Home » Technology » Smartphones (Page 6)
Category Archives: Smartphones
Interconnecting a Mobile PBX to the Asterisk Mothership

The Holy Grail for a mobile VoIP solution is a simple way to connect back to your primary Asterisk® PBX via Wi-Fi from anywhere in the world to make and receive calls as if you never left. Let’s tick off the potential problems. First, many home-based PBXs are sitting behind NAT-based routers. Second, almost all remote Wi-Fi connections are made through a NAT-based router. Third, chances are the remote hosting platform blocks outgoing email from downstream servers such as a mobile PBX. Fourth, deciphering the IP address of your remote connection can be problematic. Fifth, the chances of experiencing one-way audio or no audio on your VoIP calls is high because of NAT-based routers at both ends of your connection.
Last week we introduced OpenVPN as a solution for those with multiple VoIP sites to interconnect. But there’s a much simpler solution for those that travel regularly and want to avoid the complexity of configuring OpenVPN. Here is a quick thumbnail of the setup we recommend as your mobile companion, and you’ll never have a one-way audio problem again. In terms of hardware, you’ll need a Raspberry Pi 3B+ with its native WiFi support and a Windows or Mac notebook computer for traveling. You’ll also need a NeoRouter VPN server to make this process seamless. If you’ve already set up an OpenVPN server platform, it will work equally well. One advantage of NeoRouter is that clients can be added from the client side without having to create a config file on the VPN server. All you need is a username and password. But the choice of VPN platform is totally a matter of preference. The objective using either OpenVPN or NeoRouter is secure communications to your home base. We don’t want to have to reconfigure either your home PBX or your traveling PBX or your notebook PC based upon changes in your public and private IP addresses.
Today we’ll walk you through the easiest way to set up a (free) NeoRouter server on the Internet. It can be used to connect up to 254 devices on an encrypted private LAN. We’re delighted to have finally found a perfect use for the (free) Google Cloud instance.
Using a RaspberryPi 3B+, build an Incredible PBX 13-13.10 platform by following our previous tutorial. We’ll set this up on your home WiFi network so that you only have to throw the Raspberry Pi and its power supply in your suitcase when you travel. As part of the setup, we’ll download NeoRouter and activate private IP addresses for your notebook computer as well as both of your PBXs (using nrclientcmd). Next, we’ll interconnect the two PBXs using SIP trunks and the NeoRouter private LAN IP addresses. We’ll take advantage of a neat little Raspberry Pi trick by storing a wpa_supplicant.conf template on your PC for the remote WiFi setup even though we don’t yet know anything about the remote LAN. Once we know the SSID and password at the remote destination, we’ll use your notebook computer to edit the template and transfer the file to the /boot folder of your RasPi’s microSD card. When the card then is inserted and the RasPi is booted, it will automatically move the template to the proper /etc/wpa_supplicant folder to successfully activate your WiFi connection. We’ll also load links, a fast text-based browser, just in case you encounter a hotel that requires some sort of acknowledgement or password before establishing your WiFi connection to the Internet.

Setting Up a (free) NeoRouter Server in the Cloud
Because NeoRouter uses a star-based VPN architecture, that means the NeoRouter Server must always be available at the same IP address for all of the NeoRouter Clients (aka Nodes) to talk to. If you already have a cloud-based server that has a static IP address and can handle the traffic cop duties of NeoRouter Server, then that’s an ideal place to install NeoRouter Server. Simply download the Free flavor of NeoRouter Server that matches your existing platform and install it. Add an FQDN for your server’s IP address, and you’re all set. A detailed summary of available management options is included in our previous NeoRouter v2 article.
We devoted a couple weeks to Google Cloud instances last month, and it turned out to be a pretty awful platform for hosting Asterisk. But the free offering looks to be a perfect fit as a hosting platform for NeoRouter Server. You also won’t have to worry about Google going out of business anytime soon. So let us walk you through an abbreviated setup process on the Google Cloud platform. If you’re just getting started with Google Cloud, read our previous article to take advantage of Google’s generous $300 offer to get you started and to generally familiarize yourself with the mechanics of setting up an instance in the Google Cloud.
For NeoRouter Server, navigate to https://console.cloud.google.com. Click the 3-bar image ![]() in the upper left corner of your Dashboard. This exposes the Navigation Menu. In the COMPUTE section of the Dashboard, click Compute Engine -> VM Instances. Then click CREATE PROJECT and name it. Now click CREATE INSTANCE and Name it nrserver. The instance name becomes the hostname for your virtual machine. If you want to remain in the Free Tier, choose f1-micro instance as the Machine Type and choose a U.S. Region (us-central1, us-east1 or us-west1). For the Boot Disk, choose CentOS 6 and expand the disk storage to at least 20GB (30GB is available with the Free Tier). For the Firewall setting, leave HTTP and HTTPS disabled. Check your entries carefully and then click the Create button.
in the upper left corner of your Dashboard. This exposes the Navigation Menu. In the COMPUTE section of the Dashboard, click Compute Engine -> VM Instances. Then click CREATE PROJECT and name it. Now click CREATE INSTANCE and Name it nrserver. The instance name becomes the hostname for your virtual machine. If you want to remain in the Free Tier, choose f1-micro instance as the Machine Type and choose a U.S. Region (us-central1, us-east1 or us-west1). For the Boot Disk, choose CentOS 6 and expand the disk storage to at least 20GB (30GB is available with the Free Tier). For the Firewall setting, leave HTTP and HTTPS disabled. Check your entries carefully and then click the Create button.
When your virtual machine instance comes on line, jot down the assigned public IP address. We’ll need it in a minute. Now click on the SSH pull-down tab and choose Open in a Browser Window. Now we need to set a root password and adjust the SSH settings so that you can login from your desktop computer using SSH or Putty:
sudo passwd root su root nano -w /etc/ssh/sshd_config
When the editor opens the SSH config file, add the following entries. Then save the file and restart SSH: service sshd restart
PermitRootLogin yes PasswordAuthentication yes
You now should be able to log in to your instance as root from your desktop computer using SSH or Putty. Test it to be sure: ssh root@server-IP-address
Before we leave the Google Cloud Dashboard, let’s make the assigned public IP address permanent so that it doesn’t get changed down the road. Keep in mind that, if you ever delete your instance, you also need to remove the assigned static IP address so you don’t continue to get billed for it. From Home on the Dashboard, scroll down to the NETWORKING section and choose VPS Network -> External IP Addresses. Change the Type of your existing address to Static and Name it staticip. Next, choose Firewall Rules in the VPS Network section and click CREATE FIREWALL RULE. Fill in the template like the following leaving the other fields with their default entries. Then click CREATE.
- Name: neorouter
- Target Tags: neorouter
- Source IP Range: 0.0.0.0/0
- Protocols/Ports: check tcp: 32976
CAUTION: Before this firewall rule will be activated for your instance, it also must be specified in the Network Tags section for your instance. Shut down your instance and add the neorouter tag by editing your instance. Then restart your instance.
Now we’re ready to install NeoRouter Free v2 Server on your instance. Be sure to choose the Free v2 variety. Log back into your server as root using SSH/Putty and issue these commands:
yum -y update yum -y install nano wget http://download.neorouter.com/Downloads/NRFree/Update_2.3.1.4360/Linux/CentOS/nrserver-2.3.1.4360-free-centos-x86_64.rpm rpm -Uvh nrserver-2.3.1.4360-free-centos-x86_64.rpm /etc/rc.d/init.d/nrserver.sh restart nrserver -setdomain <DOMAINNAME> <DOMAINPASSWORD> nrserver -adduser <USERNAME> <PASSWORD> admin nrserver -enableuser <USERNAME> nrserver -showsettings
Finally, add the following command to /etc/rc.local so that NeoRouter Server gets started whenever your instance is rebooted:
echo "/etc/rc.d/init.d/nrserver.sh start" >> /etc/rc.local
Installing Incredible PBX 13-13.10 on a Raspberry Pi
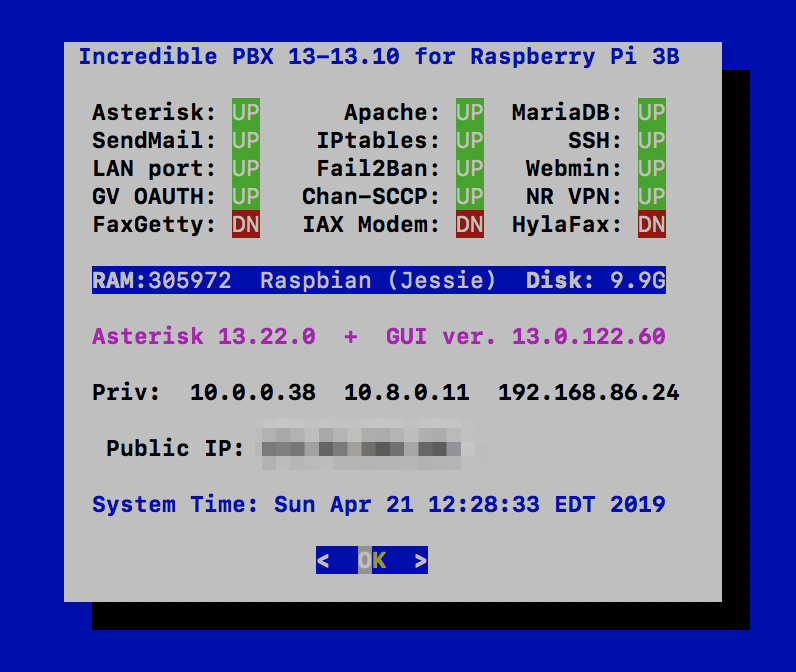
Configuring NeoRouter Client on Your Computers
On Linux-based (non-GUI) platforms, setting up the NeoRouter Client is done by issuing the command: nrclientcmd. You’ll be prompted for your NeoRouter Server FQDN as well as your username and password credentials. Perform this procedure on both your home PBX and the Raspberry Pi.
To add your Windows or Mac notebook to the NeoRouter VPN, download the appropriate client and run the application which will prompt for your NeoRouter Server FQDN as well as your NeoRouter credentials. Once completed, you should see all three machines in your NeoRouter Free Client Dashboard: your PC as well as your home PBX and Raspberry Pi-based Incredible PBX. Make note of the private VPN addresses (10.0.0.X) of both your home PBX and your Raspberry Pi. These VPN addresses never change, and we’ll need them to interconnect your PBXs and to set up a softphone on your notebook computer.
Admininistrative Tools to Manage NeoRouter
Here are a few helpful commands for monitoring and managing your NeoRouter VPN.
To access your NeoRouter Linux client: nrclientcmd
To restart NeoRouter Linux client: /etc/rc.d/init.d/nrservice.sh restart
To restart NeoRouter Linux server: /etc/rc.d/init.d/nrserver.sh restart
To set domain: nrserver -setdomain YOUR-VPN-NAME domainpassword
For a list of client devices: nrserver -showcomputers
For a list of existing user accounts: nrserver -showusers
For the settings of your NeoRouter VPN: nrserver -showsettings
To add a user account: nrserver -adduser username password user
To add admin account: nrserver -adduser username password admin
For a complete list of commands: nrserver –help

