Setting this up is the best way we can think of to get your creative juices flowing to consider what’s possible and to identify where to go next. When we’re finished, you’ll have a Facebook Messenger platform from which you can issue any Linux® or Asterisk® command to your server. And, you’ll be able to send messages from your PBX to Facebook Messenger to identify any events you wish to monitor, whether it’s phone calls, or voicemails, or receipt of faxes, or even VoIP provider outages. In addition, you can even reroute calls by entering simple call forwarding commands in Messenger.
Before we get started, let’s get all of the legal stuff out of the way up front. WE PROVIDE OPEN SOURCE, GPL CODE TO OUR READERS AT NO COST. ALWAYS HAVE. ALWAYS WILL. THE TRADEOFF IS YOU MUST AGREE TO ACCEPT ALL RISKS INHERENT IN USING THE SOFTWARE, WHETHER THOSE RISKS ARE KNOWN OR UNKNOWN TO YOU OR TO US. THE SOFTWARE IS PROVIDED "AS IS" AND MAY BE USED AS DELIVERED, OR YOU MAY MODIFY IT TO MEET YOUR OWN NEEDS SUBJECT TO THE TERMS OF THE GPL 2 LICENSE AVAILABLE HERE. IF YOU ARE UNWILLING TO AGREE TO THESE TERMS AND CONDITIONS, STOP READING HERE AND MOVE ON TO SOME OTHER WEB SITE. OTHERWISE, LET’S BEGIN WHAT WE PROMISE WILL BE A TERRIFIC ADVENTURE.
Overview of Facebook Messenger Webhooks Project
Here is a thumbnail sketch of what we’ll be covering today. Once you get an SSL certificate installed for your server, the remaining steps are a walk in the park. When we’re finished, you’ll have a Facebook Messenger platform that is seamlessly integrated with your PBX. The current software release supports Incredible PBX 13 with CentOS 6, Incredible PBX for Issabel, and Incredible PBX for Wazo. Minor tweaking required for other Asterisk platforms.
- SSL Certificate – Obtaining and installing an SSL certificate for your web server
- Security – Locking down your server for safe, secure Facebook Messenger access
- Incredible PBX Webhooks App – Installing the server-side webhooks software
- Facebook Integration – Interconnecting Facebook Messenger and Incredible PBX
- Outbound Call Setup – Configuring Incredible PBX to make outbound calls from FB
- Incoming Call Alerts – Configuring Incredible PBX for FB Messenger call alerts
- Webhooks Feature Set – Our tutorial covering all supported webhook commands
- SMS Messaging – Configuring Incredible PBX for SMS Messaging support with FB
- Webhooks Tips & Tricks – Adjusting our code to meet your own requirements
Obtaining and Installing an SSL Certificate
Believe it or not, the hardest part of today’s project was covered in last week’s Nerd Vittles tutorial. It walked you through obtaining and installing an SSL Certificate on any of the major Incredible PBX platforms. This gets your server configured to use secure and encrypted web communications via HTTPS which is both a Facebook requirement and a smart idea. There’s no need to read further until you get your server working properly with an SSL certificate because the Facebook integration component will fail until you get HTTPS access squared away. So start there and return here when you’re finished.
The Most Important Piece of the Puzzle: SECURITY
If you’ve been following Nerd Vittles over the years, you already know that our most important consideration with any PBX deployment is security. A PBX without a secure firewall is an invitation for an astronomical phone bill. Today’s setup assumes you already have deployed Incredible PBX with its Travelin’ Man 3 firewall that provides a whitelist of IP addresses that may access (or even see) your server. By definition, Facebook Messenger is a public platform available to everyone in the world. So how do we safely integrate it into your PBX while preserving the security of your server and its telecom resources? We do it in several ways. First, Facebook Messenger Webhooks are tied to a commercial Facebook page even though you don’t need a business in order to create the page. As the owner of that Facebook Page, you have to authorize users to access the page. DON’T! Make this a page that is solely dedicated to managing your PBX through Messenger. DO NOT USE THIS FACEBOOK PAGE AS THE PUBLIC FACE FOR YOUR BUSINESS! Also make certain that your Facebook credentials include a very secure password… as if the integrity of your PBX depended upon it. IT DOES! So long as you follow these guidelines, Facebook’s own security mechanisms will protect your PBX from intrusion. If this discussion makes you nervous, our last topic today will show you how to remove components from the code to eliminate any functionality you wish to turn off.
As configured, Facebook Messenger Webhooks won’t work at all with Incredible PBX because the firewall should block all web access to your server. This requires a change on the Incredible PBX for Wazo platform which we will cover momentarily. The way we will provide Facebook access is by adding the Facebook server IP addresses to the existing whitelist, and then we’ll run a bash script every night to keep the Facebook IP addresses current.
In the past, we opened TCP port 443 (HTTPS) to public access on the firewall with Incredible PBX for Wazo. Instead, we relied upon web server authentication for access to the Wazo, Telephone Reminders, and AsteriDex services. That needs to be changed before you interconnect with Facebook Messenger, and we’ll include that in the commands to whitelist the Facebook servers below.
1. To secure port 443 in your firewall, be sure that the port is not exposed in /etc/sysconfig/iptables (CentOS) or /etc/iptables/rules.v4 (Debian/Ubuntu/Raspbian). And then restart the Incredible PBX firewall.
sed -i 's|443|450|' /etc/sysconfig/iptables sed -i 's|443|450|' /etc/iptables/rules.v4 iptables-restart
2. Verify your new configuration: iptables -nL. Search for 443 and make certain it is NOT in the whitelist.
3. Verify that the whois package is installed on your server by issuing the command: whois. If you get a file not found error, install the package using the top line for CentOS and the bottom line for Debian/Ubuntu/Raspbian:
yum install whois apt-get install whois
4a. For Issabel and Incredible PBX 13, add to the end of /usr/local/sbin/iptables-restart these lines to whitelist the FB servers. Then restart the firewall: iptables-restart
whois -h whois.radb.net -- '-i origin AS32934' | grep ^route: | sed "s|route: |/usr/sbin/iptables -A INPUT -s |" | sed "s|$| -p tcp -m tcp --dport 443 -j ACCEPT|" > /usr/local/sbin/iptables-facebook chmod +x /usr/local/sbin/iptables-facebook /usr/local/sbin/iptables-facebook
4b. For Incredible PBX for Wazo, add to end of /usr/local/sbin/iptables-restart these lines to whitelist the FB servers. Then restart the firewall: iptables-restart
whois -h whois.radb.net -- '-i origin AS32934' | grep ^route: | sed "s|route: |/sbin/iptables -A INPUT -s |" | sed "s|$| -p tcp -m tcp --dport 443 -j ACCEPT|" > /usr/local/sbin/iptables-facebook chmod +x /usr/local/sbin/iptables-facebook /usr/local/sbin/iptables-facebook
5. Verify your new configuration: iptables -nL. You should see numerous whitelist entries for port 443 at the end of the listing.
6. Add the following command at the bottom of /etc/crontab to assure that the Facebook server IP addresses are kept current:
20 0 * * * root /usr/local/sbin/iptables-restart >/dev/null 2>&1
7a. For Issabel and Incredible PBX 13, create new web directory, set ownership/permissions to house the Facebook Messenger webhooks, and add a sample web page:
mkdir /var/www/html/fb echo "Hello World" > /var/www/html/fb/index2.php chown -R asterisk:asterisk /var/www/html/fb
7b. For Incredible PBX for Wazo, create web directory, set ownership/permissions to house the Facebook Messenger webhooks, and add a sample web page:
mkdir /var/www/html/fb echo "Hello World" > /var/www/html/fb/index2.php chown -R asterisk:www-data /var/www/html/fb chmod -R 775 /var/www/html/fb
8a. For Issabel and Incredible PBX 13, no further configuration is required.
8b. For Incredible PBX for Wazo, we need to enable access to the fb web directory. Edit /etc/nginx/locations/https-available/01_incrediblepbx:
At the top of the file, add the following:
location ~* ^/fb/. *\(?:ico|css|js|gif|jpe?g|png)${
root /var/www/html;
}
At the bottom of the file, add the following:
location ~ /fb/ {
root /var/www/html;
index index.php;
try_files $uri $uri/ =404;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fasstcgi_index index.php;
include fastcgi_params;
fastcgi_pass unix:/var/run/php5-fpm.sock;
}
Finally, restart the NGINX web server: service nginx restart
9. Using a browser, verify access to sample page: https://SERVER-FQDN/fb/index2.php
Installing Incredible PBX Webhooks Application
Now it’s time to install the Incredible PBX webhooks application on your PBX:
cd /var/www/html/fb wget http://incrediblepbx.com/incrediblewebhooks.tar.gz tar zxvf incrediblewebhooks.tar.gz rm incrediblewebhooks.tar.gz
For Issabel and Incredible PBX 13, adjust the file ownership and permissions like this:
chown -R asterisk:asterisk /var/www/html/fb chmod -R 775 /var/www/html/fb
For Incredible PBX for Wazo, adjust the file ownership and permissions like this:
chown -R asterisk:www-data /var/www/html/fb chmod -R 775 /var/www/html/fb
Hooking Up with Facebook
1. Visit the Facebook Developer’s Page and click Add a New App. Give your app a Display Name and provide your Contact Email. Match the letters in the box to get past the Security Check to display the Facebook Product List.
2. When the Facebook Product List appears, click Messenger and choose Setup.
3. In the Token Generation section, click Create a new Facebook Business Page to open a separate browser tab. Do NOT use a page that you use for other purposes! Company, Organization, or Institution is a good choice because there’s a Telecom Company category. Give your new page a Descriptive Name: incrediblepbx-podunk.
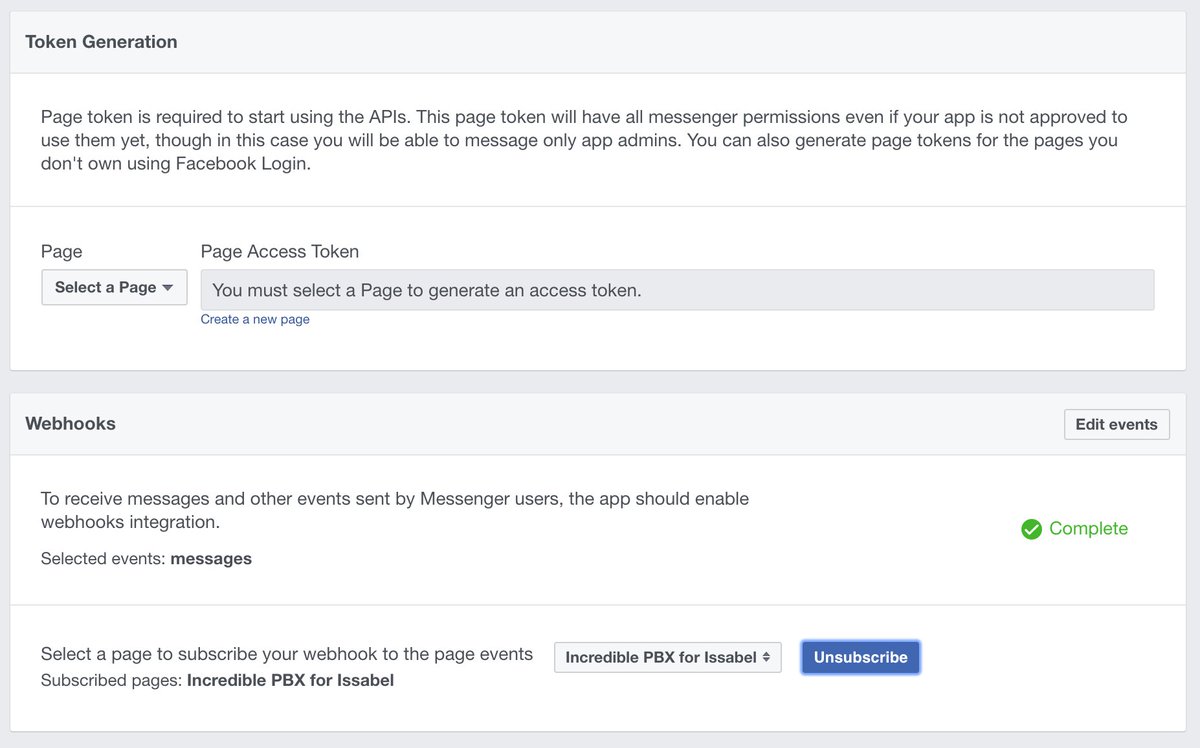
4. Return to your Token Generation browser tab and Select the Page you just created from the pull-down list (see Token Generation section of image below). Click Continue and OK to accept the default settings. Facebook then will generate a Page Access Token.
5. Copy the Page Access Token to your clipboard and paste it into the $access_token variable in the config.inc.php template in /var/www/html/fb. Write it down and keep it in a safe place. You’ll always need it to create new webhooks applications. This is the important link to talk to your Facebook Webhooks.
6. In the Webhooks section, click Setup Webhooks. In the Page Subscription form, enter the callback URL for your page. This is the https address to access your Facebook directory with a browser, e.g. https://YOUR-FQDN/fb. Make up a very secure Verify Token and enter it on the form and in the $verify_token variable in the config.inc.php template. This is the code Facebook will send to initially shake hands with your web page. The two entries must match to successfully set up your webhooks linkage. For Subscription Fields, check the Messages box. Then click Verify and Save. If it worked, you’ll get a Complete checkmark in the Webhooks section (see below). The last step is to again Select your Page in the Webhooks section to interconnect Facebook with your PBX. After choosing your page, be sure to click Subscribe or nothing will work. Here’s what a successful setup looks like:
7. To test things out, open Facebook Messenger on a desktop PC, Mac, or smartphone. Search Messenger for the Facebook page you linked to in the previous step. Then click on it to open it. Type howdy in the Message Box at the bottom of the dialog and click Send.
8. You should get an automated response that looks like this:
Hi there and welcome to BotWorld. SenderID: 13824822489535983
9. Copy the SenderID and paste it into cli-message.php together with Page Access Token from step #5, above.
Outbound Call Setup for Facebook Messenger
Outbound calling with Facebook Messenger works like this. You can connect to a specific number using the dial command. Or you can use the call command to look up an entry in your AsteriDex database. Messenger then will display the matching phone number and give you the option of placing the call. When the call is initiated, Incredible PBX will first call your designated CALL-PICKUP-NUMBER. It could be an extension or ring group of your choice. You could even specify a mobile phone number as the pickup destination provided your PBX supports at least two simultaneous outbound calls. Google Voice and many SIP providers can handle this with a single DID. Our personal preference is to route the pickup call to a trunk on a 3CX server which then sends the call to every 3CX client registered with the 3CX server. No NAT issues ever! Once you pick up the call on your designated phone, Incredible PBX will place the second call to the number you requested in Facebook Messenger. The two calls then are connected as if you had placed the call directly. The brief video below demonstrates how this works and the flexibility of using Acer’s $250 Chromebook Flip with Messenger and a 3CX client as a (free) WiFi-based web communications platform with Google Voice. It lets you place and take calls from anywhere in the world so long as you have Wi-Fi access. It’s a dirt cheap travel companion.