Interconnecting Your Raspberry Pi and Home PBX
To keep things simple, our setup examples below assume the following NeoRouter VPN addresses: Home PBX (10.0.0.1) and Raspberry Pi (10.0.0.2). Using a browser, you’ll need to login to the GUI of your Home PBX and Raspberry Pi and add a Trunk to each PBX. Be sure to use the same secret on BOTH trunk setups. We don’t recommend forwarding incoming calls from your Home PBX to your Raspberry Pi because most folks won’t be sitting in their hotel room all day to answer incoming calls. Instead, add the number of your smartphone to a Ring Group on the Home PBX and don’t forget the # symbol at the end of the number. On the Raspberry Pi side, we are assuming that whenever a call is dialed from a registered softphone with the 9 prefix, the call will be sent to the Home PBX for call processing (without the 9). For example, 98005551212 would send 800-555-1212 to the Home PBX for outbound routing and 9701 would send 701 to the Home PBX for routing to the 701 extension. You can obviously adjust your dialplan to meet your own local requirements.
On the Home PBX, the chan_sip trunk entries should look like this:
Trunk Name: raspi-remote PEER DETAILS host=10.0.0.2 type=friend context=from-internal username=home-pbx fromuser=home-pbx secret=some-password canreinvite=no insecure=port,invite qualify=yes nat=yes
On the Raspberry Pi, the chan_sip trunk entries should look like this:
Trunk Name: home-pbx PEER DETAILS host=10.0.0.1 type=friend context=from-internal username=raspi-remote fromuser=raspi-remote secret=some-password canreinvite=no insecure=port,invite qualify=yes nat=yes
On the Raspberry Pi, add an Outbound Route named Out9-home-pbx pointed to home-pbx Trunk with the following Dial Patterns. For each Dial Pattern, prepend=blank and prefix=9:
dial string: 1NXXNXXXXXX dial string: NXXNXXXXXX dial string: *98X. dial string: XXX dial string: XXXX dial string: XXXXX
Tweaking Your Raspberry Pi for WiFi Mobility
wpa_supplicant.conf config file to the /boot directory on the card once you arrive at your destination and know the SSID and password of the local WiFi network. When the Raspberry Pi is subsequently booted, the operating system will move the config file to the /etc/wpa_supplicant directory so that your WiFi network will come on line. Here’s what a typical wpa_supplicant.conf file should look like using your actual credentials. The last network section handles open WiFi network connections (think: McDonald’s) if you want to enable them:
country=US
update_config=1
network={
ssid="your-SSID"
psk="your-SSID-password"
key_mgmt=WPA-PSK
scan_ssid=1
priority=5
}
network={
key_mgmt=NONE
priority=1
}
The other gotcha is that some public WiFi networks require some type of web login procedure before you can actually access the Internet even though an IP address may have been assigned to your Raspberry Pi. To handle this situation, you’ll need a text-based web browser on the Raspberry Pi that can be accessed through your notebook PC using SSH and your Raspberry Pi’s VPN address. Our favorite is links which can be installed on your Raspberry Pi before you pack up.
apt-get install links -y
Once you arrive at your destination, connect both your notebook PC and Raspberry Pi to the same WiFi network, login to the RasPi with SSH at the VPN address assigned to your RasPi, and run links to start the browser. Press <esc> to access the links menu options. If you can’t access your RasPi at the VPN IP address, try its WiFi-assigned local IP address.
Adding a Softphone to Your Notebook PC
We recommend YateClient which is free. Download it from here. Run YateClient once you’ve installed it and enter the credentials for an extension on your Raspberry Pi. Then enter the VPN IP address of your server plus your extension’s password. Click OK to save your entries.
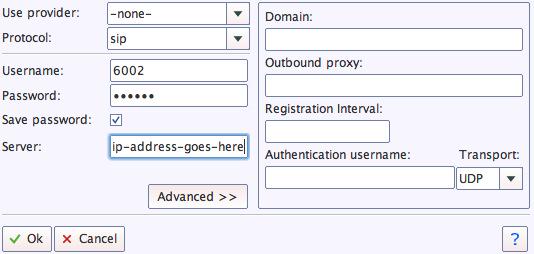
If you are a Mac user, another great no-frills softphone is Telephone. Just download and install it from the Mac App Store.
Adding a Softphone to Your Smartphone
Enjoy your pain-free traveling!
Originally published: Monday, April 22, 2019

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

A New VPN for All Seasons: Introducing OpenVPN for Asterisk

This month marks our twentieth anniversary wrestling with virtual private networks. Here’s a quick walk down memory lane. Our adventure began with the Altiga 3000 series VPN concentrators which we introduced in the federal courts in 1999. It was a near perfect plug-and-play hardware solution for secure communications between remote sites using less than secure Windows PCs. Cisco quickly saw the potential, gobbled up the company, and promptly doubled the price of the rebranded concentrators. About 10 years ago, we introduced Hamachi® VPNs to interconnect Asterisk® and PBX in a Flash servers. At the time, Hamachi was free, but that was short-lived when they were subsequently acquired by LogMeIn®. What followed was a short stint with PPTP VPNs which worked great with Macs, Windows PCs, and many phones but suffered from an endless stream of security vulnerabilities. Finally, in April 2012, we introduced the free NeoRouter® VPN. Version 2 still is an integral component in every Incredible PBX® platform today, and PPTP still is available as well. While easy to set up and integrate into multi-site Asterisk deployments, the Achilles’ Heel of NeoRouter remains its inability to directly interconnect many smartphones and stand-alone SIP phones, some of which support the OpenVPN platform and nothing else.

The main reason we avoided OpenVPN® over the years was its complexity to configure and deploy.1 In addition, it was difficult to use with clients whose IP addresses were frequently changing. Thanks to the terrific work of Nyr, Stanislas Angristan, and more than a dozen contributors, OpenVPN now has been tamed. And the new server-based, star topology design makes it easy to deploy for those with changing or dynamic IP addresses. Today we’ll walk you through building an OpenVPN server as well as the one-minute client setup for almost any Asterisk deployment and most PCs, routers, smartphones, and VPN-compatible soft phones and SIP phones including Yealink, Grandstream, Snom, and many more. And the really great news is that OpenVPN clients can coexist with your current NeoRouter VPN.
Finally, a word about the OpenVPN Client installations below. We’ve tested all of these with current versions of Incredible PBX 13-13, 16-15, and Incredible PBX 2020. They should work equally well with other server platforms which have been properly configured. However, missing dependencies on other platforms are, of course, your responsibility.
Building an OpenVPN Server Platform
There are many ways to create an OpenVPN server platform. The major prerequisites are a supported operating system, a static IP address for your server, and a platform that is extremely reliable and always available. If the server is off line, all client connections will also fail. While we obviously have not tested all the permutations and combinations, we have identified a platform that just works™. It’s the CentOS 7, 64-bit cloud offering from Vultr. If you use our referral link at Vultr, you not only will be supporting Nerd Vittles through referral revenue, but you also will be able to take advantage of their $50 free credit for new customers. For home and small business deployments, we have found the $5/month platform more than adequate, and you can add automatic backups for an additional $1 a month. Cheap insurance!
To get started, create your CentOS 7 Vultr instance and login as root using SSH or Putty. Immediately change your password and update and install the necessary CentOS 7 packages:
passwd yum -y update yum -y install net-tools nano wget tar iptables-services systemctl stop firewalld systemctl disable firewalld systemctl enable iptables
We recommend keeping your OpenVPN server platform as barebones as possible to reduce the vulnerability risk. By default, this installer routes all client traffic through the VPN server which wastes considerable bandwidth. The sed commands below modify this design to only route client VPN traffic through the OpenVPN server.
cd /root curl -O https://raw.githubusercontent.com/Angristan/openvpn-install/master/openvpn-install.sh chmod +x openvpn-install.sh sed -i "s|\\techo 'push \\"redirect-gateway|#\\techo 'push \\"redirect-gateway|" openvpn-install.sh sed -i "s|push \\"redirect-gateway|#push \\"redirect-gateway|" openvpn-install.sh sed -i 's|tls-client|tls-client\\npull-filter ignore "redirect-gateway"|' openvpn-install.sh ./openvpn-install.sh
Here are the recommended entries in running the OpenVPN installer:
- Server IP Address: using FQDN strongly recommended to ease migration issues
- Enabled IPv6 (no): accept default
- Port (1194): accept default
- Protocol (UDP): accept default
- DNS (3): change to 9 (Google)
- Compression (no): accept default
- Custom encrypt(no): accept default
- Generate Server
- Client name: firstclient
- Passwordless (1): accept default
In the following steps, we will use IPtables to block all server access except via SSH or the VPN tunnel. Then we’ll start your OpenVPN server:
cd /etc/sysconfig wget http://incrediblepbx.com/iptables-openvpn.tar.gz tar zxvf iptables-openvpn.tar.gz rm -f iptables-openvpn.tar.gz echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf sysctl -p systemctl -f enable openvpn@server.service systemctl start openvpn@server.service systemctl status openvpn@server.service systemctl enable openvpn@server.service systemctl restart iptables
Once OpenVPN is enabled, the server can be reached through the VPN at 10.8.0.1. OpenVPN clients will be assigned by DHCP in the range of 10.8.0.2 through 10.8.0.254. You can list your VPN clients like this: cat /etc/openvpn/ipp.txt. You can list active VPN clients like this: cat /var/log/openvpn/status.log | grep 10.8. And you can add new clients or delete old ones by rerunning /root/openvpn-install.sh.
For better security, change the SSH access port replacing 1234 with desired port number:
PORT=1234 sed -i "s|#Port 22|Port $PORT|" /etc/ssh/sshd_config systemctl restart sshd sed -i "s|dport 22|dport $PORT|" /etc/sysconfig/iptables systemctl restart iptables
04/16 UPDATE: We’ve made changes in the Angristan script to adjust client routing. By default, all packets from every client flowed through the OpenVPN server which wasted considerable bandwidth. Our preference is to route client packets destined for the Internet directly to their destination rather than through the OpenVPN server. The sed commands added to the base install above do this; however, if you’ve already installed and run the original Angristan script, your existing clients will be configured differently. Our recommendation is to remove the existing clients, make the change below, and then recreate the clients again by rerunning the script. In the alternative, you can execute the command below to correct future client creations and then run it again on each existing client platform substituting the name of the /root/.ovpn client file for client-template.txt and then restart each OpenVPN client.
cd /etc/openvpn sed -i 's|tls-client|tls-client\\npull-filter ignore "redirect-gateway"|' client-template.txt
Creating OpenVPN Client Templates
In order to assign different private IP addresses to each of your OpenVPN client machines, you’ll need to create a separate client template for each computer. You do this by running /root/openvpn-install.sh again on the OpenVPN server. Choose option 1 to create a new .ovpn template. Give each client machine template a unique name and do NOT require a password for the template. Unless the client machine is running Windows, edit the new .ovpn template and comment out the setenv line: #setenv. Save the file and copy it to the /root folder of the client machine. Follow the instructions below to set up OpenVPN on the client machine and before starting up OpenVPN replace firstclient.ovpn in the command line with the name of .ovpn you created for the individual machine.

Renewing OpenVPN Server’s Expired Certificate
The server certificate will expire after 1080 days, and clients will no longer be able to connect. Here’s what to do next:
systemctl stop openvpn@server.service cd /etc/openvpn/easy-rsa ./easyrsa gen-crl cp /etc/openvpn/easy-rsa/pki/crl.pem /etc/openvpn/crl.pem systemctl start openvpn@server.service
Installing an OpenVPN Client on CentOS/RHEL
cd /root yum -y install epel-release yum --enablerepo=epel install openvpn -y # copy /root/firstclient.ovpn from server to client /root # and then start up the VPN client openvpn --config /root/firstclient.ovpn --daemon # adjust Incredible PBX 13-13 firewall below iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT cd /usr/local/sbin echo "iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT" >> iptables-custom
Running ifconfig should now show the VPN client in the list of network ports:
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.2 P-t-P:10.8.0.2 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:9 errors:0 dropped:0 overruns:0 frame:0
TX packets:39 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:855 (855.0 b) TX bytes:17254 (16.8 KiB)
And you should be able to login to the VPN server using its VPN IP address:
# enter actual SSH port replacing 1234 PORT=1234 ssh -p $PORT root@10.8.0.1
Installing an OpenVPN Client on Ubuntu 18.04.2
cd /root apt-get update apt-get install openvpn unzip dpkg-reconfigure tzdata # copy /root/firstclient.ovpn from server to client /root # and then start up the VPN client openvpn --config /root/firstclient.ovpn --daemon # adjust Incredible PBX 13-13 firewall below iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT cd /usr/local/sbin echo "iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT" >> iptables-custom
Running ifconfig should now show the VPN client in the list of network ports:
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.2 P-t-P:10.8.0.2 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:9 errors:0 dropped:0 overruns:0 frame:0
TX packets:39 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:855 (855.0 b) TX bytes:17254 (16.8 KiB)
And you should be able to login to the VPN server using its VPN IP address:
# enter actual SSH port replacing 1234 PORT=1234 ssh -p $PORT root@10.8.0.1
Installing an OpenVPN Client on Raspbian
Good news and bad news. First the bad news. Today’s OpenVPN server won’t work because of numerous unavailable encryption modules on the Raspberry Pi side. The good news is that NeoRouter is a perfect fit with Raspbian, and our upcoming article will show you how to securely interconnect a Raspberry Pi with any Asterisk server in the world… at no cost.
04/16 Update: We now have OpenVPN working with Incredible PBX for the Raspberry Pi. The trick is that you’ll need to build the latest version of OpenVPN from source before beginning the client install. Here’s how. Login to your Raspberry Pi as root and issue these commands:
apt-get remove openvpn apt-get update apt-get install libssl-dev liblzo2-dev libpam0g-dev build-essential -y cd /usr/src wget https://swupdate.openvpn.org/community/releases/openvpn-2.4.7.tar.gz tar zxvf openvpn-2.4.7.tar.gz cd openvpn-2.4.7 ./configure --prefix=/usr make make install openvpn --version
Now you should be ready to install a client config file, start up OpenVPN, and adjust firewall:
cd /root dpkg-reconfigure tzdata # copy /root/firstclient.ovpn from server to client /root # and then start up the VPN client openvpn --config /root/firstclient.ovpn --daemon # adjust Incredible PBX 13-13 firewall below iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT cd /usr/local/sbin echo "iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT" >> iptables-custom
Installing an OpenVPN Client on a Mac
While there are numerous OpenVPN clients for Mac OS X, none hold a candle to Tunnelblick in terms of ease of installation and use. First, create a new client config on your server and copy it (/root/*.ovpn) to a folder on your Mac where you can find it. Download Tunnelblick and install it. Run Tunnelblick and then open Finder. Click and drag your client config file to the Tunnelblick icon in the top toolbar. Choose Connect when prompted. Done.
Installing an OpenVPN Client for Windows 10
The installation procedure for Windows is similar to the Mac procedure above. Download the OpenVPN Client for Windows. Double-click on the downloaded file to install it. Create a new client config on your server and copy it (/root/*.ovpn) to a folder on your PC where you can find it. Start up the OpenVPN client and click on the OpenVPN client in the activity tray. Choose Import File and select the config file you downloaded from your OpenVPN Server. Right-click on the OpenVPN icon again and choose Connect. Done.
Installing an OpenVPN Client for Android
Our favorite OpenVPN client for Android is called OpenVPN for Android and is available in the Google Play Store. Download and install it as you would any other Android app. Upload a client config file from your OpenVPN server to your Google Drive. Run the app and click + to install a new profile. Navigate to your Google Drive and select the config file you uploaded.
Installing an OpenVPN Client for iOS Devices
The OpenVPN Connect client for iOS is available in the App Store. Download and install it as you would any other iOS app. Before uploading a client config file, open the OpenVPN Connect app and click the 4-bar Settings icon in the upper left corner of the screen. Click Settings and change the VPN Protocol to UDP and IPv6 to IPV4-ONLY Tunnel. Accept remaining defaults.
To upload a client config file, the easiest way is to use Gmail to send yourself an email with the config file as an attachment. Open the message with the Gmail app on your iPhone or iPad and click on the attachment. Then choose the Upload icon in the upper right corner of the dialog. Next, choose Copy to OpenVPN in the list of apps displayed. When the import listing displays in OpenVPN Connect, click Add to import the new profile. Click ADD again when the Profile has been successfully imported. You’ll be prompted for permission to Add VPN Configurations. Click Allow. Enter your iOS passcode when prompted. To connect, tap once on the OpenVPN Profile. To disconnect, tap on the Connected slider. When you reopen the OpenVPN Connect app, the OVPN Profiles menu will display by default. Simply tap once on your profile to connect thereafter.
Installing a Web Interface to Display Available Clients
One advantage of NeoRouter is a simple way for any VPN client to display a listing of all VPN clients that are online at any given time. While that’s not possible with OpenVPN, we can do the next best thing and create a simple web page that can be accessed using a browser but only from a connected OpenVPN client pointing to http://10.8.0.1.
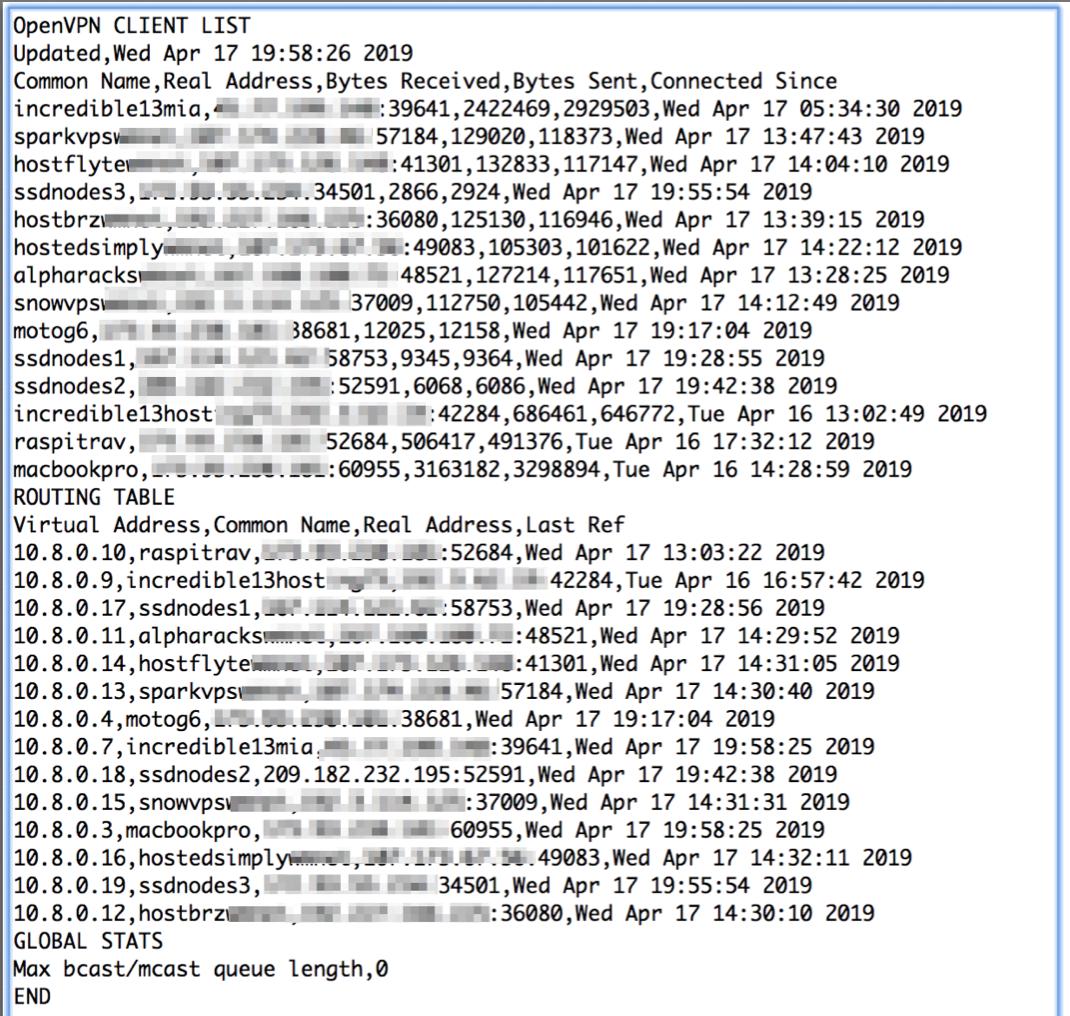
To set this up, log in to your OpenVPN server as root and issue the following commands:
yum --enablerepo=epel install lighttpd -y systemctl start lighttpd.service systemctl enable lighttpd.service chown root:lighttpd /var/log/openvpn/status.log chmod 640 /var/log/openvpn/status.log cd /var/www rm -rf lighttpd wget http://incrediblepbx.com/lighttpd.tar.gz tar zxvf lighttpd.tar.gz ln -s /var/log/openvpn/status.log /var/www/lighttpd/status.log sed -i 's|#server.bind = "localhost"|server.bind = "10.8.0.1"|' /etc/lighttpd/lighttpd.conf systemctl restart lighttpd.service
Latest VPN Security Alerts
https://nakedsecurity.sophos.com/2019/04/16/security-weakness-in-popular-vpn-clients/
Originally published: Monday, April 15, 2019 Updated: Saturday, February 29, 2020

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

- Our discussion today is focused on the free, MIT-licensed version of OpenVPN. For details on their commercial offerings, follow this link. [↩]
Cell Phone Tips for Spring Break and International Travel