To make all of this work, you need to designate a phone in /var/www/html/fb/.cli-call to take outbound calls initiated from Facebook Messenger. This is either an extension number or a 10-digit CALL-PICKUP-NUMBER in the examples below. To set this up, edit .cli-call and choose one of the following examples. Comment out the other Channel options.
For Issabel and Incredible PBX 13, choose from the following:
#echo "Channel: SIP/701" > /tmp/cli.call #echo "Channel: SIP/vitel-outbound/1CALL-PICKUP-NUMBER" > /tmp/cli-call echo "Channel: Motif/gSOME-GV-NAMEgmailcom/1CALL-PICKUP-NUMBER@voice.google.com" > /tmp/cli.call
For Incredible PBX for Wazo, choose from the following:
echo "Channel: Local/701@default" > /tmp/cli.call #echo "Channel: Local/CALL-PICKUP-NUMBER@default" > /tmp/cli.call
Incoming Call Alerts with Facebook Messenger
If you’ve always wished for screenpops to announce your incoming calls, you’re going to drool at the FB Messenger Webhooks implementation with Incredible PBX. It works (simultaneously) on desktop PCs, Macs, iPhones/iPads, Android devices, and Apple Watch:
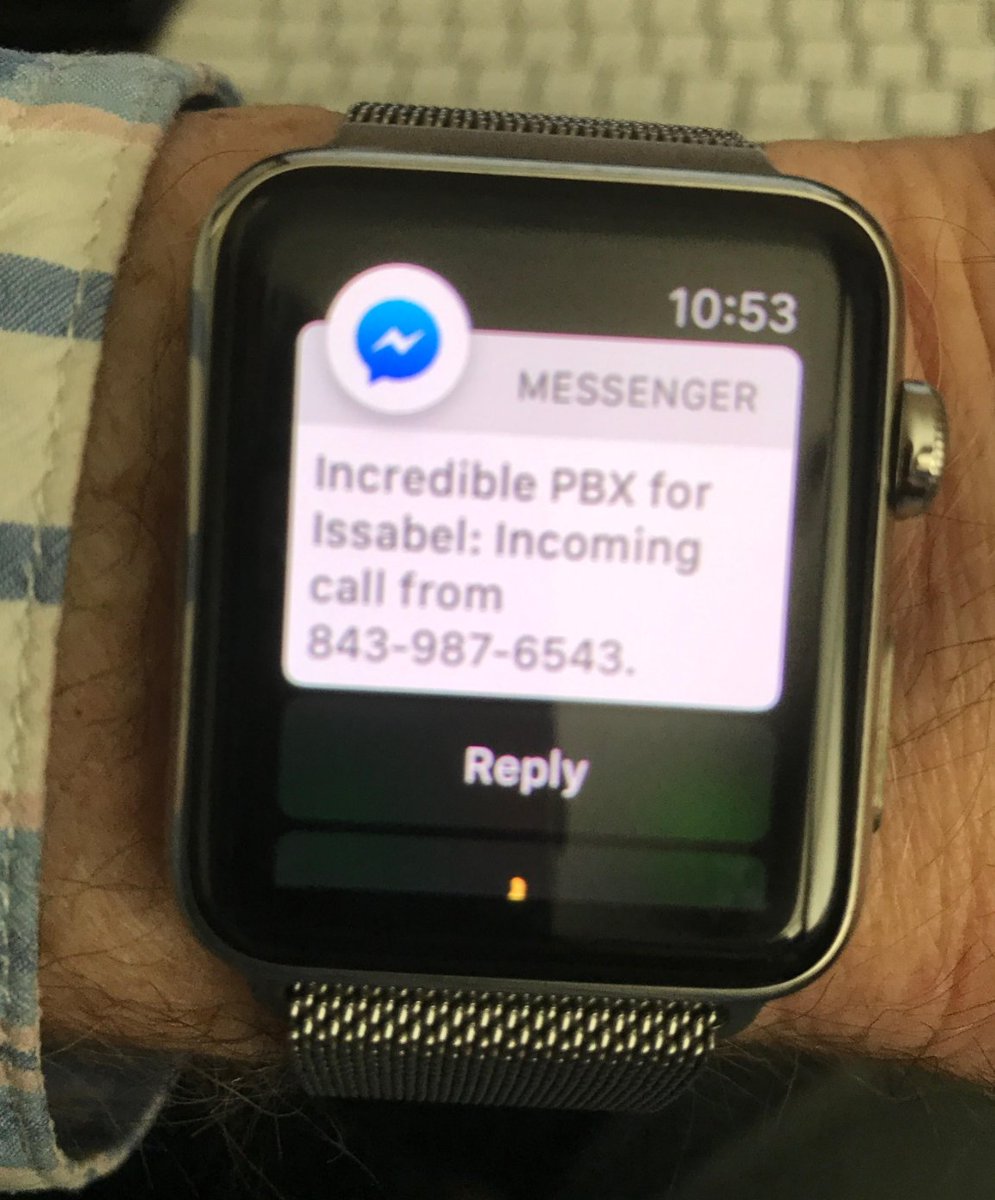
To set up incoming call alerts with Facebook Messenger, just issue the commands for your platform as outlined below.
For Incredible PBX 13, add the following to the end of extensions_override_freepbx.conf in /etc/asterisk directory. Then reload Asterisk dialplan: asterisk -rx "dialplan reload"
[cidlookup]
include => cidlookup-custom
exten => cidlookup_1,1,Set(CURLOPT(httptimeout)=7)
exten => cidlookup_1,n,Set(CALLERID(name)=${CURL(https://api.opencnam.com/v2/phone/${CALLERID(num)}?format=pbx&ref=freepbx)})
exten => cidlookup_1,n,Set(current_hour=${STRFTIME(,,%Y-%m-%d %H)})
exten => cidlookup_1,n,Set(last_query_hour=${DB(cidlookup/opencnam_last_query_hour)})
exten => cidlookup_1,n,Set(total_hourly_queries=${DB(cidlookup/opencnam_total_hourly_queries)})
exten => cidlookup_1,n,ExecIf($["${last_query_hour}" != "${current_hour}"]?Set(DB(cidlookup/opencnam_total_hourly_queries)=0))
exten => cidlookup_1,n,ExecIf($["${total_hourly_queries}" = ""]?Set(DB(cidlookup/opencnam_total_hourly_queries)=0))
exten => cidlookup_1,n,Set(DB(cidlookup/opencnam_total_hourly_queries)=${MATH(${DB(cidlookup/opencnam_total_hourly_queries)}+1,i)})
exten => cidlookup_1,n,ExecIf($[${DB(cidlookup/opencnam_total_hourly_queries)} >= 60]?System(${ASTVARLIBDIR}/bin/opencnam-alert.php))
exten => cidlookup_1,n,Set(DB(cidlookup/opencnam_last_query_hour)=${current_hour})
exten => cidlookup_1,n,System(/usr/bin/php /var/www/html/fb/cli-message.php "Incoming call: ${CALLERID(number)} - ${CALLERID(name)}.")
exten => cidlookup_1,n,Return()
exten => cidlookup_return,1,ExecIf($["${DB(cidname/${CALLERID(num)})}" != ""]?Set(CALLERID(name)=${DB(cidname/${CALLERID(num)})}))
exten => cidlookup_return,n,Return()
;--== end of [cidlookup] ==--;
For Incredible PBX for Issabel, add this to the end of extensions_override_issabel.conf in /etc/asterisk directory. Then reload Asterisk dialplan: asterisk -rx "dialplan reload"
[cidlookup]
include => cidlookup-custom
exten => cidlookup_5,1,Set(CURLOPT(httptimeout)=7)
exten => cidlookup_5,n,Set(CALLERID(name)=${CURL(https://api.opencnam.com/v2/phone/${CALLERID(num)}?format=pbx&ref=issabelpbx)})
exten => cidlookup_5,n,Set(current_hour=${STRFTIME(,,%Y-%m-%d %H)})
exten => cidlookup_5,n,Set(last_query_hour=${DB(cidlookup/opencnam_last_query_hour)})
exten => cidlookup_5,n,Set(total_hourly_queries=${DB(cidlookup/opencnam_total_hourly_queries)})
exten => cidlookup_5,n,ExecIf($["${last_query_hour}" != "${current_hour}"]?Set(DB(cidlookup/opencnam_total_hourly_queries)=0))
exten => cidlookup_5,n,ExecIf($["${total_hourly_queries}" = ""]?Set(DB(cidlookup/opencnam_total_hourly_queries)=0))
exten => cidlookup_5,n,Set(DB(cidlookup/opencnam_total_hourly_queries)=${MATH(${DB(cidlookup/opencnam_total_hourly_queries)}+1,i)})
exten => cidlookup_5,n,ExecIf($[${DB(cidlookup/opencnam_total_hourly_queries)} >= 60]?System(${ASTVARLIBDIR}/bin/opencnam-alert.php))
exten => cidlookup_5,n,Set(DB(cidlookup/opencnam_last_query_hour)=${current_hour})
exten => cidlookup_5,n,System(/usr/bin/php /var/www/html/fb/cli-message.php "Incoming call: ${CALLERID(number)} - ${CALLERID(name)}.")
exten => cidlookup_5,n,Return()
exten => cidlookup_return,1,ExecIf($["${DB(cidname/${CALLERID(num)})}" != ""]?Set(CALLERID(name)=${DB(cidname/${CALLERID(num)})}))
exten => cidlookup_return,n,Return()
;--== end of [cidlookup] ==--;
For Incredible PBX for Wazo, edit /etc/asterisk/extensions_extra.d/cid-superfecta.conf. In the [xivo-subrgbl-did] context just below the n(keepon),Gosub(cid-superfecta,s,1) line, insert the following. Then reload the Asterisk dialplan: asterisk -rx "dialplan reload"
same = n,System(/usr/bin/php /var/www/html/fb/cli-message.php "Incoming call: ${XIVO_SRCNUM} - ${CALLERID(name)}.")
Incredible PBX Webhooks Feature Set
Now that we’ve got all the pieces in place and properly configured, let’s briefly walk through the various options that are available. With all commands, you use Facebook Messenger with your designated web page on any platform supported by Messenger.
dial 8005551212 – connects to designated extension and then calls 8005551212
call Delta – looks up Delta in AsteriDex and provides button to place the call
lookup Delta – looks up Delta in AsteriDex and provides button to place the call
!command – executes a Linux command, e.g. !asterisk -rx "sip show registry"
howdy – returns greeting and SENDER ID of your FB page (Hookup, item #9)
help – provides links to phone help as well as PIAF and Asterisk forums
sms 10-digit-SMS-number "Some message" – sends SMS message through GV
update – updates Messenger platform for Incredible PBX to the latest & greatest
anything else – returns whatever you typed as a response (for now)
Configuring Incredible PBX for SMS Messaging
We’ve implemented a traditional SMS messaging function in this build that let’s you send an SMS message to any phone if you have a Google Voice account and assuming you have pygooglevoice functioning properly on your PBX. The Google Voice account need not be registered as a trunk on the PBX. To use the feature, insert your Google Voice credentials including your plain-text password for a working Google Voice account in /var/www/html/fb/.smssend. Then test the SMS functionality by issuing the following command from the Linux CLI:
/var/www/html/fb/.smssend 10-DIGIT-SMS-NUMBER "Hello SMS World"
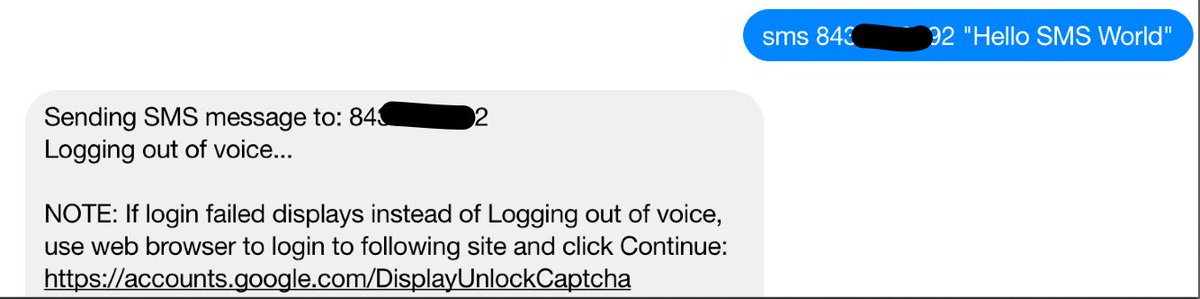
If an error occurs, the script will tell you what to try to fix it. Begin by Enabling Less Secure Apps. Then follow this link to relax Google Voice security on your account. If it still fails after trying both of these methods, you may have an old build of pygooglevoice. Here are the commands to bring your system up to current specs. Then try again.
cd /root rm -r pygooglevoice git clone https://github.com/wardmundy/pygooglevoice.git cd pygooglevoice python setup.py install cp -p bin/gvoice /usr/bin/.
Once you’ve sent an SMS message successfully using .smssend, you can start sending SMS messages from within Messenger. Syntax: sms 10-digit-SMS-number "Some message"
Incredible PBX Webhooks Tips & Tricks
There’s lots to learn with Facebook Messenger Webhooks. When we started two weeks ago, there were no PHP resources on the web that offered much help. Lucky for you, our pain is your gain. The meat of the coconut is primarily stored in the index.php in your fb directory. Print it out and it will tell you everything you ever wanted to know about coding webhooks with PHP.
Disabling Shell Access. While shell access only provides asterisk or www-data permissions depending upon your platform, we’ve nevertheless heard from more than one source exclaiming what a dumb idea it is to put a webhooks shell command out in the wild. We trust our readers to use it responsibly and to always place it behind a firewall with public access to TCP port 443 blocked. If that design and the Facebook security mechanisms still leave you queasy, the short answer is to remove that block of code on your server or change the access code from ! to something much more obscure, e.g. YuKFoo!. This is easy to do but just be aware that if you change the access code or even remove the block of code, running the update command to load the latest release from Incredible PBX Headquarters will overwrite your changes. So it’s probably a better idea to rename the update command (line 248) as well so you don’t accidentally run it. You’ll find the shell command block of code beginning at line 64 in the 170928 version. If you change the access code to a different string, remember to change the substring "1″ reference in that line and the subsequent line to the actual length of your access code, e.g. YukFoo! is seven characters long so the number 1 would be replaced with 7 in BOTH lines 64 and 65.
Other Security Measures. We don’t trust anybody (and that includes Facebook) when it comes to accessing resources from our paid VoIP providers. We would encourage you to run this application on a dedicated Incredible PBX in the Cloud server that has only a single Google Voice trunk with no funds balance in that particular Google account. In this way, if your server is compromised, the worst thing that can happen is your Google account gets compromised or some stranger makes U.S. and Canadian calls without financial cost to you. Now that Cloud servers are available for less than $2 a month, it makes good sense to separate out applications that pose heightened security issues for you and yours. If you do decide to use a SIP provider rather than a Google Voice trunk, we strongly recommend restricting international calls and keeping a minimal balance in your account with no automatic replenishment enabled.
Getting Rid of Lenny. The help command included in the feature set provided is more of a traditional web page with buttons simulating hot links. We’ve included a nifty telephone option in the help features. It let’s you embed a phone number that is called using client-side integration whenever help is entered and the "Talk to Lenny" option is clicked:
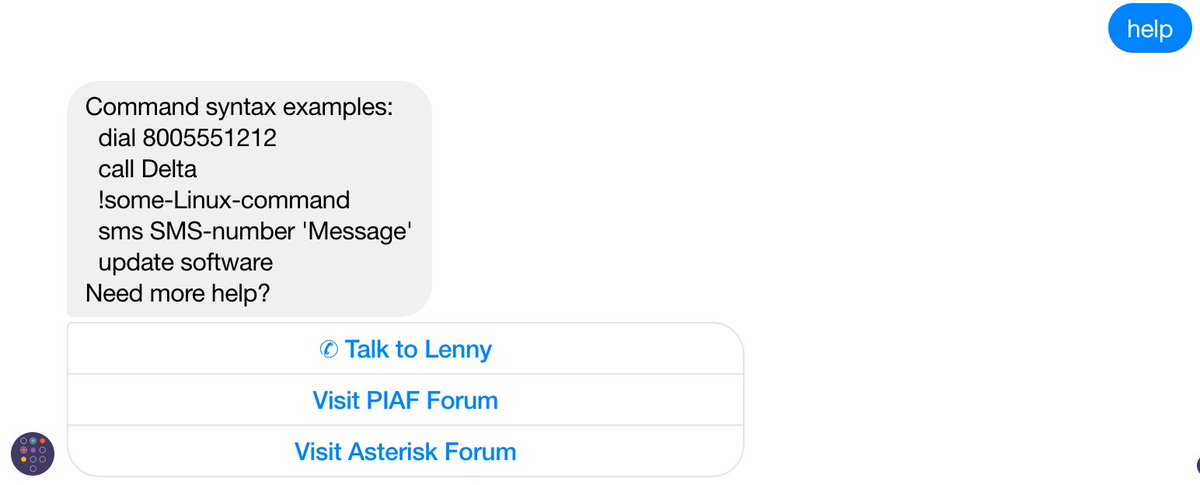
What client-side integration means is the calls use any dialer available on the Messenger client’s platform. They are not sent to your PBX for processing. On a Mac or iPhone, Facetime provides free calls. On Windows, Skype provides paid calls. On Android devices, the Google Hangouts Dialer provides free calls. Facebook basically passes tel: +18005551212 to the client’s browser, and it’s up to the client’s browser to figure out how to process the call. We currently have the feature configured to "Talk to Lenny," but you could change it to Phone Home or Call the Office and enter your own phone number. Here are the commands to do it. Just replace "Phone Home" in the first command below with whatever label desired. Replace "8005551212″ in the second line with the number to be called. Leave the other Lenny entry and phone number as they are since they will be overwritten by these two commands. As noted above, your modifications will be overwritten whenever you execute the update command.
sed -i 's|Talk to Lenny|Phone Home|' /var/www/html/fb/index.php sed -i 's|8436060444|8005551212|' /var/www/html/fb/index.php
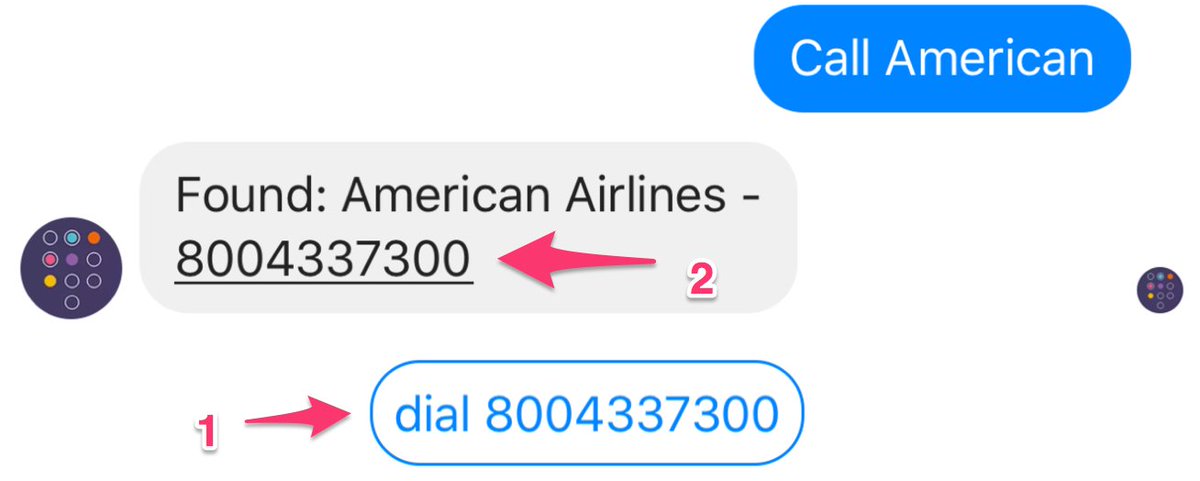
Enhanced Calling Option. Beginning with the October 1 update which you can obtain by entering the update command in Messenger, you now have two calling options on some smartphone platforms. The call command still triggers an AsteriDex lookup on your PBX. But now you have a choice in how to place the call. (1) You can click the dial button to place the outbound call through your PBX, or (2) you can click on the retrieved phone number link to place the outbound call using the client-side resource available on your Messenger platform, e.g. Facetime, Skype, or Google Hangouts. In some circumstances, the client-side call may be preferable since it avoids the two-step calling procedure used by Asterisk. The choice is yours and may depend upon the availability and cost of the client-side call when placed from your calling location.
Special Thanks. Our special hat tip to Scott T. Tabor (@ABSGINC) for his pioneering work on Facebook Webhooks. You can visit the PIAF Forum and Scott’s blog to review how far we have come in just two weeks. Thanks, Scott.
Published: Monday, October 2, 2017