With Spring Break upon us and Summer Vacations just around the corner, we wanted to briefly review some of your cellphone and data options for those that might be planning a trip outside the United States. If you’re only going as far as Mexico, Canada, or the U.S. Virgin Islands, then your existing cellular provider in the U.S. may have you covered at no additional cost. If your provider is not AT&T, then check with your carrier. And speaking of AT&T, if you’ll only be outside these covered areas for a brief time, then you may wish to consider enabling AT&T’s International Day Pass which costs you nothing until you use it. On days that you use it in over 100 countries, it’s $10/day with the same talk, text, and data options you currently have in the U.S. No, it’s not a bargain for a 60-day vacation, but it’s a pretty good deal for a week or so when you only need cell service for a few days. No changes in your current AT&T plan are necessary other than enabling the International Day Pass feature. Click on the Get Started Link to enable the service. Be sure to read the fine print.
Once you get past the options in the first paragraph, most of the other economical choices for cell phone and data coverage internationally involve swapping out the SIM card in your phone with a country-specific SIM card from a local provider. The first step is to make absolutely certain that your cell phone is unlocked before you hop on a plane. The procedure varies with different providers so you’ll need to investigate what steps are required. Be sure to also decipher how to verify that your phone is unlocked. Again, with AT&T, it’s a simple matter of visiting their web site and filling out a form. Within 24 hours, you should be good to go.
Now comes the hard part, choosing an alternate provider meeting your travel requirements. This turns on a number of factors such as whether callers in the U.S. need to contact you using a U.S. phone number. If so, then the first paragraph is your best bet if you need to be reached on your existing phone number. If any U.S. phone number will suffice (and you can always forward your cellphone number to this new number), then using an Android phone or iPhone, there’s an easy solution if you have Wi-Fi access or some cellphone data to burn. Simply use a Google Voice phone number and associate it with the new Android or iPhone Google Voice app on your phone. Be sure to enable WiFi/Mobile Data calling in GV Settings, and you’re good to go with almost any smart phone with 4G service. With Wi-Fi, no SIM card is required. Just put your phone in Airplane Mode and enjoy free calling back to the U.S. and Canada.
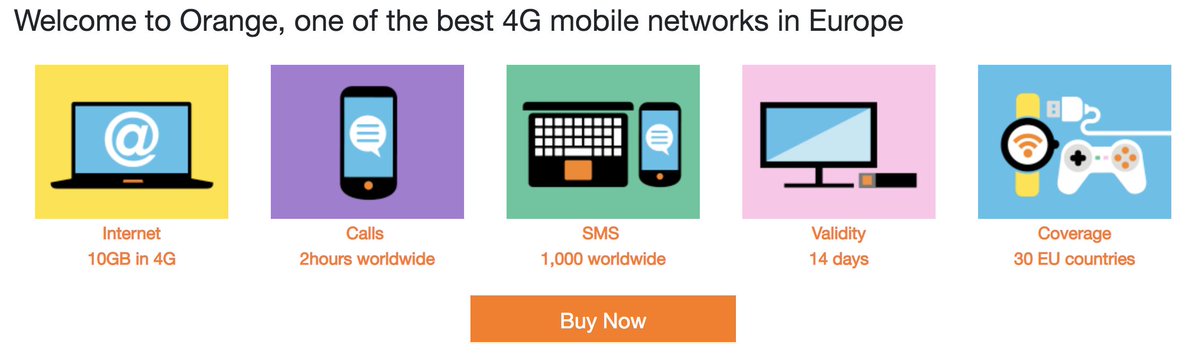
The next issue to consider is whether you need to make frequent calls or send frequent text messages to those in the U.S. while you are away. If so, then the best choice we’ve found without Wi-Fi access is Orange Holiday Europe.1 Simply buy the $50 card and put it in your cellphone on the day you wish to begin your service. It buys you 10GB of data, 2 hours of calls, and 1000 text messages to almost any phone in the world from 30 European countries including the U.K. Once activated, the card is good for 14 days and includes tethering. It can be renewed for an additional 21.70€ (about $25) which adds another 14 days with an additional 10GB of data, 120 minutes of calls, and another 1,000 SMS messages.
If the phone number of your calls doesn’t matter and you can also take advantage of Google Voice for free calling to and from the U.S., then all you really need is the cheapest SIM card you can find in the country you’re visiting. One word of advice from our frequent traveler friends is don’t buy the SIM card in the airport where they typically are two to five times as expensive. To give you an example, a SIM card with 5GB of data in Madrid can be had for about 10€ per week. For iPhone users, a more flexible SIM card that looked appealing to us was Gigsky which offers regional SIM cards for anywhere in the world. Enjoy your vacation!
Originally published: Monday, March 25, 2019
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

- Many of our purchase links refer users to Amazon when we find their prices are competitive for the recommended products. Nerd Vittles receives a small referral fee from Amazon to help cover the costs of our blog. We never recommend particular products solely to generate Amazon commissions. However, when pricing is comparable or availability is favorable, we support Amazon because Amazon supports us. [↩]
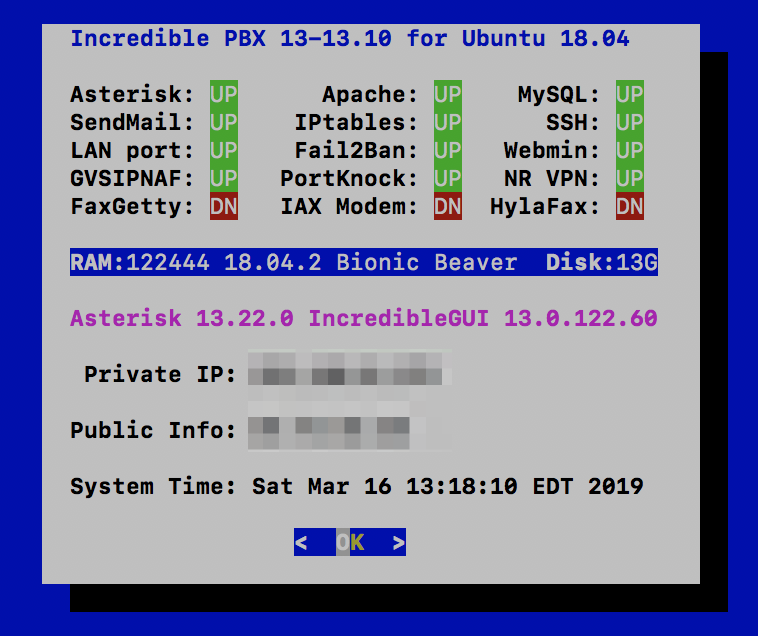
A Golden Newbie: Incredible PBX 13-13.10 for Ubuntu 18.04.2

If you’re as big a fan of Ubuntu as we are, then you’ll be pleased to know that the month-old update to Ubuntu 18.04 LTS is rock-solid. It takes a brave soul to name anything Bionic Beaver, but Ubuntu pulls it off and makes you want to meet one face-to-face, just not in a bar after midnight. Well, St. Paddy would be proud. Today’s new Incredible PBX® 13-13.10 release brings you everything you could want in a PBX, and the icing on the cake is Ubuntu 18.04.2. The only drawback to Ubuntu 18.04 is that none of our $1/month VPS cloud providers support the platform just yet. But have no fear, both Digital Ocean and Vultr already do.1
Introducing 2019 Edition of Incredible PBX
This is our third major release of our flagship Incredible PBX 13-13 platform. In addition to today’s release for Ubuntu 18.04.2, it’s also available for Raspbian 8 as well as CentOS 6 and 7. It features 70+ new FreePBX® GPL modules plus all the latest components for OSS Endpoint Manager making SIP phone deployment with Asterisk® 13 a breeze. There also are terrific new backup and restore utilities which make migration and restoration of Incredible PBX platforms a snap. Finally, we’ve incorporated Skyetel SIP trunking in the build. It literally makes configuration of outbound and incoming calling a one-minute process. On the Skyetel side, create an Endpoint Group pointing to the IP address of your PBX, order one or more DIDs and point them to the new EndPoint Group. Done. On the Incredible PBX side, add Inbound Routes specifying the 11-digit numbers of your Skyetel DIDs and point each of them to the desired destination for incoming calls. Done. Outbound calls are automatically configured to use your Skyetel account. Our complete Skyetel tutorial is available here and includes up to a $250 usage credit with Skyetel’s new BOGO deposit match.2 Effective 10/1/2023, $25/month minimum spend required.
Creating an Ubuntu 18.04.2 Platform
If you plan to install Incredible PBX 13-13.10 using a cloud provider that supports Ubuntu 18.04.2, then creation of the Ubuntu 18.04.2 platform is as simple as clicking on the 64-bit OS as part of the creation of your 1GB RAM virtual machine. If you plan to use your own hardware, then any modern desktop computer will suffice. Begin by downloading the Ubuntu 18.04.2 ISO from here. Then create a bootable USB stick or assign the ISO as the boot device on your virtual machine platform. Here are steps for Ubuntu install using the server console:
- Preferred language: English
- Keyboard: English (US)
- Install Ubuntu
- Network interface (eth or wlan) from DHCP
- Proxy (leave blank)
- Ubuntu mirror (accept default entry)
- Partitioning: Use Entire Disk
- Choose Disk for Install (accept default usually)
- File System Setup (choose Done)
- Confirm Disk Install (Continue)
- Profile Setup (create a username and password)
- Install OpenSSH server (press Space Bar then Done)
- Featured Server Snaps (leave blank)
- Reboot Now (when prompted)
- Remove installation media
- Login using username created above
- sudo passwd root
- exit
- Login as root with new root password
- userdel username (that you created above)
- nano -w /etc/ssh/sshd_config
- Add: PermitRootLogin yes
- save file
- exit
- Login as root using SSH or Putty
CAUTION: Don’t make any "improvements" to Ubuntu 18.04.2 after the initial install, or the Incredible PBX install may fail. It is designed for a base platform only!
Installing Incredible PBX 13-13.10
If you haven’t already done so, log into your Ubuntu 18.04.2 server as root using SSH or Putty. It’s important to log in from a desktop computer that you will be using to make changes on your server since this IP address will be whitelisted in the firewall as part of the installation process. Do NOT use the server console to install Incredible PBX, or you may not be able to log in from your desktop computer thereafter.
Before we begin the install procedure, let’s determine whether a swap file exists on your platform. If not, you’ll need to create one below as one of the first steps after downloading the Incredible PBX installer. Issue this command to determine if you have swap space: free -h
Now let’s download and install Incredible PBX 13-13.10. There are two flavors: the base install with the 70+ FreePBX GPL modules that comprise the web-based GUI to manage your PBX and the Whole Enchilada which adds 30+ Asterisk applications to the base install to provide TTS support, voice recognition, news and weather TTS apps, AsteriDex, telephone reminders, and much more. Here are the steps. Be sure to uncomment the create-swapfile-DO entry if you are lacking a swapfile.
cd /root wget http://incrediblepbx.com/incrediblepbx-13-13.10U-LEAN.tar.gz tar zxvf incrediblepbx-13-13.10U-LEAN.tar.gz rm -f incrediblepbx-13-13.10U-LEAN.tar.gz #./create-swapfile-DO ./Incredible*
There are two phases to the base install. You’ve just completed Phase #1. After your server reboots, log back in and kick off the Incredible PBX installer a second time. Don’t disappear immediately. On some cloud platforms, you may be asked whether to preserve your existing SSH setup. Choose the Keep Local Version default. On all platforms, you’ll be prompted for two additional responses in the first few minutes. At the first prompt, simply press ENTER to continue. At the second prompt, enter the country code to associate with your PBX. For those in the United States, the code is 1. We assume others are more familiar with their country code than Americans are. 😉
cd /root ./Incredible*
Make some careful notes when the install finishes. Then press ENTER to reboot your server.
If you don’t plan to use the Incredible PBX applications, then your install is complete after the reboot. Each time you log in to your server, the Automatic Update Utility will run to provide late-breaking updates that may affect the security of your server. So make sure you log in to the Linux CLI at least once a week to stay safe!
Assuming you’ve already created a very secure root password (update it by running passwd), perform the following 5 Steps to get everything locked down:
- Create an admin password for GUI access: /root/admin-pw-change
- Create an admin password for Apache web access: htpasswd /etc/pbx/wwwpasswd admin
- Configure the correct timezone for your server: /root/timezone-setup
- Retrieve your PortKnocker setup like this: cat /root/knock.FAQ
- Add IPtables WhiteList entries for remote access: /root/add-ip or /root/add-fqdn
Most of the configuration of your PBX will be performed using the web-based Incredible PBX GUI with its FreePBX 13 GPL modules. Use a browser pointed to the IP address of your server and choose Incredible PBX Admin. Log in as admin with the password you configured in the first step above. HINT: You can always change it if you happen to forget it.

To get a basic system set up so that you can make and receive calls, you’ll need to add a VoIP trunk, create one or more extensions, set up an inbound route to send incoming calls to an extension, and set up an outbound route to send calls placed from your extension to a VoIP trunk that connects to telephones in the real world. You’ll also need a SIP phone or softphone to use as an extension on your PBX.
Continue Reading: Configuring Extensions, Trunks & Routes

Installing Incredible PBX 13-13 Whole Enchilada
There now are two more pieces to put in place. The sequence matters! Be sure to upgrade to the Whole Enchilada before you install Incredible Fax. If you perform the steps backwards, you may irreparably damage your fax setup by overwriting parts of it.
The Whole Enchilada upgrade script now is included in the Incredible PBX LEAN tarball. To run it, issue the following commands:
cd /root ./Enchilada*
If you accidentally installed Incredible Fax before upgrading to the Whole Enchilada, you may be able to recover your Incredible Fax setup by executing the following commands. It’s worth a try anyway.
amportal a ma install avantfax amportal a r
Installing Incredible Fax with HylaFax/AvantFax
You don’t need to upgrade to the Whole Enchilada in order to use Incredible Fax; however, you may forfeit the opportunity to later upgrade to the Whole Enchilada if you install Incredible Fax first. But the choice is completely up to you. To install Incredible Fax, log into your server as root and issue the following commands:
cd /root ./incrediblefax13_ubuntu18.sh
After entering your email address to receive incoming faxes, you’ll be prompted several times to choose options as part of the install. Simply press the ENTER key at each prompt and accept all of the defaults. When the install finishes, make certain that you reboot your server to bring Incredible Fax on line. There will be a new AvantFax option in the Incredible PBX GUI. The default credentials for AvantFax GUI are admin:password. Be advised that there remain a couple of quirks on the Ubuntu 18.04 platform. First, after entering your credentials, you may get a timeout error with your browser. Simply press the Reload/Refresh icon in your browser, and the default AvantFax menu will appear. Second, you will need to set your email delivery address and a new password for AvantFax manually. Click on the Settings option in the upper right corner of the dialog. When you save your settings, you may again experience a timeout event. Click the Reload/Refresh button on your browser again, and AvantFax will come back to life.
NAT-Based Router and Dynamic IP Wrinkles
If your PBX is sitting behind a NAT-based router, you’ll need to redirect incoming UDP 5060 traffic to the private IP address of your PBX. While this isn’t technically necessary to complete calls with registered trunk providers, there are others such as Skyetel that don’t use SIP registrations where failure to redirect UDP 5060 would cause inbound calls to fail.
The Incredible PBX GUI is accessed using a web browser pointed to the IP address of your server. As part of the password setup, you created an admin password for the Incredible PBX GUI, a.k.a. FreePBX GUI. Login now using your favorite browser. If you have forgotten your admin password, you can reset it by logging into your server as root using SSH: /root/admin-pw-change. Once you’ve logged into the GUI, your first task is to record the public and private IP addresses for your server. This eliminates 99% of the problems with one-way audio on calls where your server is sitting behind a NAT-based router. Navigate to Settings -> SIP Settings and click on Detect Network Settings in the NAT Settings section of the template. Verify that the entries shown are correct and then click Submit followed by Apply Config.
Many Internet service providers assign dynamic IP addresses to customers. This poses issues with a PBX because SIP phones positioned outside your LAN need to be able to connect to the PBX. It also complicates SIP routing which needs both the public IP address and the private IP address of the PBX in order to route calls properly. In the previous section, you configured your PBX with these two IP addresses. The problem, of course, is that this public IP address may change when your ISP assigns dynamic IP addresses. Luckily, many ISPs rarely update dynamic IP addresses of their customers. For example, our home network has had the same dynamic IP address for more than four years. If this is your situation, then you have little to worry about. If the IP address ever changes, you can simply repeat the steps in the previous section. However, if your ISP regularly changes your public IP address, then you need an automatic way to keep your PBX configured properly. Otherwise you will start experiencing calls with one-way audio or no audio, and remote phones will no longer be able to connect to the PBX. We’ve developed a script to update the public IP address of your PBX. Depending upon your situation, all you need to do is run it hourly or daily to keep your PBX configured properly. To begin, first download the updater script after logging into your server as root:
cd /root wget http://incrediblepbx.com/update-externip.tar.gz tar zxvf update-externip.tar.gz rm -f update-externip.tar.gz
Try running the script once to make sure it correctly identifies the public IP address of your server: /root/update-externip. Then add an entry to the end of /etc/crontab that schedules the script to run at 12:30 a.m. each night:
30 0 * * * root /root/update-externip > /dev/null 2>&1
Configuring Trunks with Incredible PBX
Before you can actually make and receive calls, you’ll need to add one or more VoIP trunks with providers, create extensions for your phones, and add inbound and outbound routes that link your extensions to your trunks. Here’s how a PBX works. Phones connect to extensions. Extensions connect to outbound routes that direct calls to specific trunks, a.k.a. commercial providers that complete your outbound calls to any phone in the world. Coming the other way, incoming calls are directed to your phone number, otherwise known as a DID. DIDs are assigned by providers. Some require trunk registration using credentials handed out by these providers. Others including Skyetel use the IP address of your PBX to make connections. Incoming calls are routed to your DIDs which use inbound routes telling the PBX how to direct the calls internally. A call could go to an extension to ring a phone, or it could go to a group of extensions known as a ring group to ring a group of phones. It could also go to a conference that joins multiple people into a single call. Finally, it could be routed to an IVR or AutoAttendant providing a list of options from which callers could choose by pressing various keys on their phone.
We’ve done most of the prep work for you with Incredible PBX. We’ve set up an Extension to which you can connect a SIP phone or softphone. We’ve set up an Inbound Route that, by default, sends all incoming calls from registered trunks to a Demo IVR. And we’ve built dozens of trunks for some of the best providers in the business. Sign up with the ones you prefer, plug in your credentials, and you’re done. The next section of this tutorial will show you the easier way, using Skyetel.
Unlike traditional telephone service, you need not and probably should not put all your eggs in one basket when it comes to telephone providers. In order to connect to Plain Old Telephones, you still need at least one provider. But there is nothing wrong with having several. And a provider that handles an outbound call (termination) need not be the same one that handles an incoming call (origination) and provides your phone number (DID). Keep in mind that you only pay for the calls you make with each provider so you have little to lose by choosing several. The PIAF Forum also has dozens of recommendations on VoIP providers.
With the preconfigured trunks in Incredible PBX, all you need are your credentials for each provider and the domain name of their server. Log into Incredible PBX GUI Administration as admin using a browser. From the System Status menu, click Connectivity -> Trunks. Click on each provider you have chosen and fill in your credentials including the host entry. Be sure to uncheck the Disable Trunk checkbox! Fill in the appropriate information for the Register String. Save your settings by clicking Submit Changes. Then click the red Apply Config button.