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
VoIP Security: Installing SSL Certificates with Incredible PBX

We’ve got some revolutionary VoIP projects coming your way over the next several weeks, but I’m sorry to say the hardest part of them is getting your server configured to use secure and encrypted web communications via HTTPS. This is quickly becoming a universal requirement of most of the major technology players. So what might not be the most glamorous VoIP topic for a Monday morning is not only necessary but long overdue. The good news is that obtaining, installing, configuring, and maintaining an SSL certificate for your VoIP server is not the royal pain that it once was. And, by this time next week, you’ll be glad you went through the exercise. Thankfully, the EFF’s Certbot project is available to assist in installing free certificates from Let’s Encrypt.
Before we begin, here’s a word to the wise. You will save yourself a thousand headaches by deploying your Incredible PBX server in the cloud where you get a dedicated IP address and can easily assign a fully-qualified domain name (FQDN) to your server. Options now are available for as little as $1.50 to $3.50/month including Vultr which provides an incredibly reliable platform in many cities for as little as $2.50 a month. And another 50¢ buys you weekly image backups without lifting a finger. They can be restored with one click! If reliability and redundancy matter, you can’t beat Vultr’s price or the feature set, and we have tutorials to get you started with either Wazo or Issabel. If cost is your sole criteria, you can’t beat WootHosting at $1.50 a month. You’ll find a tutorial here. If performance is critical, you can’t beat OVH at $3.50/month with a Wazo tutorial here and an Issabel tutorial here. Finally, if you’re technically challenged, our corporate sponsor, RentPBX, will do all of the cloud migration for you and provide a turnkey, high performance VoIP platform for just $15/month. So what are you waiting for? Now’s the time. No excuses! It’s not going to get any cheaper or more reliable. And next week you’ll be thanking us. For these reasons, we’re saying goodbye our home-based servers sitting behind NAT-based firewalls. With the projects coming down the pike, the mountain is just too steep to continue that trek unless you have the technical expertise to pull it off yourself.
Obtaining and Installing an SSL Certificate
For CentOS 6 running Incredible PBX 13 or CentOS 7 running Incredible PBX for Issabel 4, begin by making certain that you can access your site using its FQDN with HTTP, e.g. http://myserver.mydomain.org. Get that working first. Next, log into your server as root using SSH/Putty and issue the following commands:
yum -y install python-devel python-pip python-setuptools python-virtualenv --enablerepo=epel yum -y install centos-release-scl yum -y install python27 scl enable python27 bash pip -V # should show python 2.7 pip install --upgrade pip pip install requests registry urllib3 pyOpenSSL --force --upgrade pip install certbot-apache --force --upgrade cd /root wget https://dl.eff.org/certbot-auto chmod a+x certbot-auto service iptables stop ./certbot-auto --authenticator webroot --installer apache -w /var/www/html -d FQDN.here iptables-restart service httpd restart exit
During the automated setup, you can decide whether to force all web traffic to the secure site. We recommend it. Once the install finishes, test access to your server by going to your FQDN using HTTPS. Don’t continue with the setup until you get HTTPS working and your browser shows you have a SECURE site! Remember that you must renew your free certificate every 90 days by using the following /root/certbot-update script:
#!/bin/bash echo "Before you begin, type: scl enable python27 bash" echo "Then rerun this update script and press ENTER." read -p "If you already have done so, press Enter. Otherwise, Ctrl-C now" service iptables stop ./certbot-auto --authenticator webroot --installer apache -w /var/www/html -d FQDN.here iptables-restart echo "Type exit when this script completes." exit
For Debian 8 running Incredible PBX for Wazo, things are a bit more complicated because Wazo forces HTTPS access even though you do not yet have a certificate for your FQDN. Because of its NGINX web server platform, with Wazo you’ll have to manually install and configure certificates with certbot and LetsEncrypt. The silver lining with Wazo is HTTPS access gets you a WebRTC phone with a couple button clicks. Go to this link, click on the Config wheel (bottom right), click on the Pencil icon and plug in the FQDN of your server. Click SAVE. Enter your login name as 701 and the password assigned to the extension which you can obtain by running: /root/show-701-pw. That’s probably the quickest phone setup you’ll ever find. But we’re getting ahead of ourselves…
1. Let’s get certbot installed. Login to your server as root using SSH or Putty and issue the following commands:
cd /etc/apt echo "deb http://ftp.debian.org/debian jessie-backports main" >> sources.list apt-get update apt-get install certbot -t jessie-backports
2. Temporarily, turn off HTTPS since the certificate install requires HTTP access. In /etc/nginx/sites-enabled/xivo, comment out these 3 lines and save the updated file:
In server section for port 80: # include /etc/nginx/locations/http-enabled/*; In server section for port 443: # listen 443 default_server; # server_name $domain;
Then restart the web server: /etc/init.d/nginx restart. Now you have a basic http web server. If you want to verify that it’s working, use a browser and go to http://YOUR-FQDN/asteridex4/index.php. It should download the file to your desktop which isn’t desirable, but this is only temporary.
3. In /var/www/html, issue the following commands:
cd /var/www/html mkdir .well-known cd .well-known mkdir acme-challenge cd acme-challenge chown -R asterisk:www-data /var/www/html/.well-known
Leave this SSH/Putty session running temporarily and open a second SSH/Putty connection to your server logging in as root.
4. Disable your firewall temporarily: /etc/init.d/netfilter-persistent flush
5. Start the certbot installation script: certbot certonly –manual
6. You’ll be prompted for the FQDN of your server to generate the certificates. Then you’ll be given an oddball name AND an expected oddball response. With these two entries in hand, temporarily switch back to your other SSH session and issue these commands while positioned in /var/www/html/.well-known/acme-challenge:
mkdir ODDBALL-NAME cd ODDBALL-NAME echo "ODDBALL-RESPONSE > index.html" chown -R asterisk:www-data /var/www/html/.well-known
7. Use a browser to (quickly) go to http://YOUR-FQDN/.well-known/acme-challenge/ODDBALL-NAME/ and be sure your web server displays the expected ODDBALL-RESPONSE. You’ve got to get this working before you continue with the certbot install or it will fail. You only have a few minutes to do this before certbot will change the ODDBALL-NAME and ODDBALL-RESPONSE credentials. 3 consecutive failures and you have to wait an hour to try again. Guess how we know?
8. Once you get the expected response, switch back to your SSH session running the certbot installer and press ENTER to continue with the certificate install. When it completes, you’ll get a congratulatory note and a reminder that, in less than 90 days, you’ll need to run certbot renew to update your certificate.
9. Install the new certificates in NGINX and put things back together again:
cd /etc/nginx/sites-enabled nano -w xivo
10. Begin by removing the 3 # signs that we inserted to get HTTP working in step #2.
11. Near the bottom of the file, comment out these existing certificate lines:
# ssl_certificate /usr/share/xivo-certs/server.crt; # ssl_certificate_key /usr/share/xivo-certs/server.key; # ssl_ciphers ALL:!aNULL:!eNULL:!LOW:!EXP:!RC4:!3DES:!SEED:+HIGH:+MEDIUM;
12. Add the following new lines just below the lines you commented out. Be sure to replace YOUR.FQDN in each line with the actual FQDN of your server:
ssl_certificate /etc/letsencrypt/live/YOUR.FQDN/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/YOUR.FQDN/privkey.pem;
ssl_ciphers HIGH:MEDIUM:!aNULL:!MD5:!SEED:!IDEA;
13. Save the file and then restart your firewall and NGINX:
iptables-restart /etc/init.d/nginx restart
14. Edit /etc/apt/sources.list and comment out the jessie-backports line from step #1.
15. Reload your aptitude sources: apt-get update
16. Remember that you must renew your free certificate every 90 days by issuing this command: certbot renew --quiet.
Better yet, issue the following command to set up a cron job to auto-renew your certificate every week:
echo "5 3 * * 0 root /usr/bin/certbot renew --quiet > /dev/null 2>&1" >> /etc/crontab
17. Test things out with a web browser by visiting your FQDN. Your browser should now show the site as SECURE.
18. Now try out that new WebRTC phone.
Published: Monday, September 25, 2017

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
Another Perfect Pair: Flawless VoIP with Wazo and 3CX

We previously documented how to interconnect an Issabel PBX with 3CX to take advantage of the best of both worlds. Today, we’ll again use the Nerd Vittles free 3CX server offering and interconnect it with a Wazo PBX. An added benefit of using Wazo is the fact that you can set up redundant (and free) HA servers with Wazo in minutes. Once we get the pieces in place, from Wazo extensions, you’ll be able to call your 3CX Clients by dialing 4 digits. And, from 3CX Clients, you can call Wazo extensions as well as all of your Asterisk® applications in the same way with the added bonus of being able to make outbound calls through your Wazo trunks by dialing any number with an 8 prefix from 3CX extensions. Once you have both of your PBXs running, the setup time to interconnect them is under 5 minutes.
Why would you want to maintain two PBXs? As we previously noted, the simple answer is the added flexibility you achieve coupled with a 99% reduction in VoIP headaches. If you haven’t yet used 3CX Clients on a PC or Mac desktop or on an iOS or Android device, you have missed perhaps the greatest VoIP advancement of the last decade. As the name suggests 3CX Clients connect to a 3CX server with less than a one-minute setup. They work flawlessly from anywhere using WiFi or cellular. Every function you’re accustomed to on a top-of-the-line desktop SIP phone works exactly the same on the 3CX clients: phonebook, hold, transfer, voicemail, chat, conferencing, and WebMeeting. It’s what every Unified Communications system should deliver. The silver lining is you can kiss all of your Asterisk NAT woes goodbye! If you ever travel or if you need remote phone access to your PBX infrastructure, you owe it to yourself to try a 3CX Client. We promise. You’ll never go back!
Building Your Wazo and 3CX Server Platforms
The prerequisite for interconnecting Wazo and 3CX servers is, of course, to install the two PBXs on platforms of your choice. Our preference is cloud-based servers because it avoids many of the stumbling blocks with NAT-based routers. If you know what you’re doing, you obviously can deploy the PBXs in any way you like. For the Wazo PBX, start with our latest Wazo tutorial. For 3CX, start with our introductory tutorial which includes a link to obtain a free perpetual license supporting 4 simultaneous calls and unlimited trunks. Then secure your server by adding the Travelin’ Man 3 firewall for 3CX. Once both servers are up and running, whitelist the IP address or FQDN of the Wazo PBX on the 3CX server and vice versa. You’ll find the add-ip and add-fqdn utilities in /root of each server.
Overview of Interconnection Methodology
If you’re new to all of this, suffice it to say that 3CX is a powerful, commercial PBX while Wazo provides a robust Asterisk RealTime implementation for basic telephony operation. The two systems are quite different in terms of their approaches to interconnectivity. While you can transparently interconnect one 3CX server to another one, you cannot accomplish the same thing when the second PBX is Asterisk-based. Instead, Wazo is configured as a SIP trunk on the 3CX platform. The limitation this causes is that extensions on the Wazo PBX can only direct dial extensions on the 3CX platform. Wazo-based extensions cannot utilize 3CX trunks to place outbound calls. There’s more flexibility on the 3CX side of things. 3CX extensions can place direct calls to Wazo extensions. They also can take advantage of Wazo’s trunks to place outbound calls. Additionally, as we noted above, 3CX extensions can take advantage of every Asterisk application hosted on the Wazo platform including all of the Incredible PBX® enhancements. This actually works out perfectly because you can deploy 3CX Clients for your end-users, and they can take advantage of all the extension and trunk resources on both the 3CX and Wazo platforms. It also greatly simplifies remote deployment by removing NAT one-way audio hassles while allowing almost instantaneous setup of remote 3CX Clients, even by end-users.
For our setup today, we’re assuming you have elected to use 3-digit extensions on both the Wazo and 3CX platforms. To call extensions connected directly to the alternate server, we will simply dial 8 + the extension number on the remote PBX. To make external calls from 3CX extensions using Wazo trunks, we will dial 8 + a 10-digit number. For international users, you can adjust the dialplan on both PBXs accordingly.
By default, SIP trunks are associated with a DID on the 3CX platform. We will register the 3CX DID trunk with Wazo to maintain connectivity; however, we will not register the corresponding trunk on the Wazo side with the 3CX server. Keep in mind that you can only route a 3CX DID to a single destination, i.e. an extension, a ring group, or an IVR. But we can use 3CX’s CallerID routing feature to send calls to specific 3CX extensions from Wazo extensions even using a single 3CX trunk. For each 3CX extension, we’ll create an Outbound Route on the Wazo side with a CallerID number that matches the 3CX extension number we wish to reach. On the 3CX side, we’ll create an Inbound CID Rule that specifies the extension number to which each matching CallerID number should be routed. This sounds harder than it actually is. So keep reading, and it’ll all make sense momentarily. Once you’ve set all of this up, we think you’ll agree that it makes sense to create the bulk of your extensions exclusively on the 3CX side.
Configuring Wazo for Interconnection to 3CX
Let’s begin by creating a Trunk on the Wazo side to connect to your 3CX server. In the Wazo GUI, choose IPBX:Trunk Management:SIP Protocol and + Add SIP Trunk.
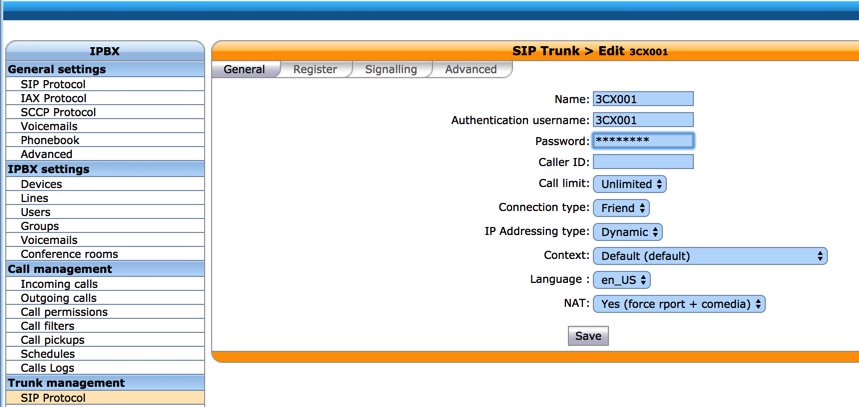
In the General tab, fill in the blanks as shown below. Make up a very secure Password:
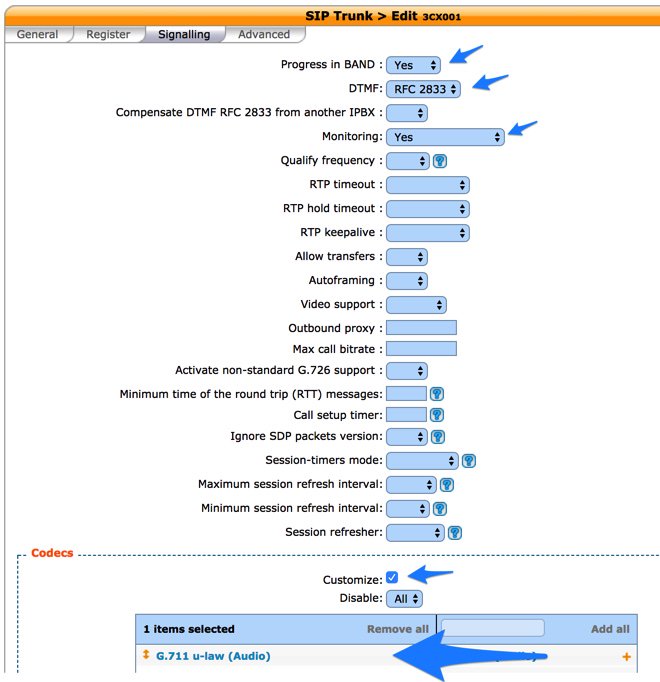
In the Signalling tab, fill in the blanks identified by arrows as shown below:
In the Advanced tab, fill in the blanks as shown below. Then SAVE the trunk settings.
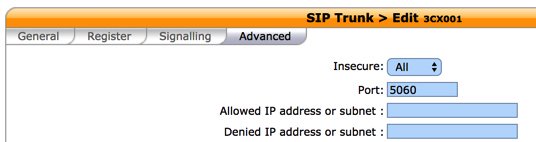
Because we set up the Wazo trunk with a Default destination context, we don’t need an Incoming Route for the 3CX calls since they will be processed exactly as if they were dialed from a local extension on the Wazo PBX, i.e. local calls will be routed to extensions and outgoing calls through trunks will be routed using your existing Outbound Routes.
Finally, we need to create the Outbound Routes for calls originating from Wazo extensions that should be directed to specific extensions on the 3CX platform. You’ll need a list of the 3CX extension numbers you wish to enable on the Wazo platform, and we’ll need to create a separate Outbound Route for each 3CX extension to be enabled. Create the Outbound Routes using the template below after accessing Call Management:Outgoing Calls:+ Add Route.
In the General tab, we recommend including the 3CX extension in the Name field. The Context should be Outcalls, and the Trunk should be the 3CX001 trunk we created above.
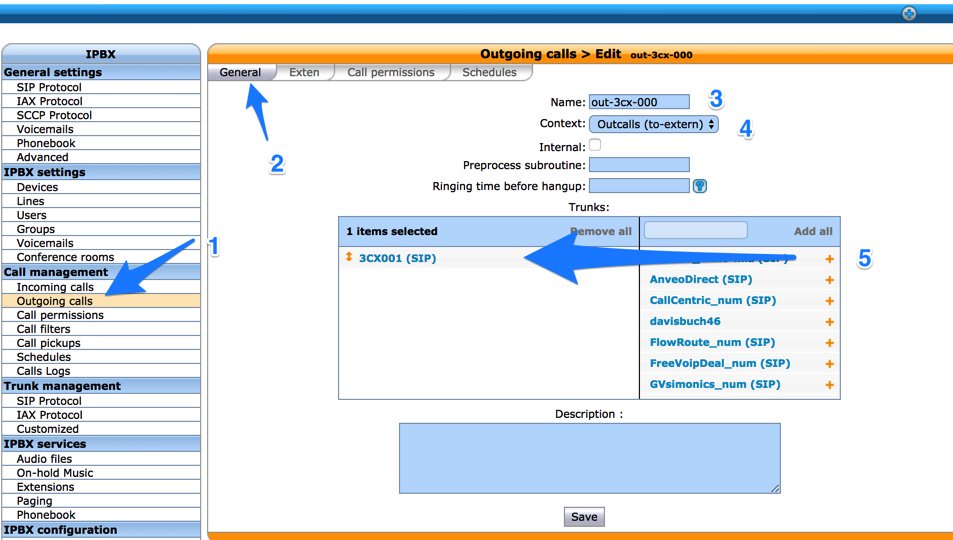
In the Exten tab, specify the dialing prefix (9) followed by the 3CX extension number in the Exten field. Then choose 1 in the Stripnum field to tell Wazo to strip off the dialing prefix before sending the call to the 3CX PBX. Click SAVE to save your new outbound route settings. Repeat for each 3CX extension that should be accessible from the Wazo PBX.
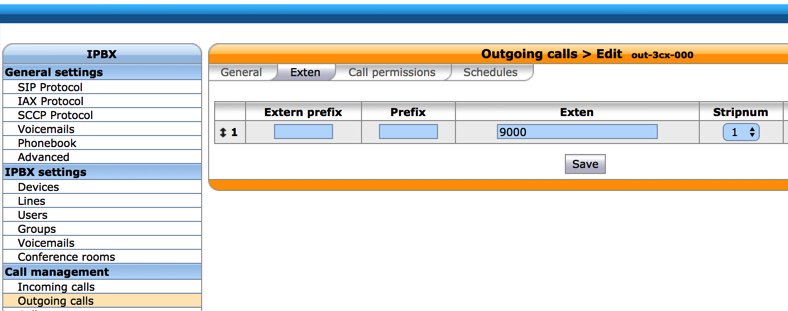
Configuring 3CX for Interconnection to Issabel PBX
Now we’re ready to set up the 3CX side to interconnect with your Wazo PBX. Start by creating a SIP Trunk and fill out the template as shown below using one of the phone numbers associated with your Wazo PBX as the Main Trunk No.
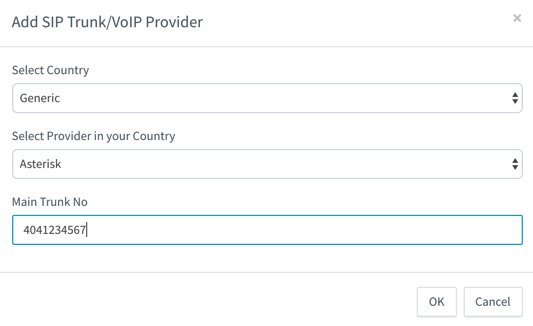
Fill in the Trunk Details using the example below. Be sure to specify the actual IP address or FQDN of your Wazo server as well as the SIP credentials of 3CX for username and the actual password you set up on the Wazo side of things. The Main Trunk No will be the same as you entered in the previous step. Choose a Default Destination for the Trunk.
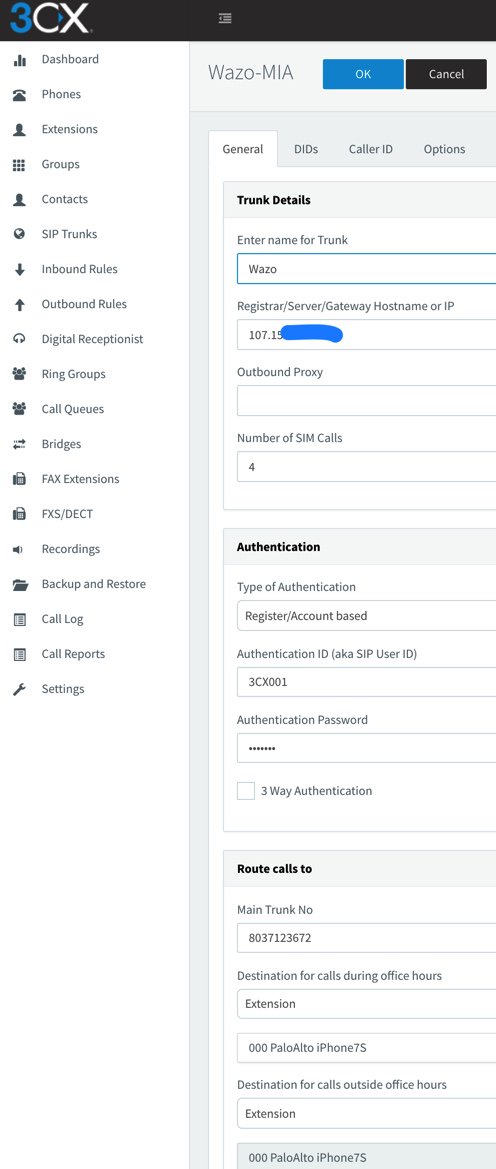
When the SIP Trunks listing redisplays, highlight your new Asterisk trunk and click Refresh Registration. The icon beside the Trunk should turn green. If not, be sure your IP address and password match the settings on the Wazo side. Remember to also whitelist the IP address of your 3CX server on the Wazo PBX using /root/add-ip and do the same for the Wazo PBX on the 3CX side. Don’t proceed until you get a green light!
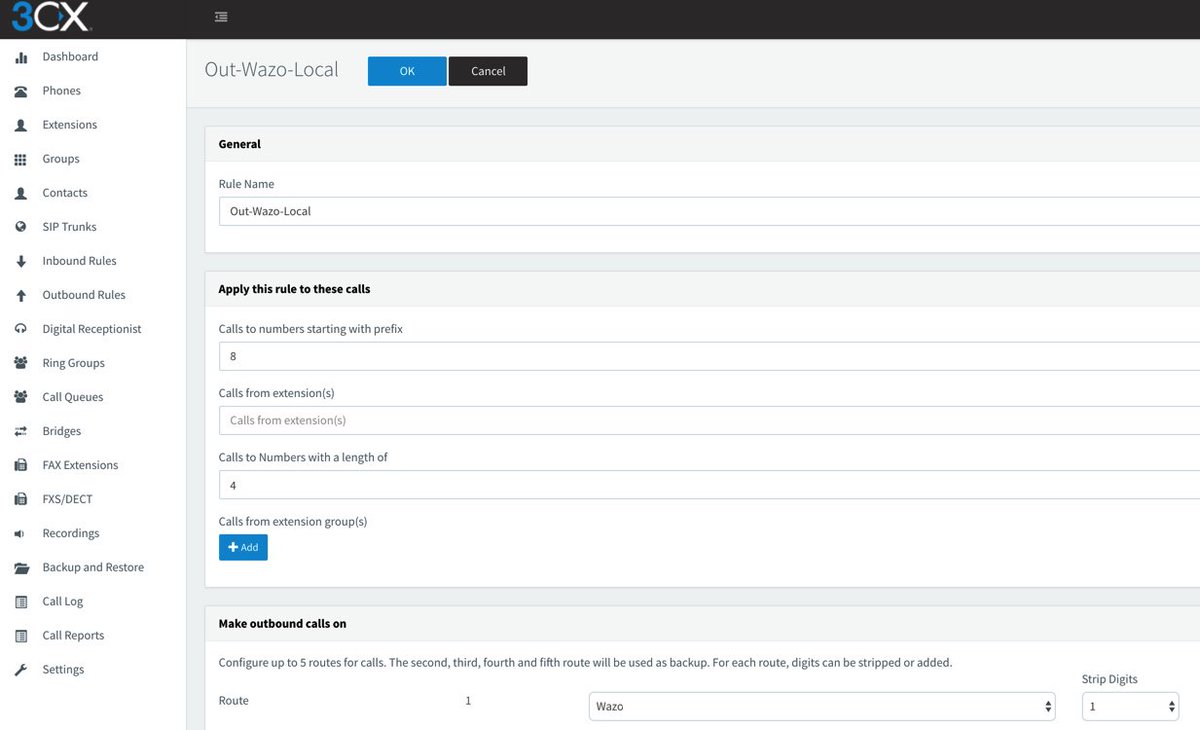
Now we need two Outbound Routes for calls placed from 3CX extensions. One will handle calls destined for Local Extensions on the Wazo side. Our design is to place calls to Wazo extensions by dialing 8 + the 3-digit extension number. Adjust this to meet your own requirements. Be sure to set the Route as Wazo with a value of 1 for Strip Digits.
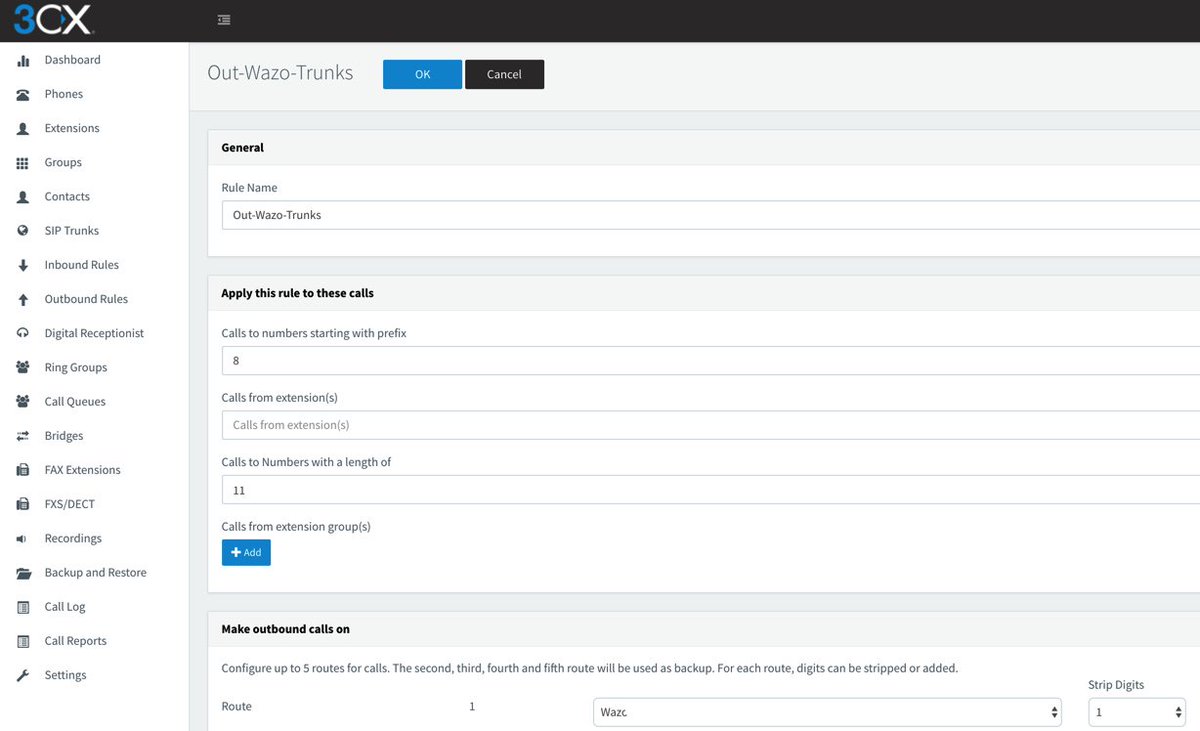
The other Outbound Route will handle calls destined for external calling with a Wazo trunk using a similar methodology. 3CX users will dial 8 + 10-digit number for calls to be processed by Trunks on the Wazo server.
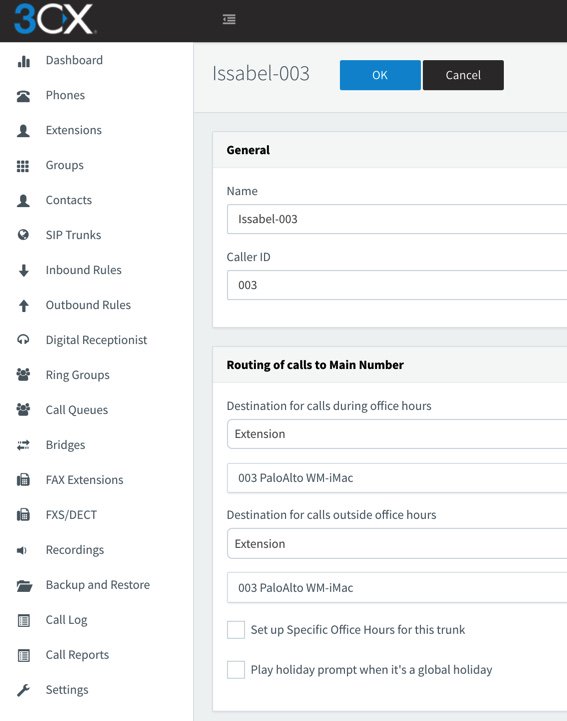
Finally, we need an Inbound Rule for every 3CX extension that you wish to enable for remote calling from Wazo extensions. Use the Add CID Rule option to create each Inbound Rule using the sample below. In our example, we’re authorizing incoming calls to 3CX extension 003 where the CallerID number of the incoming call is 003. This template is exactly the same as what we used with the 3CX-Issabel setup previously.
Test Drive Your Interconnected Servers
Now we’re ready to try things out. From an extension on the 3CX server, dial 8 plus any 3-digit extension that exists on the Wazo server. Next, dial 8 plus a 10-digit number such as your smartphone. The call should be routed out of your Wazo server using the Trunk associated with the NXXNXXXXXX rule in your Wazo Outbound Routes. Finally, from an extension on your Wazo PBX, dial 9 plus 000 which should route the call to extension 000 on your 3CX server. Enjoy!
Published: Tuesday, September 5, 2017
 Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.
Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
Best of the Internet: American Road Warrior’s Fall Roundup