Using Skyetel with Incredible PBX
On the Raspberry Pi platform, all of the Skyetel trunks are preconfigured. All you need to do is sign up for Skyetel service in March to take advantage of the $50 Nerd Vittles special offer. First, complete the Prequalification Form here. You then will be provided a link to the Skyetel site to complete your registration. Once you have registered on the Skyetel site and your account has been activated, open a support ticket and request a $50 credit for your account by referencing the Nerd Vittles special offer. Greed will get you nowhere. Credit is limited to one per person/company/address/location. You can also take advantage of a 10% discount on your current service. Just open another ticket and attach a copy of your last month’s bill. See footnote 3 for the fine print.3 If you have high call volume requirements, document these in your Prequalification Form, and we will be in touch.
Unlike many VoIP providers, Skyetel does not use SIP registrations to make connections to your PBX. Instead, Skyetel utilizes Endpoint Groups to identify which servers can communicate with the Skyetel service. An Endpoint Group consists of a Name, an IP address, a UDP or TCP port for the connection, and a numerical Priority for the group. For incoming calls destined to your PBX, DIDs are associated with an Endpoint Group to route the calls to your PBX. For outgoing calls from your PBX, a matching Endpoint Group is required to authorize outbound calls through the Skyetel network. Thus, the first step in configuring the Skyetel side for use with your PBX is to set up an Endpoint Group. A typical setup for use with Incredible PBX®, Asterisk®, or FreePBX® would look like the following:
- Name: MyPBX
- Priority: 1
- IP Address: PBX-Public-IP-Address
- Port: 5060
- Protocol: UDP
- Description: server1.incrediblepbx.com
To receive incoming PSTN calls, you’ll need at least one DID. On the Skyetel site, you acquire DIDs under the Phone Numbers tab. You have the option of Porting in Existing Numbers (free for the first 60 days after you sign up for service) or purchasing new ones under the Buy Phone Numbers menu option.
Once you have acquired one or more DIDs, navigate to the Local Numbers or Toll Free Numbers tab and specify the desired SIP Format and Endpoint Group for each DID. Add SMS/MMS and E911 support, if desired. Call Forwarding and Failover are also supported. That completes the VoIP setup on the Skyetel side. System Status is always available here.
Configuring a Skyetel Inbound Route
Because there is no SIP registration with Skyetel, incoming calls to Skyetel trunks will NOT be sent to the Default Inbound Route configured on your PBX because FreePBX treats the calls as blocked anonymous calls without an Inbound Route pointing to the 11-digit number of each Skyetel DID. From the GUI, choose Connectivity -> Inbound Routes. You will note that we already have configured a Skyetel template for you. Simply edit the existing entry and plug in the 11-digit phone number (beginning with a 1) of your Skyetel DID . Set the Destination for the incoming DID as desired and click Submit. It defaults to extension 701.
If your PBX is sitting behind a NAT-based router, you’ll need to redirect incoming UDP 5060 traffic to the private IP address of your PBX. Then place a test call to each of your DIDs after configuring the Inbound Routes.
If you have installed the Incredible Fax add-on, you can enable Fax Detection under the Fax tab. And, if you’d like CallerID Name lookups using CallerID Superfecta, you can enable it under the Other tab before saving your setup and reloading your dialplan.
Configuring a Skyetel Outbound Route
If Skyetel will be your primary provider, it is preconfigured by default on the Raspberry Pi platform so you can use both 10-digit and 11-digit dialing to process outbound calls through your Skyetel account. If you prefer another setup, choose Connectivity -> Outbound Routes.
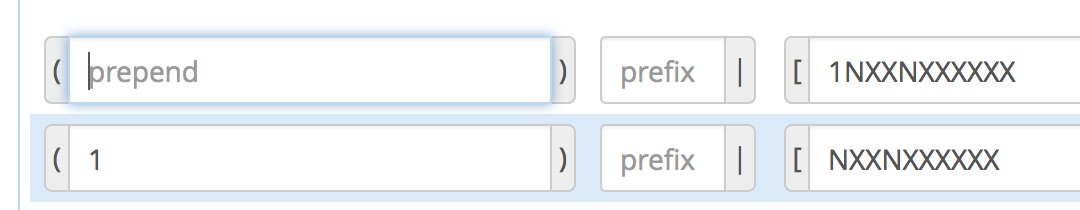
There are a million ways to design outbound calling schemes on PBXs with multiple trunks. One of the simplest ways is to use no dial prefix for the primary trunk and then use dialing prefixes for the remaining trunks.
Another outbound calling scheme would be to assign specific DIDs to individual extensions on your PBX. Here you could use NXXNXXXXXX with the 1 Prepend as the Dial Pattern with every Outbound Route and change the Extension Number in the CallerID field of the Dial Pattern. With this setup, you’d need a separate Outbound Route for each group of extensions using a specific trunk on your PBX. Additional dial patterns can be added for each extension designated for a particular trunk. A lower priority Outbound Route then could be added without a CallerID entry to cover extensions that weren’t restricted or specified.
HINT: Keep in mind that Outbound Routes are processed by FreePBX in top-down order. The first route with a matching dial pattern is the trunk that is selected to place the outbound call. No other outbound routes are ever used even if the call fails or the trunk is unavailable. To avoid failed calls, consider adding additional trunks to the Trunk Sequence in every outbound route. In summary, if you have multiple routes with the exact same dial pattern, then the match nearest to the top of the Outbound Route list wins. You can rearrange the order of the outbound routes by dragging them into any sequence desired.
Audio Issues with Skyetel
If you experience one-way or no audio on some calls, make sure you have filled in the NAT Settings section in the GUI under Settings -> Asterisk SIP Settings -> General. In addition to adding your external and internal IP addresses there, be sure to add your external IP address in /etc/asterisk/sip_general_custom.conf like the following example and restart Asterisk:
externip=xxx.xxx.xxx.xxx
If you’re using PJSIP trunks or extensions on your PBX, implement this fix as well.
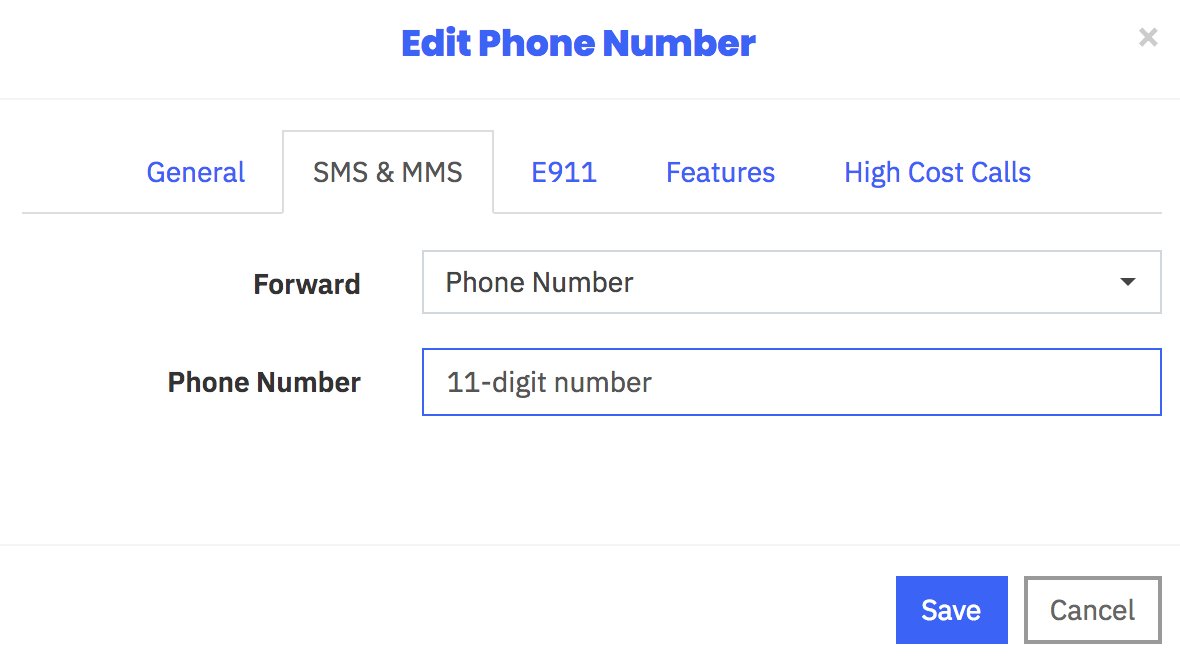
Receiving SMS Messages Through Skyetel
Most Skyetel DIDs support SMS messaging. Once you have purchased one or more DIDs, you can edit each number and, under the SMS & MMS tab, you can redirect incoming SMS messages to an email or SMS destination of your choice using the following example:
Sending SMS Messages Through Skyetel
We’ve created a simple script that will let you send SMS messages from the Linux CLI using your Skyetel DIDs. In order to send SMS messages, you first will need to create an SID key and password in the Skyetel portal. From the Settings icon, choose API Keys -> Create. Once the credentials appear, copy both your SID and Password. Then click SAVE.
Next, from the Linux CLI, issue the following commands to download the sms-skyetel script into your /root folder. Then edit the file and insert your SID, secret, and DID credentials in the fields at the top of the script. Save the file, and you’re all set.
cd /root wget http://incrediblepbx.com/sms-skyetel chmod +x sms-skyetel nano -w sms-skyetel
To send an SMS message, use the following syntax where 18005551212 is the 11-digit SMS destination: sms-skyetel 18005551212 "Some message"
Configuring a Softphone for Incredible PBX
We’re in the home stretch now. You can connect virtually any kind of telephone to your new PBX. Plain Old Phones require an analog telephone adapter (ATA) which can be a separate board in your computer from a company such as Digium. Or it can be a standalone SIP device such as ObiHai’s OBi100 or OBi110 (if you have a phone line from Ma Bell to hook up as well). SIP phones can be connected directly so long as they have an IP address. These could be hardware devices or software devices such as the YateClient softphone. We’ll start with a free one today so you can begin making calls. You can find dozens of recommendations for hardware-based SIP phones both on Nerd Vittles and the PIAF Forum when you’re ready to get serious about VoIP telephony.
We recommend YateClient which is free. Download it from here. Run YateClient once you’ve installed it and enter the credentials for the 701 extension on Incredible PBX. You’ll need the IP address of your server plus your extension 701 password. Choose Applications _> Extensions -> 701 and write down your SIP/IAX Password. You can also reset it by running /root/update-passwords. Fill in the blanks using the IP address of your Server, 701 for your Username, and whatever Password you assigned to the extension when you installed Incredible PBX. Click OK to save your entries.