The Internet is all about sharing the best finds and once a year we like to take a fresh look at what’s new and exciting whether you travel frequently or not. While the primary focus of Nerd Vittles is VoIP technology, you can’t provide the best VoIP solutions without also exploring network and cellular technology. And, as the old saying goes, all work and no play makes Jack a dull boy. When we travel for more than a day or two, we like to have a music and video source other than an iPhone. So let’s start there. And there’s plenty to love here even if you never leave the comfort of your living room.

For movies and TV shows, nothing holds a candle to a $10 subscription to Netflix. You can watch on your phone, or tablet, or PC, and someone else in your family can do the same thing at the same time. For $2 more, you can watch on four devices at a time. If you happen to have a rental unit, your renters will always remember you for the free Netflix subscription. Our second place alternative is primarily for cord cutters. DirecTV Now is just $10/month if you happen to have an AT&T Unlimited Data Plan (regularly $35). That gets you 60+ live channels and 20,000 on demand titles. For an extra $5, you can add HBO. With a two-month prepayment, you can snag a free Roku Premier until September 22, 2017. DirecTV Now also aupports streaming to two simultaneous devices, and a 100-hour DVR is just around the corner.

For cellular service, we’ve never been big fans of corporate tying. Believe it or not, there was a time when most thought it was illegal. But there’s a loophole. So long as you’re not forced to buy the unrelated product, it’s not technically a tying violation. And that’s where we find ourselves today with American oligopolies. You’d be crazy not to take advantage of the opportunities especially since AT&T bought DirecTV. An AT&T unlimited data plan for your cellular service unlocks all sorts of goodies with DirecTV. We’ve mentioned the $25 monthly credit with DirecTV Now. But it’s also available with standard DirecTV subscriptions. And you get HBO and NFL Sunday Ticket at no charge as well. With four devices including a Wi-Fi HotSpot, our cellular plan with AT&T costs under $50/month per device including taxes and fees. It provides unlimited talk, text, and data in the U.S., Canada, Mexico, Puerto Rico, and the U.S. Virgin Islands. The 22GB data throttling gotcha doesn’t apply in many locations including our hometown of Charleston, SC. We racked up 90GB of data usage on the hotspot during our last 8-day vacation. Never a hiccup! Whether you’re in a car, a hotel room, or on a cruise ship, the $59 AT&T Velocity 4G LTE HotSpot is a perfect traveling companion supporting 10 device connections for up to 10 hours.

For international cellular data service, there’s a terrific new option that provides unlimited 4G data service in 100+ countries for $9 per day. This compares favorably with AT&T’s outrageous cruise ship offering of $8.19 per megabyte of data traffic. You can purchase the Skyroam Solis device for $150 on Amazon, or you can rent one in major airports. It supports 5 devices at a time. We can’t give you a first-hand report on the Solis because it was just released this week. But we have ordered one and will provide a Grand Turk update soon. ↙

For music services, Spotify Premium remains the gold standard. $10 a month buys you unlimited streaming of almost every song ever published. $5 more gets you a family plan to support 5 people. For qualifying college students, Spotify Premium is just $5 a month. You can even download the songs to your smartphone or tablet and play them when you don’t have Internet connectivity. For extended vacations, we discovered a new boom box this summer that is worth a careful look. It combines an Android tablet with some terrific speakers to provide 12 hours of non-stop music from your favorite sources including Spotify. It also can access the best radio stations throughout the United States using the iHeartRadio app. And it even includes 8GB of internal storage as well as microSD and USB flash drive support. The Sonicgrace will set you back $190 on Amazon (MSRP: $299.99).

For music junkies, it’s worth noting that the only application that routinely crashed Android unfortunately was TuneIn Radio. For neophytes, TuneIn is the must-have app that provides streaming of virtually every commercial radio station in the world. Here’s the quick fix. We suspected that the problem involved the latest release of TuneIn which you would automatically receive using Google’s Play Store as the download source as Sonicgrace does. So the solution would be to install a prior release. Here’s how. On a desktop PC, download an earlier TuneIn APK from here. We chose 13.7 which happened to work. Next, use Gmail to send yourself a message with this 13.7.apk file as an attachment. Then, on the Sonicgrace, first install Gmail from the Play Store tapping My +:App:PlayStore. Open the Gmail app once the install finishes and then open the email message you sent yourself. Tap on the attachment, and TuneIn will automatically be installed.
For VoIP telephony, here’s another nice surprise. Google’s Amazon Echo Killer, aka Google Home, has a new feature. It can make free calls in the United States and Canada to anyone in your Google Contacts as well as any business you can find with a Google Search. Here’s the best deal we could find if you don’t already own Google Home. It’s also available at Target and WalMart for about $25 more plus tax. And here’s how to start making calls.
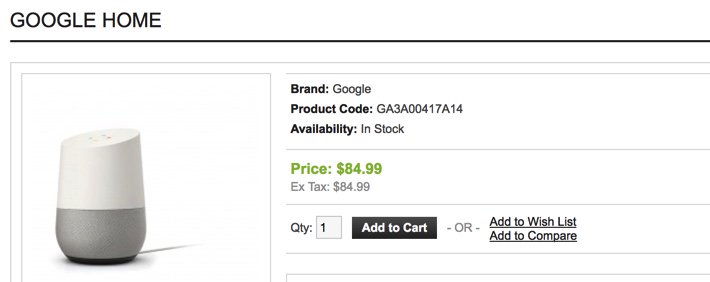
Published: Friday, September 1, 2017

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
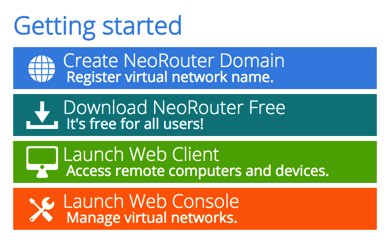
A VPN for All Seasons: Introducing NeoRouter v2

Today, we want to revisit our favorite client-server VPN, NeoRouter. It’s included with all versions of Incredible PBX® and eases the pain of setting up air-tight firewalls as well as High Availability (HA) redundant servers with VoIP. NeoRouter relies upon a central server and uses a star topology to connect remote nodes. The major difference between NeoRouter and PPTP VPNs is that only registered devices participate in the virtual private network so there is no direct access to other machines on the LANs of the registered devices. If you have servers or users scattered all over the countryside, NeoRouter is an excellent (and free) way to manage and interconnect them. All data and communications between the nodes can then be routed through the encrypted VPN tunnel for rock-solid security.

With NeoRouter’s latest 2.3 (free) software, you can set up your VPN server using a PC, a Mac, a Linux or FreeBSD machine, OpenWrt Backfire, Tomato, or even a Raspberry Pi. With all versions of Incredible PBX, the NeoRouter Free Client is automatically installed. To bring up NeoRouter, all you need to do is install the NeoRouter Free Server on one of your machines and then login to the server from each NeoRouter Client using your server credentials. VPN clients also are available for PCs, Macs, Linux and FreeBSD machines, Raspberry Pi, OpenWrt, Tomato as well as Android and iOS phones and tablets. There’s even an HTML5 web application in addition to a Chrome browser plug-in. With the OpenWrt and Tomato devices or if you’re an extreme techie, you can broaden your NeoRouter star configuration and bridge remote LANs. See pp. 58-63 of the NeoRouter User’s Manual.
You can interconnect up to 256 devices to the NeoRouter Free Server at no cost. For $999, you can enlarge your VPN to support 1,000 devices. Screen sharing, remote desktop connections, HTTP, and SSH access all work transparently using private IP addresses of the VPN nodes which are automatically assigned in the 10.0.0.0 private network.
Today we are introducing the second generation of the NeoRouter VPN solution. It’s suitable for use on a dedicated server or running as a virtual machine. Whether to run NeoRouter Free server on a dedicated machine is your call. We never do. And NeoRouter never requires exposure of your entire server to the Internet. Only a single TCP port needs to be opened in your hardware-based firewall or IPtables Linux firewall. The only real requirement is a dedicated IP address for your server so that the client nodes can always find the mothership. We typically run the NeoRouter server component on our failover VoIP server with Wazo HA. We’ll finish up today by showing you how to back up the critical components of NeoRouter Server so that, if your server platform ever should fail, it only takes a few minutes to get back in business on a new server platform. Let’s get started.
Creating Your NeoRouter Server Platform
We’re assuming you already have an Incredible PBX server of some flavor running on a dedicated IP address with the IPtables firewall. If not, start there.
First, on your IPtables firewall, make certain that TCP port 32976 has been whitelisted for public access. On Incredible PBX platforms, this is automatic. You can double-check by running iptables -nL and searching for an entry that looks like this:
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:32976
Second, we need to download and install the NeoRouter Free Server for your platform. Be sure you choose the version that matches your operating system, CPU architecture, and type. Debian and Ubuntu servers use the same code. We do not recommend Raspberry Pi as a suitable platform for your NeoRouter server!
For RedHat/CentOS 64-bit platforms, here’s the download link. While logged into your server as root, issue the following command using the downloaded 64-bit RPM:
rpm -Uvh nrserver-2.3.1.4360-free-centos-x86_64.rpm
For Ubuntu/Debian 64-bit platforms, use this link. While logged into your server as root, issue the following command using the downloaded 64-bit .deb image:
dpkg -i nrserver-2.3.1.4360-free-ubuntu-amd64.deb
Third, each administrator (admin) and user is going to need a username to access your NeoRouter VPN. You can use the same credentials to log in from multiple client machines, something you may or may not want to do. Here are the commands to create admin and user accounts. Don’t use any special characters in the username and password!
nrserver -adduser username password admin
nrserver -adduser username password user
You’re done. Now let’s register your NeoRouter server with the mothership.
After your NeoRouter Free Server is installed, you can optionally go to the NeoRouter web site and register your new VPN by clicking Create Standalone Domain. Make up a name you can easily remember with no periods or spaces. You’ll be prompted for the IP address of your server in the second screen. FQDNs are NOT permitted.
When a VPN client attempts to login to your server, the server address is always checked against this NeoRouter database first before any attempt is made to resolve an IP address or FQDN using DNS. If no matching entry is found, it will register directly to your server using a DNS lookup of the FQDN. Whether to register your VPN is totally up to you. Logins obviously occur quicker using this registered VPN name, but logins won’t happen at all if your server’s dynamic IP address changes and you’ve hard-coded a different IP address into your registration at neorouter.com.
Configuring and Connecting Your NeoRouter Client
As mentioned previously, there are NeoRouter clients available for almost every platform imaginable, including iPhones, iPads, and our beloved Raspberry Pi. NeoRouter Client software is included in all Incredible PBX builds. If you’re using some other platform, Step #1 is to download whatever client is appropriate to meet your requirements. Here’s the NeoRouter Download Link. Make sure you choose a client for the Free version of NeoRouter. Obviously, the computing platform needs to match your client device. The clients can be installed in the traditional way with Windows machines, Macs, etc. Once enabled, you can use your NeoRouter Client to create a VPN tunnel to connect to any other resource in your virtual private network using SSH, VoIP clients, and web browsers.
To activate the NeoRouter client while logged in as root, type: nrclientcmd. You’ll be prompted for your Domain, Username, and Password. You can use the registered domain name from neorouter.com if you completed that step above. Otherwise, be sure to use the FQDN assigned to your NeoRouter Server. Once you’re logged in, you will be presented with the names and private IP addresses of all of your connected nodes.
To exit from NeoRouter Explorer, type: quit. The NeoRouter client will continue to run so you can use the displayed private IP addresses to connect to any other online devices in your NeoRouter VPN. All traffic from connections to devices in the 10.0.0.0 network will flow through NeoRouter’s encrypted VPN tunnel. This includes inter-office SIP and IAX communications between Asterisk® endpoints. These private IP addresses can also be used to create a High Availability (HA) platform with Wazo even if the servers are not colocated.
Admininistrative Tools to Manage NeoRouter
Here are a few helpful commands for monitoring and managing your NeoRouter VPN.
Browser access to NeoRouter Configuration Explorer (requires user with Admin privileges)
Browser access to NeoRouter Remote Access Client (user with Admin or User privileges)
Manage your account on line at this link
To access your NeoRouter Linux client: nrclientcmd
To restart NeoRouter Linux client: /etc/rc.d/init.d/nrservice.sh restart
To restart NeoRouter Linux server: /etc/rc.d/init.d/nrserver.sh restart
To set domain: nrserver -setdomain YOUR-VPN-NAME domainpassword
For a list of client devices: nrserver -showcomputers
For a list of existing user accounts: nrserver -showusers
For the settings of your NeoRouter VPN: nrserver -showsettings
To add a user account: nrserver -adduser username password user
To add admin account: nrserver -adduser username password admin
Test VPN access: http://www.neorouter.com/checkport.php
For a complete list of commands: nrserver –help
To change client name from default pbx.local: rename-server OR…
- Edit /etc/hosts
- Edit /etc/sysconfig/network
- Edit /etc/sysconfig/network-scripts/ifcfg-eth0
- Edit /etc/asterisk/vm_general.inc
- reboot
For the latest NeoRouter happenings, visit the NeoRouter blog and forum.
Backing Up NeoRouter Server for That Rainy Day
Yes, servers fail sooner or later. So it’s best to plan ahead and avoid having to recreate your NeoRouter VPN from scratch. Backing up your server is easy. Log into your server as root and issue the following command:
tar cvzf nr-server-db.tar.gz /usr/local/ZebraNetworkSystems/NeoRouter/NeoRouter_0_0_1.db /usr/local/ZebraNetworkSystems/NeoRouter/Feature.ini
Copy nr-server-db.tar.gz and your NeoRouter Server installer to a safe place!
When that sad day arrives, be sure that your original NeoRouter Server is off line. Then reinstall NeoRouter Server on a new server platform using your original NeoRouter Server installer. If necessary, change the DNS entry for your original NeoRouter server to the new IP address. Then shut down new NeoRouter Server, load your backup, and restart server:
/etc/rc.d/init.d/nrserver.sh stop cd / tar zxvf nr-server-db.tar.gz /etc/rc.d/init.d/nrserver.sh start
Published: Monday, August 21, 2017

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
3CX in the Cloud: 8 Great Ways to Secure Your Server

Now that many of you have taken advantage of the opportunity to deploy a free 3CX server, it seemed like an opportune time to share what we’ve learned while deploying 3CX on hosted platforms in the cloud. If you’ve followed our Nerd Vittles adventures over the years, you already know that our number one consideration with any PBX deployment is security. Without that, you’re just paying somebody else’s phone bill. While 3CX is extremely secure as delivered, once you choose a cloud-based platform, it’s a new ballgame. There is no 3CX firewall sitting between your PBX and the Internet.
We hear some of you saying, "I love Asterisk. Why would I want to move to 3CX?" The short answer is don’t move, add a new 3CX server to supplement your existing Asterisk® infrastructure. Why? Because the 3CX Clients for Windows, Macs, iOS, and Android are incredibly compelling. You can make a connection from anywhere using WiFi or cellular infrastructure and make crystal clear calls with zero hassles. Better yet, folks can reach you on your mobile phone from anywhere in the world at zero cost by dialing your SIP URI using any SIP device including SIP softphones and other 3CX Clients. And the 3CX Client is literally plug-and-play. Send the welcome email for the extension you wish to activate on the 3CX Client, and in one-click your 3CX Client is automatically configured and on line. By interconnecting your 3CX server with your existing Asterisk infrastructure, you get the best of both worlds without the messy NAT and firewall problems that were daily fare using Asterisk alone. But we’re getting ahead of ourselves, let’s get your 3CX server in the Cloud properly secured before moving on to the fun stuff.
Five years ago, we first introduced our Failsafe PBX Security Tips to Sleep Like a Baby. That’s well worth a careful read before we begin. For today, we’ll be implementing most of the Travelin’ Man 3 Security Model with a few tweaks to take advantage of existing 3CX security features. We’ll walk you through (1) choosing a cloud platform, (2) deploying the IPtables Linux firewall, (3) implementing a WhiteList to hide your server from those that don’t need access, (4) installing PortKnocker to make it easy for end-users to give themselves access to your PBX, (5) configuring FQDNs and implementing dynamic DNS updates for remote users, (6) setting up a BlackList to complement 3CX’s existing Anti-Hacking mechanisms, (7) deploying IPset to facilitate blocking entire countries from accessing your server, and (8) protecting SSH by setting up Fail2Ban and changing ports.
Let’s spend a moment considering the best security methodology for your cloud-based server. The short answer is IT DEPENDS. If all of your users are situated in the same location and never travel and you don’t care to enable SIP URI calling from anywhere in the world to save on phone costs, then the solution is pretty easy. We can lock your server down to the public IP address of your private LAN, and nobody else will ever see your server. Once you add users outside your home office, things get more complicated. If they are all sitting behind local routers with public IP addresses that are static, things are still fairly straightforward. We can whitelist all of the static IP addresses, and again nobody else will see your 3CX server. If you have users that travel for a living or need 3CX Client connectivity from their smartphones or from PCs at various locations that only have dynamic IP addresses, then things get more complicated. You can take your chances and expose SIP communications ports while locking down other access, or you can lock down everything, assign FQDNs to each user, and use dynamic DNS clients running on Android or iOS devices or local PCs to regularly update IP addresses of users in the firewall whitelist.
Another option that we use when traveling is PortKnocker which will be installed as part of our Travelin’ Man 3 security suite. The way this works is you send a single packet to three different TCP ports on your server using a predefined sequence of 3 port numbers. When there is a match, the server will automatically whitelist your IP address. Then you can log into SSH or the Web portal or use a 3CX Client in the usual way. There are PortKnocker clients for smartphones (Android’s DroidKnocker and iOS PortKnock), or you can use the command line from a Linux server to immediately authorize remote access from any IP address. No firewall modification is required. By default, Travelin’ Man 3 temporarily authorizes IP address access until the next server reboot. But you can elect to permanently whitelist the IP addresses if desired. Again, all of this can be performed remotely by end-users without ever touching your server or calling upon assistance from an administrator.
Finally, we’ve provided utilities in /root to assist an administrator in whitelisting IP addresses (add-ip) or FQDNs (add-fqdn) as well as removing whitelisted entries (del-acct). In addition, if you prefer to leave your server exposed, we’ve included tools to blacklist IP addresses (add-blacklist), and our discussion below will provide some alternatives to secure SSH access. Whichever path you choose, just be aware that server security it totally your responsibility, not ours and not 3CX’s. We strongly recommend that you regularly monitor the Event Log in the 3CX Dashboard for security issues and attempted breaches. You then can make firewall adjustments to address the problems or to further lock down your server.
LEGAL DISCLAIMER: ALL OF THE SECURITY CODE WHICH FOLLOWS IS DISTRIBUTED AS IS AND PURSUANT TO THE GPL2 LICENSE. YOU AGREE TO ASSUME ALL RISKS BY USING THIS SOFTWARE. YOU ARE FREE TO MODIFY IT TO MEET YOUR REQUIREMENTS SO LONG AS YOU COMPLY WITH THE GPL LICENSE TERMS AVAILABLE HERE.
For today’s tutorial, we will cover both the WhiteList 3CX firewall methodology and the less secure BlackList alternative. We’ll walk you through exposing the necessary ports if you elect to use this relaxed security configuration for your server. Just be aware that it’s your phone bill at stake particularly if you have authorized calls to countries outside the location of your server as part of your 3CX setup.
1. Choosing a 3CX Cloud Platform
Here are a few things to consider when choosing a cloud platform for your 3CX server. Keep in mind that the cloud giants like Amazon charge for data bandwidth usage AND data storage AND processing cycles. Even though Amazon uses what are traditionally considered non-routable IP addresses internally, be advised that Amazon internally routes these private LAN addresses. What that means is that, if you have whitelisted private LAN addresses in the 172.16.0.0/12 range, you will expose your server to hacking attempts from anyone with an Amazon S3 account. For that reason coupled with the pricing structure, we recommend against using Amazon as your 3CX cloud platform.
We also recommend you stick with VPS hosting plans using the KVM architecture and avoid OpenVZ unless it’s hosted with Virtuozzo 7. The traditional shared kernel architecture of OpenVZ means you will forfeit the ability to use powerful tools such as IPset to blacklist country-wide IP addresses from countries such as China and Russia. Over 90% of the attacks we see on our web sites originate from IP addresses in just those two countries. Fortunately, the new Virtuozzo 7 implementations of OpenVZ support ipset. SSDnodes in Montreal is the provider we use.
The rest of the cloud platform equation comes down to balancing the feature set and performance against the cost. At the bottom of the barrel is CloudAtCost which offers lifetime cloud services for a one-time charge PLUS an annual maintenance charge. Performance and reliability range from awful to tolerable. As an experimental platform, it’s worth considering. For anything beyond that, don’t waste your time or money.
Our preferences in low-cost, moderate performance cloud platforms include OVH virtual private servers ($3.49/mo. for 2GB RAM, 10GB SSD, 100Mbps unlimited bandwidth, and DDoS protection), Vultr VPS ($5/mo. for 1GB RAM, 25GB SSD, 1TB bandwidth), and Digital Ocean ($5/mo. for 512MB RAM, 20GB SSD, 1TB bandwidth plus $10 usage credit). For high performance, long-term use, nobody beats our corporate sponsor, RentPBX.com, at $15/mo. with referral code: NOGOTCHAS.1
2. Deploying the IPtables Linux Firewall
We’ve taken the pain out of deploying IPtables as a 3CX firewall. Our Travelin’ Man 3 script for 3CX does the heavy lifting for you by installing and preconfiguring IPtables and a collection of other security components. There are two alternatives when running the installer. You can completely lock down your server and use a firewall whitelist to enable access from specified IP addresses or FQDNs. There are utilities to allow administrators and end-users to add their own addresses to the whitelist. The other option is to run 3CX without the whitelist functionality and employ blacklisting to reduce the exposure of your server. This obviously increases the security risks but reduces the administrative burden on administrators and end-users. And, as you probably know, 3CX includes some security mechanisms to block or reduce attacks on your server. A third option using 3CX Clients or SBCs in networks that prevent VoIP calls is to deploy 3CX’s VPN-like Tunnel. This is well documented in this server tutorial and this client tutorial. It’s worth a careful look if you’re in a country that blocks VoIP calls, and it works with either TM3 firewall configuration. A fourth option which we will save for another day is to employ virtual private networks such as OpenVPN and NeoRouter. With VPNs, there’s more work on the front end but less day-to-day administration once properly configured.
If you don’t have widely scattered users and traveling users that need to employ 3CX Clients, the WhiteList option is far preferable. It sets up a WhiteList of devices that are authorized to access your PBX. Nobody else can even see the server on the Internet. To get started, log into your server as root using SSH or Putty. Be sure to login from a computer that will be used to manage your server so that this computer’s IP address gets whitelisted. You don’t want to lock yourself out of your own server! Then issue the following commands at the Linux prompt to run the TM3 installer, accept the license agreement, and choose either the WhiteList or BlackList option when prompted:
cd / wget http://incrediblepbx.com/tm3-3cx.tar.gz tar zxvf tm3-3cx.tar.gz rm -f tm3-3cx.tar.gz cd /root ./tm3-3cx.sh
When the installer finishes, press ENTER. You now have a functioning 3CX firewall with IPtables and Fail2Ban functionality to protect SSH logins from hacking attempts, IPset to block server access from certain countries, PortKnocker to facilitate remote user access to servers employing a WhiteList, and a collection of utilities in /root to facilitate WhiteListing and BlackListing of IP addresses and FQDNs by administrators.
3. Implementing the 3CX Firewall WhiteList
For the more technical types, here’s an overview of how the IPtables firewall is configured and functions. Currently, only IPv4 is protected. The basic setup is handled in /etc/iptables/rules.v4 by making a copy of rules.v4.tm3 and whitelisting 3 IP addresses: your server, your user PC from which you logged into SSH, and your public IP address. Additional whitelist entries are added using add-ip or add-fqdn in /root. Or end users can whitelist themselves using the PortKnocker credentials stored in /root/knock.FAQ. IPtables ALWAYS must be restarted/reloaded using the command: iptables-restart. This assures that all necessary components are reloaded including the base rules.v4 IPtables config plus the custom config in /usr/local/sbin/iptables-custom plus Fail2Ban. An administrator can remove whitelisted entries using /root/del-acct using the *.iptables filename associated with the entry to be removed. PortKnocker whitelist entries are stored by creation date.
Two templates for the TM3 custom configuration are stored in /usr/local/sbin. The WhiteList is iptables-custom.secure. The BlackList is iptables-custom.insecure. As part of the install, one or the other is copied into iptables-custom for use with your IPtables firewall. The code is well documented so that administrators can easily make modifications to support your own requirements. Simply rerun the tm3-3cx.sh installer once you have made changes, and your server will be reconfigured. Be advised that any previously added whitelist entries should be removed (/root/*.iptables) BEFORE rerunning the installer as these entries will not be replicated.
4. Using PortKnocker with the TM3 Firewall
There are two ways to use PortKnocker for end user management of the WhiteList. The default methodology is to temporarily WhiteList qualifying IP addresses whenever a successful port knock is performed from any remote site. This WhiteList addition to the firewall lasts only until the firewall is restarted with iptables-restart or the server is rebooted. For a mobile workforce, this is probably the preferable alternative with frequently updated remote IP addresses. The other alternative is to permanently add successful PortKnock IP addresses to the iptables-custom whitelist. The administrator can activate this by running the following command: iptables-knock activate. As with other WhiteList additions, these are stored in /root as *.iptables. To use PortKnocker, remote users will need the secret knock credentials stored in /root/knock.FAQ. Should you ever need to modify these codes when an employee is fired, simply edit /etc/knockd.conf and change the codes. Remember to revise /root/knock.FAQ with the new codes. Then restart PortKnocker: /root/knock-tester.sh.
5. Configuring Dynamic DNS for End Users
Here’s an easier way to set up remote users whose IP addresses regularly change either because of an ISP’s dynamic IP addressing scheme or because the user travels or frequently uses 3CX Clients from a smartphone. The trick here is to assign a fully-qualified domain name (FQDN) to each remote user’s device and then deploy a dynamic DNS update application on their device to keep the user’s current IP address in sync with their FQDN. As part of the TM3 implementation on 3CX, we included the /root/ipchecker script which checks for IP address changes every 10 minutes and updates the firewall whitelist accordingly. All that is required from the administrator is running /root/add-fqdn once for each remote user. Everything else is automatic on the 3CX server and the end user device.
There are a number of Dynamic DNS providers. Some are free and others have a modest annual fee. When it comes to DNS service, you get what you pay for. And our favorite remains dyndns.com. There are hundreds of domain names from which to choose, and there are update clients for most client platforms: Windows, Mac, Linux, iOS, and Android.
The setup procedure is straight-forward. (1) Choose a FQDN for each of your users on the dynamic DNS provider site. (2) Install and configure the DNS updater on each client device. (3) Run /root/add-fqdn on your 3CX server to add the FQDNs of each user to the TM3 WhiteList. (4) Restart IPtables: iptables-restart.
6. Implementing BlackLists with the TM3 Firewall
If an administrator elects NOT to deploy the 3CX firewall with a WhiteList and opts for the open 3CX firewall, then there are some additional steps to assure that your server remains secure. First, you’ll want to carefully monitor the 3CX Event Log in the 3CX web dashboard. When you spot hacking attempts that are being temporarily blocked by your 3CX server, immediately add them to your IPtables BlackList: /root/add-blacklist ipaddress. Thereafter, those users will no longer be able to access your server. After adding less than a handful of entries, our exposed server has not seen any further hacking attempts. YMMV!
7. Configuring Country Blocking with IPtables
The primary reason individual blacklist entries are unnecessary is because the TM3 installer automatically configures IPset to block access from a number of problematic countries. You can review these in /etc/block-china.sh and make modifications based upon your own requirements. Keep in mind that, if you add or remove countries from the script, you will need to add/remove the same entries in /usr/local/sbin/iptables-custom to assure that all of the countries you intend to block are assimilated into your firewall’s blacklist. Then reload the IPset tables and restart IPtables with this command: /etc/block-china.sh. To begin, you’ll need to decipher the country code for additional countries you wish to block. The country listing with codes is available here. The IPset country zones are available here.
The syntax for a new country addition in /etc/block-china.sh looks like this with the country name inserted in lines 1 & 4 and the country code inserted in lines 2 & 3:
/sbin/ipset -N china hash:net rm cn.zone /usr/bin/wget -P . http://www.ipdeny.com/ipblocks/data/countries/cn.zone for i in ; do /sbin/ipset -A china ; done
The blacklist entries in /usr/local/sbin/iptables-custom look like this using the country name from above:
/sbin/iptables -A INPUT -p tcp -m set --match-set china src -j DROP /sbin/iptables -A INPUT -p udp -m set --match-set china src -j DROP
None of the country modifications take effect until you reload the IPset tables and restart IPtables. Both are accomplished by running /etc/block-china.sh.
8. Hardening SSH with 3CX in the Cloud
If you chose to implement the TM3 WhiteList option, SSH on your 3CX server is insulated from SSH attacks because the bad guys can’t see or access port 22 on your server. However, if you’re using the non-WhiteList approach with IPtables, then some additional safeguards to secure SSH are appropriate. As part of the TM3 security suite, Fail2Ban was installed to block repeated attempts to login to SSH. While this offers some protection, be advised that Fail2Ban scans logs and, as such, requires a sufficient time slice of processing power to complete the task regularly. Some of the more vicious hacking attempts originate from extremely powerful server platforms that can monopolize processor resources thereby depriving Fail2Ban of the necessary horsepower to adequately protect your server from brute force SSH attacks. The most important thing you can do to protect SSH on your server is to regularly review /var/log/auth.log for hacking attempts and block those IP addresses using the add-blacklist script.
The most effective way to configure SSH access is to deploy key-based authentication using cryptographically secure keys. Once enabled and tested, be sure to remove the ability to login using your root password. But be aware that removing root password access will mean that you cannot login to your server from multiple devices without copying your private key to every device from which you wish to obtain access. An excellent tutorial that will walk you through the basic implementation procedure is available from Digital Ocean.
The other effective way to minimize SSH attacks is to change the default access port on your server from port 22 to some other TCP port above 1024. While there are arguments against this approach, if you have a dedicated IP address assigned to your server, the likelihood of a bad guy hijacking your IP address and setting up a script to fake SSH behavior and surreptitiously collect your passwords is extremely remote. Most of the bad guys use toolkits that target port 22 for brute force SSH attacks. By changing the port, you cut your vulnerability by about 99 per cent. Here’s how. First, edit /etc/ssh/sshd_config. Change the line near the top of the file from Port 22 to some port number above 1024. If the line is commented out with #, remove the #. Second, edit /etc/iptables/rules.v4. On or about line 27, change 22 to the port number you assigned in the first step. Third, edit /etc/fail2ban/jail.conf. Scroll down to the [ssh] section of the file and change the port entry to: port = ssh,1234 where 1234 is the port number you assigned in step one. Save the file. Fourth, restart SSH: /etc/init.d/ssh restart. Finally, restart IPtables: iptables-restart.
When using an SSH client to login to your server, the new syntax should look something like this: ssh -p 1234 root@ipaddress where 1234 is the port you assigned for SSH access to your server and ipaddress is the IP address or FQDN of your server. When using putty, be sure to change the port to match the SSH port you assigned for SSH access to your server.
Nerd Vittles Exclusive: Grab your new (free) 3CX perpetual license with unlimited SIP trunks, 10 extensions, 4 simultaneous calls, and 10-user conferencing here.
Originally published: Friday, June 23, 2017