Once you are registered to extension 701, close the Account window. Then click on YATE’s Telephony Tab and place some test calls to the numerous apps that are preconfigured on Incredible PBX. Dial a few of these to get started:
DEMO - Apps Demo
123 - Reminders
947 - Weather by ZIP Code
951 - Yahoo News
*61 - Time of Day
TODAY - Today in History
If you are a Mac user, another great no-frills softphone is Telephone. Just download and install it from the Mac App Store.
Upgrading to IBM Speech Engines
If you’ve endured Google’s Death by a Thousand Cuts with text-to-speech (TTS) and voice recognition (STT) over the years, then we don’t have to tell you what a welcome addition IBM’s new speech utilities are. We can’t say enough good things about the new IBM Watson TTS and STT offerings. With IBM’s services, you have a choice of free or commercial tiers. Let’s put the pieces in place so you’ll be ready to play with the Whole Enchilada.
Getting Started with IBM Watson TTS Service
We’ve created a separate tutorial to walk you through obtaining and configuring your IBM Watson credentials. Start there.
Next, login to your Incredible PBX server and issue these commands to update your Asterisk dialplan and edit ibmtts.php:
cd /var/lib/asterisk/agi-bin ./install-ibmtts-dialplan.sh nano -w ibmtts.php
Insert your credentials in $IBM_username and $IBM_password. For new users, your $IBM_username will be apikey. Your $IBM_password will be the TTS APIkey you obtained from IBM. Next, verify that $IBM_url matches the entry provided when you registered with IBM. Then save the file: Ctrl-X, Y, then ENTER. Now reload the Asterisk dialplan: asterisk -rx "dialplan reload". Try things out by dialing 951 (news) or 947 (Weather) from an extension registered on your PBX.
Getting Started with IBM Watson STT Service
Now let’s get IBM’s Speech to Text service activated. Log back in to the IBM Cloud. Click on the Speech to Text app. Choose a Region to deploy in, choose your Organization from the pull-down menu, and select STT as your Space. Choose the Standard Pricing Plan. Then click Create. When Speech to Text Portal opens, click the Service Credentials tab. In the Actions column, click View Credentials and copy down your STT username and password.
Finally, login to your Incredible PBX server and issue these commands to edit getnumber.sh:
cd /var/lib/asterisk/agi-bin nano -w getnumber.sh
Insert apikey as your API_USERNAME and your actual STT APIkey API_PASSWORD in the fields provided. Then save the file: Ctrl-X, Y, then ENTER. Update your Voice Dialer (411) to use the new IBM STT service:
sed -i '\\:// BEGIN Call by Name:,\\:// END Call by Name:d' /etc/asterisk/extensions_custom.conf sed -i '/\\[from-internal-custom\]/r ibm-411.txt' /etc/asterisk/extensions_custom.conf asterisk -rx "dialplan reload"
Now try out the Incredible PBX Voice Dialer with AsteriDex by dialing 411 and saying "Delta Airlines."
Transcribing Voicemails with IBM Watson STT Service
We’ve included the necessary script to transcribe your incoming voicemails using IBM’s STT service. Navigate to the /usr/local/sbin folder and edit sendmailmp3.ibm. Insert your APIKEY in the password field and save the file. Now copy the file to sendmailmp3 and make the file executable: chmod +x sendmailmp3.
Using Gmail as a SmartHost for SendMail
Many Internet service providers block email transmissions from downstream servers (that’s you) to reduce spam. The simple solution is to use your Gmail account as a smarthost for SendMail. Here’s how. Log into your server as root and issue the following commands:
cd /etc/mail hostname -f > genericsdomain touch genericstable makemap -r hash genericstable.db < genericstable mv sendmail.mc sendmail.mc.original wget http://incrediblepbx.com/sendmail.mc.gmail cp sendmail.mc.gmail sendmail.mc mkdir -p auth chmod 700 auth cd auth echo AuthInfo:smtp.gmail.com \\"U:smmsp\\" \\"I:user_id\\" \\"P:password\\" \\"M:PLAIN\\" > client-info echo AuthInfo:smtp.gmail.com:587 \\"U:smmsp\\" \\"I:user_id\\" \\"P:password\\" \\"M:PLAIN\\" >> client-info echo AuthInfo:smtp.gmail.com:465 \\"U:smmsp\\" \\"I:user_id\\" \\"P:password\\" \\"M:PLAIN\\" >> client-info nano -w client-info
When the nano editor opens the client-info file, change the 3 user_id entries to your Gmail account name without @gmail.com and change the 3 password entries to your actual Gmail password. Save the file: Ctrl-X, Y, then ENTER.
Now issue the following commands. In the last step, press ENTER to accept all of the default prompts:
chmod 600 client-info makemap -r hash client-info.db < client-info cd .. sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.mc sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.mc sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/Makefile sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.cf sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/databases sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.mc.gmail sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.cf.errors make sendmailconfig
Finally, stop and restart SendMail and then send yourself a test message. Be sure to check your spam folder!
/etc/init.d/sendmail stop /etc/init.d/sendmail start apt-get install mailutils -y echo "test" | mail -s testmessage yourname@yourdomain.com
Check mail success with: tail /var/log/mail.log. If you have trouble getting a successful Gmail registration (especially if you have previously used this Google account from a different IP address), try this Google Voice Reset Procedure. It usually fixes connectivity problems. If it still doesn’t work, enable Less Secure Apps using this Google tool.
Configuring a SIP URI Address for Your PBX
Setting up a SIP URI is a simple way to let anyone with a SIP phone call you from anywhere in the world and talk for as long and as often as you like FOR FREE. The drawback of SIP URIs is typically the security risk accompanying the SIP exposure you must provide to receive these calls. Here's the safe way using what we call a hybrid SIP URI. It works like this. Sign up for a VoIP.ms account and create a subaccount that you will register using the VoIPms trunk included in Incredible PBX. As part of the setup in the VoIP.ms portal, assign an Internal Extension Number to your subaccount, e.g. 789123. Make it random so you don't get surprise calls from anonymous sources. The extension can be up to 10 digits long. Next, sign up for a free iNUM DID, e.g. 883510009901234, in your VoIP.ms account. Using Manage DIDs in the portal, link the iNUM DID to your subaccount and assign one of the VoIP.ms POP locations for incoming calls, e.g. atlanta.voip.ms. Next, write down your VoIP.ms account number, e.g. 12345. Once you've completed these three steps and registered the VoIP.ms subaccount on your PBX, you now have two SIP URIs that are protected by your VoIP.ms credentials and don't require you to expose your SIP port to the outside world at all. These SIP URIs can be pointed to different destinations by setting up Inbound Routes using your VoIP.ms account number as one DID and setting up your iNUM number as the second DID. To reach your PBX via SIP URI, callers can use 12345789123@atlanta.voip.ms to reach the DID you set up for your VoIP.ms subaccount where 12345 is your VoIP.ms account number and 789123 is the Internal Extension Number for your subaccount. Or callers can use 8835100099012234@inum.net to reach the DID you set up using your iNUM number that was assigned by VoIP.ms. Don't forget to whitelist the VoIP.ms POP's FQDN for SIP UDP access to your PBX:
/root/add-fqdn voipms atlanta.voip.ms
If you wish to make SIP URI calls yourself, the easiest way is to first set up a free LinPhone SIP Account. You can find dozens of recommendations for hardware-based SIP phones both on Nerd Vittles and the PIAF Forum. For today we'll get you started with one of our favorite (free) softphones, YateClient. It's available for almost all desktop platforms. Download YateClient from here. Run YateClient once you’ve installed it and enter the credentials for your LinPhone account. You’ll need LinPhone's FQDN (sip.linphone.org) plus your LinPhone account name and password. Fill in the Yate Client template and click OK to save your entries. Once the Yate softphone shows that it is registered, try a test call to one of our demo SIP URIs: sip:weather@demo.nerdvittles.com or sip:news@demo.nerdvittles.com.
Adding the NeoRouter Virtual Private Network
We've made it easy to set up a virtual private network between your PBX and your other computers. NeoRouter is a free VPN for up to 256 machines. It requires that you first set up a server for NeoRouter using a static IP address and preferably a fully-qualified domain name. This is covered in this Nerd Vittles tutorial. Once you have your NeoRouter server operational, adding your PBX to the VPN is easy. Simply run nrclientcmd and enter the FQDN of your VPN server together with your credentials. All clients on the VPN have an encrypted tunnel with private LAN addresses in the 10.0.0.x range. HINT: Setting up a NeoRouter VPN provides an easy way to get back into your server if the firewall ever locks you out since the 10.0.0.x subnet is automatically whitelisted as part of the initial install.
Using PortKnocker to Regain Access to Your PBX
And speaking of getting locked out of your server because you've forgotten to whitelist the IP address of your computer, there's another easy way to regain access: PortKnocker. The way the service works is you send sequential pings to 3 randomized TCP ports that are known only by you. They are listed in /etc/knock.FAQ. When your server detects a match, it will whitelist your new IP address allowing you to login using SSH or Putty. There also are PortKnocker utilities for both iOS and Android devices. Complete implementation details are available in this Nerd Vittles tutorial. If your PBX is sitting behind a router or firewall, don't forget to forward the three TCP ports from your router to the private LAN address of your PBX.

Planning Ahead for That Rainy Day
If you haven't already learned the hard way, let us save you from a future shock. Hardware fails. All of it. So spend an extra hour now so that you'll be prepared when (not if) disaster strikes. First, once you have your new PBX configured the way you plan to use it, make a backup of your PBX by running the Incredible Backup script: /root/incrediblebackup13
Copy down the name of the backup file that was created. You'll need it in a few minutes.
Second, build yourself a VirtualBox platform on your desktop PC using the Ubuntu ISO you previously downloaded. Once you complete the identical Incredible PBX install plus the Whole Enchilada upgrade and Incredible Fax (if used on your primary server), fire up the virtual machine and login as root with password as your password.
Next, create a /backup folder on your new VirtualBox PBX and copy the backup file from your main server to your VirtualBox server and restore it while logged into the VirtualBox PBX as root:
mkdir /backup scp root@main-pbx-ip-address:/backup/backup-file-name.tar.gz /backup/. /root/incrediblerestore13 /backup/backup-file-name.tar.gz
Verify that everything looks right by using a browser to access and review the settings in your new VirtualBox PBX. At a minimum, verify extensions, trunks, and routes.
Last but not least, if you're running Incredible PBX in the Cloud on Digital Ocean or Vultr, you can set up automatic backups of your server for only an extra dollar a month. It's the cheapest insurance your can buy. Enjoy!
Continue Reading: Configuring Extensions, Trunks & Routes
Don't Miss: Incredible PBX Application User's Guide covering the 31 Whole Enchilada apps
Originally published: Monday, March 18, 2019

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

- With some providers including Digital Ocean and Vultr, Nerd Vittles receives referral credits when you sign up for service. This assists in keeping the Nerd Vittles lights burning brightly. So... thank you. [↩]
- Skyetel is a Platinum Sponsor of Nerd Vittles and open source projects of Ward Mundy & Associates, LLC. [↩]
- In the unlikely event that Skyetel cannot provide a 10% reduction in your current origination rate and/or DID costs, Skyetel will give you an additional $50 credit to use with the Skyetel service. [↩]
Adding SIP URI Dialing to Asterisk for Free Worldwide Calling