Need help with 3CX or VoIP? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
- Some of our links refer users to providers that support Nerd Vittles through referral fees or advertising. These funds help cover the costs of our blog. We never recommend particular products solely to generate revenue. However, when pricing is comparable or particular features warrant our recommendation, we support these vendors and deeply appreciate their financial support of our software development efforts. [↩]
The Autonomous Car: Navigating Tesla’s Slippery Slope to the Promised Land

We continue our Autonomous Car series today with a report card on our first quarter results with the new Tesla Vision autopilot and a cautionary note to would-be Tesla owners. Since the new Tesla hardware was rolled out to vehicles manufactured in the last couple months of 2016, Tesla has had a bumpy ride and, in no small part, it has been due to self-inflicted wounds. The Tesla executive heading up the autopilot project abruptly quit and allegedly walked out the door with Tesla’s crown jewels. Then it became apparent that Tesla had misled fourth quarter buyers by promising autopilot software that was anything but ready for prime time. In fact, it barely existed. To make matters worse, Elon Musk finally acknowledged a couple weeks ago that their first generation autopilot hardware and software powered by Mobileye was nowhere to be found in the new vehicles. This was a careful way of admitting that Tesla was basically starting over with Tesla Vision. The alarming reports from new Tesla owners (685+ posts) confirmed that fairly quickly. For a glimpse at the complexity of autonomous driving, take a look at this in-depth review.
Tesla Autopilot 2.0: law firm attempts class action lawsuit against Tesla over self-driving claims | Electrek https://t.co/jffRu7l8jv
— Ward Mundy (@NerdUno) March 22, 2017
The Joke’s On You: What You Saw Ain’t What You Get
To make matters worse, Tesla had sold the vehicles by overpromising features which were nowhere near ready. BestRadar, one of the frequent contributors to TMC’s Tesla Motors Forum, recently posted some interesting comparisons of Tesla’s representations to buyers in October, 2016 to demonstrate the morphing which occurred after the first of the year. Using a tool called Copyscape he compared Tesla’s autopilot offering (AP2) from late 2016 to the revised text in early 2017. The actual before and after web pages are available as well. Here’s the Enhanced AutoPilot feature, a pricey $6,000 upgrade, that has caused fourth quarter 2016 buyers the most heartburn:
Here’s the Standard Safety Features offering also promised for delivery in December 2016:
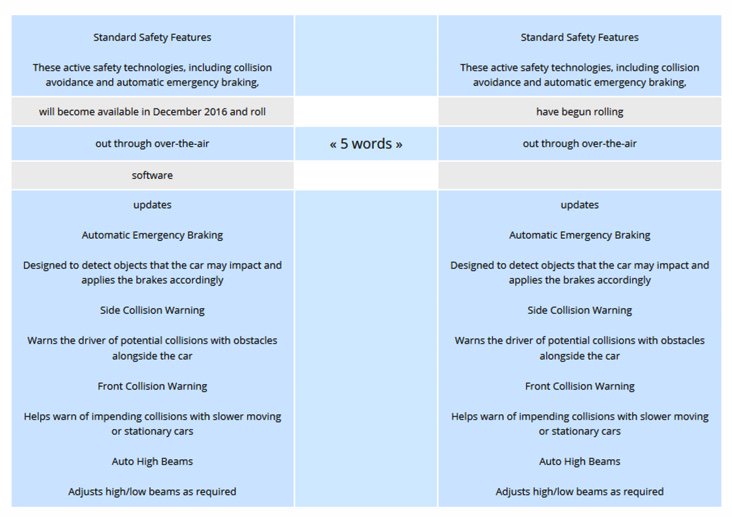
Let’s compare features promised to buyers by December 2016 to what has been delivered:
- Match Speed to Traffic Conditions (90% TACC; 55MPH on Interstate w/ AP2)
- Keep Vehicle Within a Lane (Curve-free with lane markings, minimal car following)
- Automatically Change Lanes w/o Driver Input (NO)
- Transition from One Freeway to Another (NO)
- Exit Freeway When Destination is Near (NO)
- Self-Park When Near a Parking Spot (20%)
- Summon Vehicle To/From Garage (NO)
- Collision Avoidance (NO)
- Automatic Emergency Breaking (NO)
- Side Collision Alerts (Worthless)
- Front Collision Warning (YES)
- Auto High Beams (NO)
- Auto Windshield Wipers (NO)
Keep in mind that those who purchased Tesla AP2 vehicles in the fourth quarter of 2016 had never seen an actual AP2 Tesla because they were not yet available. So the entire purchasing decision was based upon Tesla’s and Musk’s representations that the new Teslas were far superior to earlier vehicles both in terms of hardware and software. This was reinforced in the video contemporaneously released by Tesla (below) demonstrating Tesla Vision (AP2) as a fully autonomous driving experience. Only months later when California released its disengagement report for 2016 did we learn that the making of that video apparently resulted in traveling about 500 miles and logging 177 disengagement reports with the state over the 3-day filming period. A "disengagement" is defined as an autonomous driving event that forces a driver to take control of the vehicle. And never mind the video’s opening assertion that the entire trip was hands-free with the driver doing nothing. It further appears that, following production of the Tesla video, further self-driving experimentation with Tesla Vision was completely halted. Details here.
Beware the Ides of March
We haven’t mentioned SAFETY yet but you’ll want to read this if you’re considering a new Tesla. If you’ve ever driven a car with a toddler sitting in your lap holding the steering wheel with you, then you’ll appreciate the amount of care and attention you need to focus on a Tesla while AP2 is activated. It’s that dangerous. Forum reports of vehicles veering toward guard rails and ditches are common as are reports of Tesla vehicles swerving out of their lane in search of a lane divider while 18-wheelers are within six feet of your car. As one forum member observed, autopilot in a car differs dramatically from autopilot on a plane where a pilot who is alerted to take control has 5 minutes or more to react before a plane can descend from 30,000 feet. With a car, you’re talking about a fraction of a second when autopilot does something stupid and veers into another lane of traffic. This also isn’t a case of your Tesla relying upon Mobileye with a decade of self-driving experience under its belt. We’re talking about brand new, half-baked software. Labeling it as "beta" suggests you really must be a Tesla shareholder.
I chose the image at the top of this article because it literally sent shivers down my spine thinking some poor fool might actually try using AP2 on this road. Look at the margin of error available with your $100,000+ autonomous vehicle.
Shares of Mobileye surged more than 30% in pre-market trading after agreeing to be bought by Intel for about $15 billion. $MBLY $INTC
— USA TODAY Tech (@usatodaytech) March 13, 2017
Dangerous software is only part of the problem. The other half is Tesla’s complete failure to document for its drivers what works and what doesn’t. It’s one thing to do something stupid after you’ve been warned not to do it. It’s quite another to have to discover all of the mines in the minefield for yourself. It’s worth recalling that, in selling the $6,000 Enhanced Autopilot feature, Tesla represented that the software was "expected to complete validation" by the end of December, 2016. In the English language, that certainly suggests that the software is all but ready and just needs a bit more testing to validate that all of the promised features are safe before uploading it to Tesla vehicles. Remember that Tesla was still saying the same thing at the end of December and even into the middle of January. Truth be told, we’re not sure large chunks of the deliverable software have even been written yet. We’re not talking about "puffing." Take a look at the list above and where we stand today. Then compare that to what Tesla was promising in sales contracts and actually showcasing in videos four to five months ago:
Deep Neural Networks and Machine Learning
For the technically curious, it’s worth mentioning the complexity of the Tesla autopilot approach and how primitive it remains today. Keep in mind that Tesla’s AP1 vehicles had the luxury of Mobileye technology with 10 years of machine learning to identify dangerous and safe objects using cameras. To fully appreciate the enormity of the AP2 problem, take a look at Tesla’s explanation of its new radar-centric approach. Then enjoy a fascinating introduction to Machine Learning 101. In a nutshell, Tesla has got to create a "map" whitelisting every stationary object in the world and determining with 99.99% accuracy whether it is unlikely to pose a collision risk to a Tesla vehicle. The reason is because radar can have a difficult time distinguishing an overhead sign 25 feet in the air and an overhead sign that has fallen onto the highway. You obviously want the car to slam on the brakes for the latter one but not for every overhead sign you encounter while traveling down an interstate highway. We haven’t yet considered electronic highway signs where the messaging on the sign constantly changes. To your Tesla, every change in the sign message looks like a new sign. Here’s another example at the neighborhood level. We have two 90 degree turns in the street near our home. To date, our Tesla vehicle with AP2 proceeds at full speed into both locations. Without manual intervention, the AP2 result would either land your Tesla in the water or it would plow into a wall. Now let’s multiply those situations by a hundred million, and you’ll appreciate the complexity of the task at hand and better understand how deceptive the Tesla video really was.
Dear Elon: We Still Love You, Warts and All
Don’t take our observations the wrong way. We love our Tesla vehicle and appreciate everything Elon Musk is trying to do both in terms of electric vehicles and autonomous driving. But, as we have observed previously, Elon can morph from Steve Jobs visionary into used car salesman with a single tweet. And he often does, particularly when Tesla earnings reports are at stake. We’ve been in the technology business for more than 30 years and we’ve owned 25 different automobiles. When it comes to software development or car purchases, there’s not much we haven’t witnessed first hand. But Tesla’s approach of overselling and underdelivering functionality is novel. And we believe it is precarious if not downright dangerous from both a legal and safety standpoint. That’s unfortunate because a class action lawsuit or serious accident involving a Tesla with AP2 which, unlike the earlier vehicles, has no track record of safety could set back not only Tesla but all autonomous driving projects by years. It also would prompt federal and state regulators to take a very hard look at the types of vehicles which are being unleashed on public highways.
Our plea to Elon is please clean up your act before releasing Model 3 vehicles to 400,000 unsuspecting owners. People are accustomed to purchasing vehicles with the expectation that the features they’ve purchased will actually work and will do so in a SAFE manner. They also expect to be able to get their cars repaired. Read this nightmare scenario from a fender bender. Stop overpromising and overhyping what new Tesla vehicles can actually do and level with buyers on the very real limitations of the current vehicles. Drivers need to understand what works and what doesn’t before they set foot in a new Tesla. A simple disclaimer that the software is experimental really doesn’t cut it. As it stands today, autopilot using AP2 is little more than a wish and a prayer much like our license plate. Here’s hoping we all make it through this Magic Carpet Ride alive.

Finally, a word about the Tesla Model 3. We’ve commented before that customers will be hard-pressed to purchase a Tesla Model 3 for $35,000. Guess what? Here’s a price list formulated by one industrious user based upon estimates of feature costs derived from current Tesla vehicles. While it is not an official Tesla document, it provides a fairly accurate estimate of the pricing that Tesla Model 3 buyers can expect to see:
Tesla Model 3 pricing and options have not leaked, here's what happened https://t.co/1vJ46TdBMb pic.twitter.com/RWTp7tkxv1
— Electrek.co (@ElectrekCo) March 5, 2017
Move Over Tesla: Competition Coming on April 1
Tesla will no longer be the only option starting April 1. @Lloyd shared a sneak peek at Google’s surprise. Production looks eerily similar to Tesla’s self-driving video. 😉
Published: Monday, March 13, 2017
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
Best of Both Worlds: Marrying Asterisk to 3CX’s Free PBX with a $35 Raspberry Pi

One of the real beauties of Asterisk® has always been its flexibility in talking to other PBXs, both commercial and open source. There are numerous reasons why you might want to try this. First, it makes it easy to migrate to a commercial platform where you can get support for mission critical telephony requirements. Second, you may want a hybrid setup where servers with on-site support personnel can run Asterisk while remote satellite offices can take advantage of a commercial PBX and the support options it offers. Third, you may want to take advantage of specific features that are only available by relying upon multiple PBX solutions. In the case of 3CX, their integrated softphone clients with one-click setup simplicity, conferencing and WebRTC apps, and Call Center offerings are the best in the business while providing unmatched VoIP security. Asterisk on the other hand is light-years ahead of almost everybody in the text-to-speech and voice recognition fields while offering the most powerful VoIP toolkit to build any custom VoIP application imaginable.
Today we thought it would be fun to walk you through the easy way to tie an Incredible PBX server with all its features to a powerful (free) 3CX platform with its virtually flawless softphone clients.1 When we’re finished, you’ll have a free 3CX server in the Cloud at a one-time total cost of $17.50. And you’ll be able to place and receive free U.S./Canada calls from any iPhone, Android phone, or PC using the 3CX client from anywhere in the world with nothing more than a WiFi connection. The Google Voice trunk supporting the calls will reside on Incredible PBX for the Raspberry Pi. When you’re sold on the power of the 3CX platform, you can upgrade to the 3CX 4-simultaneous call commercial offering with unlimited users and trunks at an annual cost of just $149. Maintenance and upgrades are included. Large organizations have relied upon back office servers for custom applications forever. And now you can take advantage of the same flexibility using a tiny $35 Raspberry Pi and our free (as in really free) Incredible PBX software. No Gotchas!
Initial Raspberry Pi Platform Setup
Before we can interconnect 3CX’s Free PBX with a Raspberry Pi, you obviously have to set up both PBX platforms. For the Raspberry Pi, our recent Nerd Vittles tutorial will walk you through the setup process. In lieu of a Raspberry Pi, you can use any legacy FreePBX®-based Asterisk platform including Incredible PBX 13, PIAF3, Elastix®, AsteriskNOW®, or FreePBX Distro®. The setup procedure is exactly the same.
Building a 3CX Server in the Cloud
Building a 3CX server in the Cloud is equally easy. Let’s go through the process once again. If you’re just experimenting, a lifetime Cloud-based server at CloudAtCost for a one-time charge of $17.50 cannot be beat. We would hasten to add that we don’t recommend this platform for production use, but it’s a terrific proof-of-concept option. When you’re actually ready to deploy 3CX for production use, the least costly Cloud solution is the $3.49 per month OVH RAID offering with 2GB of RAM and 10GB storage. The $5 per month offerings from Digital Ocean and Vultr are other alternatives worth a look. Both of these platforms come with free credits ($10 and $20, respectively) to let you try things out.
To get started, sign up for a $17.50 server at Cloud at Cost. They will send you credentials to log into the Cloud at Cost Management Portal. Change your password IMMEDIATELY after logging in. Just go to SETTINGS and follow your nose.
To build your free 3CX PBX, create a virtual machine by clicking on the CLOUDPRO button in the CloudAtCost control panel. Then click Add New Server. Choose 1 CPU, 512MB RAM, and 10GB storage for your server. Choose Debian 8 64bit as the OS Type and click Complete.
While CloudAtCost is building your server platform, obtain a free license key for 3CX.
Once the Debian 8 server appears in your Control Panel, it will look something like what’s shown above, not CentOS obviously. The red arrow points to the i button you’ll need to click to decipher the password for your new virtual machine. You’ll need both the IP address and the password for your new virtual machine in order to log into the server which is now up and running with a barebones Debian 8 operating system. Note the yellow caution flag. That’s telling you that Cloud at Cost will automatically shut down your server in a week to save (them) computing resources. You can change the setting to keep your server running 24/7. Click Modify, Change Run Mode, and select Normal – Leave Powered On. Click Continue and OK to save your new settings.
Finally, you’ll want to change the Host Name for your server to something more descriptive than c7…cloudpro.92… Click the Modify button again and click Rename Server to make the change. Your management portal then will show the new server name as shown above.
Next, log in to your new Debian server as root using SSH or Putty and issue the commands below. Step #1 is to change your root password. What appears as the fourth line below is actually part of the third line and needs to be run as a single command. The last line to install SendMail will actually be run after you elect to use the Web Interface Wizard to configure 3CX. Just run it from the SSH command line before you switch to a browser to complete the 3CX setup.
passwd wget -O- http://downloads.3cx.com/downloads/3cxpbx/public.key | apt-key add - echo "deb http://downloads.3cx.com/downloads/3cxpbx/ /" | tee /etc/apt/sources.list.d/3cxpbx.list apt-get update rm -f /zang-debian.sh apt-get -y install 3cxpbx apt-get -y install sendmail sendmail-bin
When the initial setup finishes, choose the Web Interface Wizard and complete the install using your favorite web browser. Enter your 3CX license key when prompted. Make up a very secure Username and Password to access your 3CX portal. Specify that your IP address is Dynamic when prompted (even though it isn’t). This tells 3CX to generate an FQDN for your server. Accept the default ports for HTTP (5000) and HTTPS (5001) access to your server. We recommend choosing 4-digit extensions numbers which will make it easy to distinguish 3CX extension numbers from 3-digit extension numbers of the RasPi platform. While logged into the 3CX management portal, adjust Settings → Email to Mail Server → 127.0.0.1 and Reply to → noreply@YourActual3CX-FQDN. Leave the other settings blank and click TEST then OK. Now download your favorite 3CX smartphone client, send yourself the Welcome Email for your default extension, and your 3CX initial setup is complete.
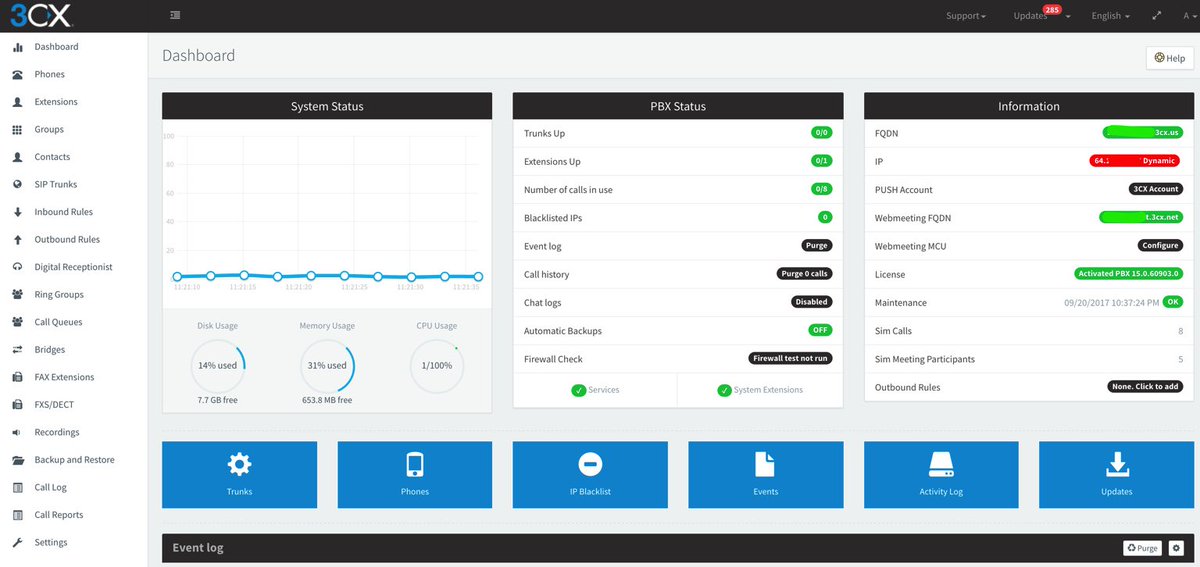
Server Interconnection Overview
Now we’re ready to interconnect the two servers. What we’ll be doing is creating Trunks on both the Raspberry Pi and the 3CX server and tying them together. We’ll use this trunk to handle the call traffic between the two PBXs. Then we’ll add incoming and outgoing call routes on both servers to specify how the individual calls should be routed. Because the free version of 3CX limits the administrator to a single trunk, we’ll offload all of the provider trunks to the Raspberry Pi and reserve the one available 3CX trunk as the interconnect path to the Raspberry Pi. For today’s setup, we’ll use 3CX’s free softphone clients as the actual phone devices for end-users. Of course, you could also use your favorite SIP phones, and 3CX provides automatic configuration for dozens of devices. But we want to introduce the 3CX smartphone clients because they provide an incredibly easy way to get users connected without having to worry about punching holes in firewalls.
To place outbound calls on the 3CX side, 3CX provides enormous flexibility in call routing. Because we chose 4-digit local extensions when we set up the 3CX server, it will make it easy to route other calls through the outbound trunk to the Raspberry Pi using nothing more than the length of the dial string. For example, 3-digit calls line up perfectly with extension numbers on the Incredible PBX for RasPi platform. So 3CX users can easily reach extensions connected directly to the Raspberry Pi. And 10-digit 3CX calls will be forwarded to the Raspberry Pi as traditional outbound calls. They will be processed just as if you had dialed a 10-digit call from a Raspberry Pi extension. For example, if you have a registered Google Voice trunk to handle 10-digit calls on the Raspberry Pi, then the same call path would be used for calls originating from 3CX extensions. And, yes, calls to the U.S. and Canada would still be free and would display the CallerID associated with the Raspberry Pi’s Google Voice trunk. You could get more creative and add an additional dialing prefix on the 3CX side to route specific types of calls to a designated outbound trunk on the Raspberry Pi side based upon the dialing prefix, but we’ll leave that as a homework project for you.
For incoming calls on the 3CX side, in addition to 4-digit local extension-to-extension calling, we can define the destination for incoming calls that originate from either a Raspberry Pi extension or from outside calls coming in from one of the Raspberry Pi’s provider trunks. These are managed by assigning one or more DIDs in the 3CX trunk configuration and then creating 3CX Inbound DID Rules that tell 3CX where to route calls to each defined DID. For 3CX softphone clients registered to extensions, it means your cellphone will ring whenever a call is routed to that particular extension. On the Raspberry Pi side, we create Incoming Call Routes for each DID to be routed to 3CX and specify our defined 3CX trunk as the destination for incoming calls from those DIDs. Not all DIDs on the Raspberry Pi have to be routed to the 3CX server obviously. That is merely one of many call destination options available to the administrator on the Raspberry Pi server.

Here’s a typical call path for an outside call that is placed to a Google Voice number registered with your Raspberry Pi. The Asterisk server running on the Raspberry Pi would answer the call placed to the Google Voice Trunk. Asterisk then would check for an Incoming Route on the Raspberry Pi with a DID matching the number of your Google Voice trunk. Finding a match, Asterisk would check for the desired destination of the call and would note that it is listed as the registered 3CX trunk. Asterisk would pass the call through this trunk to the 3CX server including its associated DID and CallerID info. The 3CX server would answer the incoming call and would check for an Incoming Route matching the DID passed from Asterisk. Finding a match, it would pass the call to the Extension specified in the Incoming Route. When 3CX rings the extension, it would also detect that a softphone was registered to that extension and would also ring the 3CX client on the user’s smartphone. The user answers the call on the 3CX client of their smartphone and begins a conversation. The free version of the 3CX server supports 8 simultaneous calls so you are unlikely to ever run out of call paths for calls in the home and small office environment.
Firewall Setup for Server Interconnection
Because the 3CX server is sitting in the Cloud, its firewall is configured automatically as part of the setup process. If your Raspberry Pi is sitting behind a NAT-based firewall, then you would need to map port UDP 5060 from the router on your public IP address to the private IP address of your Raspberry Pi. In addition, login to your Raspberry Pi as root using SSH and run /root/add-ip to whitelist the public IP address of your 3CX server in the cloud. Otherwise, the 3CX server cannot establish a connection to your Raspberry Pi.
Raspberry Pi Trunk Configuration
Using a browser, login to the web interface for FreePBX on your Raspberry Pi and choose Connectivity → Trunks → Add SIP (chan_sip) Trunk. Name the trunk remote. In the Outgoing Settings, make the entries shown below naming the trunk remote and using a secure secret that will be used to interconnect the two servers. The Register String looks like the following: main:secret@3CX-IP-Address where main is the 3CX server trunk name, secret is your secure secret, and 3CX-IP-Address is the 3CX public IP address.
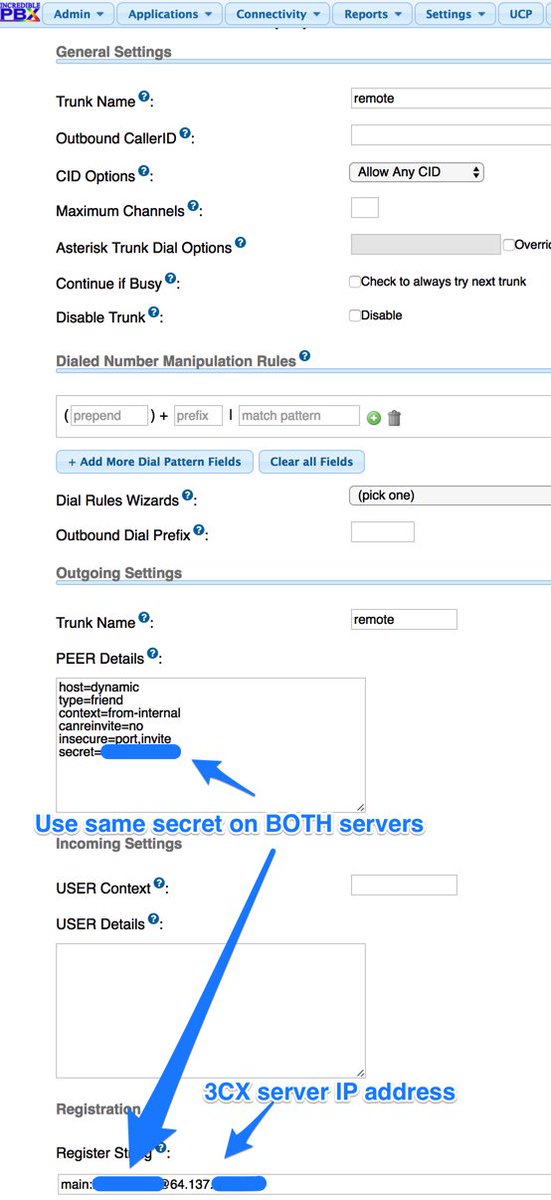
3CX Trunk Configuration
Using a browser, login to your 3CX server: https://3CX-IP-Address:5001 or http://3CX-IP-Address:5000. From your Dashboard, choose SIP Trunks → Add SIP Trunk. Create a Generic SIP Trunk and then fill in the blanks as shown below. For Registrar/Server/Gateway Hostname or IP, use the public IP address or FQDN of your Raspberry Pi. For Type of Authentication choose Outbound. The authentication credentials should be remote and the secure secret you chose, and the Main Trunk No should match the DID of the Google Voice trunk you set up on your Raspberry Pi. Then pick a default Destination for incoming calls.
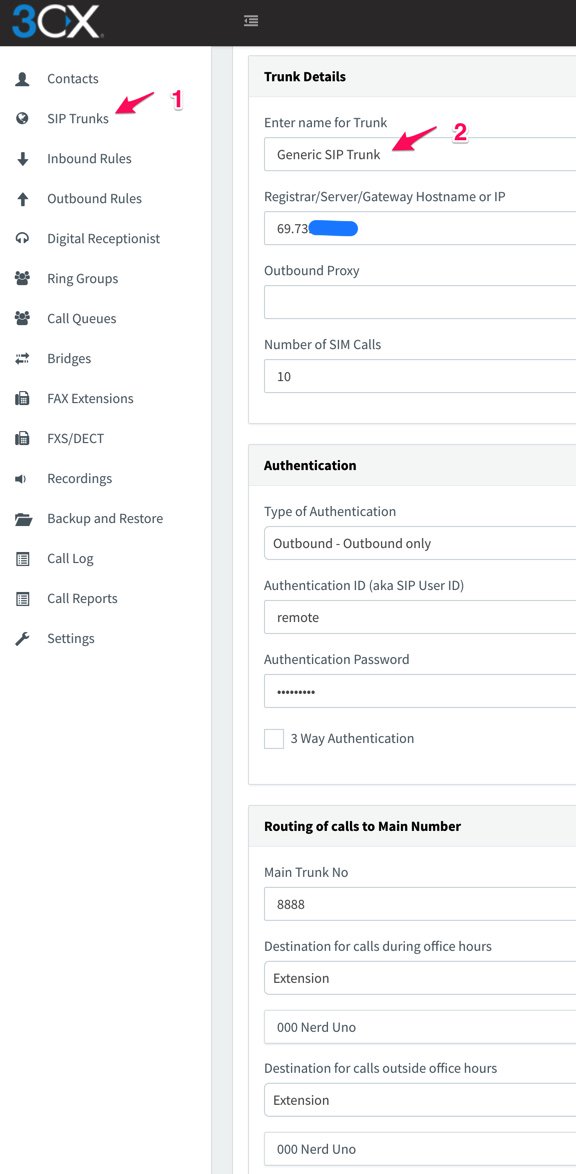
3CX Outbound Rules Configuration
Next, we need to tell 3CX which outgoing calls to send out through the Raspberry Pi trunk we just set up. In our example today, we’re going to send all 10-digit calls and 3-digit calls. The 10-digit calls will be routed out the Google Voice trunk on the Raspberry Pi side. And the 3-digit calls will be sent directly to Raspberry Pi extensions. So we’ll need two Outbound Rules.
For the first rule, choose Outbound Rules → Add. For the Rule Name, specify StandardOut. Apply the rule to Calls to Numbers with a length: 10. For Route 1, choose Generic SIP Trunk as the Destination. Click OK to save the new rule.
For the second rule, choose Outbound Rules → Add. For Rule Name, specify StandardInt. Apply the rule to Calls to Numbers with a length: 3. For Route 1, choose Generic SIP Trunk as the Destination. Click OK to save the new rule.
If you already have configured a 3CX smartphone client for one of your 3CX extensions, you now should be able to dial any 3-digit or 10-digit number and have the call processed through your new 3CX→RasPi trunk without any further setup assuming you’ve created a Google Voice trunk on the Raspberry Pi side. That wasn’t too hard, was it?
Routing Incoming Google Voice Calls to 3CX
Depending upon your own requirements, you may want to route incoming Google Voice calls or other trunks directly to an extension and/or softphone on your 3CX server. You obviously could set up multiple trunks of any type on the Raspberry Pi side and have the calls to each trunk routed to a different extension or softphone on the 3CX side. To enable this on the 3CX side, edit your Generic SIP Trunk and click the DIDs tab. Then Add each of the 10-digit DIDs of the Raspberry Pi trunks you wish to redirect. Next, create an Inbound Rule for every DID and tell 3CX where to route the calls.
On the Raspberry Pi side, add each of your Google Voice Trunks. Then create an Inbound Route for each DID and specify the Destination as Trunks → Remote (sip). The 3CX server will take care of routing the various incoming calls to each of the Google Voice trunks to its predefined extension and/or softphone. Enjoy!
Originally published: Monday, March 6, 2017
9 Countries Have Never Visited Nerd Vittles. Got a Friend in Any of Them https://t.co/wMfmlhiQ9y #asterisk #freepbx pic.twitter.com/TPFGZbqWB6
— Ward Mundy (@NerdUno) April 22, 2016

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
- A simpler Bridge setup is available in the paid versions of 3CX. [↩]


 JUST RELEASED: Visit the Incredible PBX Wiki
JUST RELEASED: Visit the Incredible PBX Wiki