Since giving up on Google Voice, we’ve been extolling the virtues of SIP URI dialing which gives you unlimited free calls to anyone else in the world that happens to have their own SIP URI address. SIP URIs look very much like email addresses except they’re used to share phone conversations instead of email messages. And, as we’ve mentioned previously, if everyone in the world had their own SIP URI, paying for phone calls would become a thing of the past. We hope you’ll join us in making that happen. As a fallback, give our $50 credit at Skyetel a try.
One of the drawbacks of Asterisk® PBXs using the FreePBX® GUI has been the inability to place outbound SIP URI calls from SIP phones registered as extensions on the PBX. Today we first want to address that shortcoming. Our SIP URI dialing solution for Asterisk should work with any FreePBX-based implementation including Incredible PBX® and Issabel as well as on Raspberry Pi platforms. We’ll wrap things up by providing some tips on obtaining and deploying your own SIP URI at little or no cost and pointing you to some excellent resources that facilitate calling millions of SIP phones around the world at zero cost. All you need is an Internet connection, and we’ll point you to a terrific softphone to begin your adventure.
Let’s begin by examining why SIP URI dialing is a problem with FreePBX. The reason is pretty simple. FreePBX interprets dial strings by matching them against some rules to determine whether you’re making an internal call or a call outside your PBX. It matches internal calls against a list of available internal extensions. External calls are matched against rules defined in your outbound routes which are associated with trunks. Since SIP URI calls don’t match any extension or outbound route, the caller receives a congestion tone.
The traditional workaround has been to define a custom extension using the FreePBX GUI which points to a SIP URI. Then the user can dial the custom extension, and the call will be routed to the defined SIP URI. These custom extensions also can be defined in extensions_custom.conf within the from-internal-custom context. For example, the following dialplan code would let users dial 411 to reach AT&T’s Toll-Free Directory Assistance: exten => 411,1,18005551212@switch.starcompartners.com.
But there’s a better way. Wouldn’t it be nice to be able to dial any SIP URI from a softphone or to store SIP URI addresses in the phonebook of your SIP phone?1 Well, now you can. Before we actually put the dialplan code in place, let us explain how this will work. First, FreePBX still needs to be able to distinguish a SIP URI call from a "regular call." The reason this gets tricky is because Asterisk typically throws away the destination hostname when you place a call. For example, calls to 8005551212 and 8005551212@sip2sip.info are processed by Asterisk in exactly the same way, i.e. dropping the host address before dialing.
Using the new dialplan code in the next section, here’s how calls will be processed:
User dials Asterisk processes call as ------------------------ --------------------------------------------- 701 internal call to local extension 701 4045551212 external call using NXXNXXXXXX outbound route 2233435945@sip2sip.info SIP URI call to Lenny by acct at sip2sip.info lennybgood@sip2sip.info SIP URI call to alias lennybgood@sip2sip.info
Cautionary Notes: Our code should work fine with any Asterisk 13 and FreePBX 13 or Incredible PBX deployment on any Linux platform; however, with servers other than Incredible PBX, make sure you have added the following entries to sip_general_custom.conf, or you can configure them in the GUI by making the changes in Settings -> Asterisk SIP Settings -> Chan SIP Settings:
srvlookup=yes allowguest=yes
You also need to test a traditional outbound call (e.g. 8005551212) immediately after you finish the install procedure. Monitor the Asterisk CLI (asterisk -rvvvvvvvvvv) and observe the first few lines of the log after you place a call. The second line will show SIPDOMAIN which should be either the FQDN of your server or an IP address depending upon how you registered your softphone extension. The first line should display the MyDomain variable. If it is empty or doesn’t match the SIPDOMAIN entry, the outbound call will fail. To fix it, add an entry to the Asterisk database from the Asterisk CLI using syntax like the following: database put MyDomain FQDN 10.0.0.11 or database put MyDomain FQDN sip.me.com where 10.0.0.11 or sip.me.com matches the SIPDOMAIN entry shown on the second line. Then retry your outbound call, and it should complete successfully. We’ve tested this back to the early Asterisk 11 days with FreePBX 2.11 without any problems. If your calls still fail, then you will probably need to remove the new code from your platform until you upgrade to a more current version of Asterisk and FreePBX. The code hasn’t been tested with FreePBX 14 and 15.
Finally, you may want to manually set the CallerID for your outgoing SIP URI calls. From the Asterisk CLI, issue a command for every extension from which you will be placing SIP URI calls, e.g. extension 701 syntax: database put 701 user_sipname "Nerd Uno"
Enabling SIP URI Dialing with FreePBX
To enable SIP URI dialing from phones registered with your Asterisk PBX, we’ll modify the dialplan in order to detect SIP URI dial strings entered into a softphone or retrieved from a phonebook associated with almost any SIP phone. When a SIP URI dial string is detected, we’ll send the call out as requested rather than passing the call through the outbound routes and trunks associated with your PBX. All of this dialplan code is open source and is licensed pursuant to the GPL2 license.
SECURITY ALERT: Never use the SIP URI MOD on a server with a publicly-exposed SIP port as it is possible for some nefarious individual to spoof your FQDN in the headers of a SIP packet and easily gain outbound calling access using your server’s trunk credentials.
FEB. 21 UPDATE: There was a bug in the original code which caused some internal calls to fail including calls to a DISA extension. Simply install the application again, and it will overwrite the previous version.
MAR. 5 UPDATE: A bug was discovered in previous releases that treated 911 and 933 calls as internal calls when, in fact, they should have been routed out using your outbound trunks. Simply install the application again, and it will overwrite the previous version.
MAR. 13 ALERT: This software is not compatible with the Debian, Raspbian, and Ubuntu platforms.
To begin or update your installation, log in to your PBX as root using SSH or Putty and issue these commands:
cd /tmp wget http://incrediblepbx.com/sipuri-mod.tar.gz tar zxvf sipuri-mod.tar.gz rm -f sipuri-mod.tar.gz ./install-sip-uri-mod.sh
Obtaining Your Own SIP URI
There are a number of ways to obtain your own SIP URI. Perhaps the easiest is to set up the open Incredible PBX cloud platform that we introduced several weeks ago. Then you can create as many SIP URIs as you like, and they can be used to perform any task that’s available with Asterisk. If you’re not quite ready to make that leap, a free or almost free SIP URI is available from the following sources. VoIP.ms provides a SIP URI for every subaccount you create. Just set up an internal extension number for the subaccount, and that becomes a SIP URI to connect back to your registered server or SIP phone. In the alternative, VoIP.ms will also provide you with a free iNUM DID which can be reached at the following IP address: 81.201.82.50. CallCentric provides a SIP URI matching your account number which can be reached @in.callcentric.com. CallCentric will also provide you with a free iNUM DID which can be reached at the following IP address: 81.201.82.50. LocalPhone provides the same two options as CallCentric: you can be reached by your account number @localphone.com. Or the LocalPhone-assigned iNUM DID can be reached @81.201.82.50. Then there’s pbxes.org. Your account name can be used for SIP URI access @pbxes.org. And, of course, if you’re a 3CX user, you can set up a SIP URI for each extension on your PBX. Just navigate to the Options tab of the desired extension(s) and enter a unique SIP ID for each extension. The SIP URI becomes SIPID@YOUR-3CX-FQDN. SIP URI calls to 3CX Clients on smartphones are also free! This list is not exhaustive. There are now more than 2,000 VoIP networks that support SIP URI access. Using a SIP URI dialing prefix, call any of the referenced networks @sipbbroker.com.2
Choosing a SIP Phone or Softphone
You can find dozens of recommendations for hardware-based SIP phones both on Nerd Vittles and the PIAF Forum. For today we’ll get you started with one of our favorite (free) softphones, YateClient. It’s available for almost all desktop platforms. Download YateClient from here. Run YateClient once you’ve installed it and enter the credentials for an extension on your PBX. You’ll need the IP address of your server plus your extension number and its password. Fill in the Yate Client template using the IP address of your PBX as well as your extension credentials. Click OK to save your entries.
Once the Yate softphone shows that it is registered, try a test call to Lenny using one of the following SIP URIs: 2233435945@sip2sip.info or 883510001198938@81.201.82.50. Better yet, try out a few Incredible PBX samples from the public server we previously deployed:
Yahoo News Headlines - news@demo.nerdvittles.com Weather by Zip Code - weather@demo.nerdvittles.com Directory Assistance - information@demo.nerdvittles.com Lenny for Telemarketers - lenny@demo.nerdvittles.com
Originally published: Monday, February 11, 2019

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

- Special thanks to Olivier Adler and voip-info.org for their early work on SIP URI dialing with Asterisk. [↩]
- Some of our links refer users to sites or service providers when we find their prices are competitive for the recommended products. Nerd Vittles receives a small referral fee from these providers to help cover the costs of our blog. We never recommend particular products solely to generate commissions. [↩]
SIP Happens! And Kamailio Makes It Easy, Part I

If ever there was a Swiss Army Knife for SIP, Kamailio (a.k.a. OpenSER) is the hands-down winner. The flexibility of this open source SIP server is legendary. Whether it’s secure communications, insulation from brute force attacks, load balancing, failover, WebRTC, or the return of shared line appearances on your office phone system, Kamailio can handle it while processing thousands of call setups per second on minimal hardware platforms.
Our plan for today is to walk you through setting up a Debian-based Kamailio server on an inexpensive cloud platform that is suitable for making thousands of free SIP phone calls worldwide. Down the road, we’ll walk you through using Kamailio as a frontend for one or more Asterisk® servers to insulate your communications workhorses without sacrificing network security. If, like us, you managed an office which migrated from key telephones to a platform like Asterisk, then you will most certainly appreciate the ability to once again let your managers and secretaries share phone lines without the aggravation of call parking and pickup. Other than removing a free office coffee machine, I can’t think of any single event that ever prompted a staff and management revolt quite like the one we experienced with the removal of key telephones. Little wonder that it’s part of all Cisco and Avaya phone systems as well as cloud offerings from Vonage, 8X8, Jive, and probably others.
Before we begin our adventure, let me caution everyone that this is an experimental platform with a tutorial prepared by a Kamailio novice. While we’ve done our homework, digging out information on Kamailio is a challenge because many of the experts depend upon Kamailio consulting for their livelihood. It’s quite similar to the early Asterisk years. We also don’t vouch for the longevity of any of these VPS providers. Reread our article for details.
SIP URI (Free) Calling Opportunities
We mentioned free SIP phones in our introduction of Kamailio. But let that sink in for a moment. As we have stressed for many years, SIP calls to anyone with a public SIP URI (somebody@somewhere.com) are entirely free to anyone worldwide. And you can talk as long as you like. All that’s required is an Internet connection, a SIP phone or softphone, and a SIP URI. As part of the Kamailio implementation, we’ll show you how easy it is to create SIP URIs for all your friends and business acquaintances securely… in seconds. First, let’s take a moment to consider what SIP URI (free) calling opportunities are available. There literally are millions of SIP URI resources that await. But, unless you want to be one of the "don’t call us, we’ll call you" folks, you also will need one or more SIP URIs for yourself. YOU DON’T NEED A KAMAILIO SERVER TO OBTAIN A SIP URI. Here are just a few of the possibilities. Using SIP Broker, you can call anyone on more than 2,000 VoIP networks around the globe. Using a softphone and a free or almost free registration with VoIP.ms, CallCentric, or LocalPhone, you not only get a SIP URI, but you also can request an iNUM number which also doubles as a SIP URI by coupling it with @81.201.82.50. 3CX and pbxes.org also offer SIP URIs to complement their free offerings. All of these companies will let you connect a softphone or SIP endpoint directly to their service without the need for an Asterisk PBX in the middle.1 You can even refer your favorite spam callers to Lenny via SIP URI: 2233435945@sip2sip.info.
Deploying a Cloud-Based Debian Server
We hope you took advantage of one of the special VPS offerings we highlighted to start the New Year. Some are still available with annual pricing that’s less than the cost of most lunches these days. We recommend a cloud platform because (1) it’s cheap, (2) it’s easy to set up a Debian platform, and (3) it provides a static IP4 address for your server. When you sign up or if you wish to reconfigure an existing VPS that you may have gathering dust, just choose the Debian 8/64 operating system and assign an FQDN to your server. Once you get your credentials, log into the server as root with the password that was provided. Immediately change your root password and issue the following commands to bring Debian up to date. We also strongly recommend changing the SSH port to deter would-be attackers. A TCP port in the 1000-2000 range works wonders. Simply edit /etc/ssh/sshd_config and change the Port 22 entry before rebooting. HINT: Birth years make the SSH port easy to remember.
passwd apt-get update apt-key update apt-get dist-upgrade apt-get -y install gcc flex bison libmysqlclient-dev make libssl-dev nano apt-get -y install libcurl4-openssl-dev libxml2-dev libpcre3-dev ntp ntpdate reboot
Once the reboot is complete, log back into your server’s new SSH port using this syntax where 1234 is the port number you chose.
ssh -p 1234 root@server-ip-address
Now we’re ready to install the necessary packages to support Kamailio:
apt -y install mysql-server mysql_secure_installation apt -y install kamailio kamailio-mysql-modules apt -y install kamailio-dbg apt -y install kamailio-extra-modules apt -y install kamailio-outbound-modules apt -y install kamailio-presence-modules apt -y install kamailio-tls-modules apt -y install kamailio-utils-modules apt -y install kamailio-websocket-modules
Configuring Kamailio’s kamctlrc File
For today, we’ll be configuring Kamailio to allow user logins from SIP endpoints including SIP phones and softphones. Down the road, we’ll change things up to let Kamailio serve as the front-end to one or more Asterisk PBXs. But let’s learn to walk before we start running. We’ll be editing three configuration files and then adding a SIP account to support logging in from a SIP phone. Let’s begin with kamctlrc.
(1) Edit kamctlrc: nano -w /etc/kamailio/kamctlrc
(2) Start by uncommenting SIP_DOMAIN and insert the FQDN you associated with your VPS.
(3) Uncomment DBENGINE line and make certain it points to MYSQL.
(4) Uncomment the following line: DBRWUSER="kamailio".
(5) Uncomment the DBRWPW line and insert your own password between the quotes.
(6) Uncomment the following line: DBROUSER="kamailioro".
(7) Uncomment the DBROPW line and insert a different password between the quotes.
(8) Uncomment the DBACCESSHOST line and insert the IP address of your server.
(9) Drop down near the bottom of the file and uncomment the PID_FILE line.
(10) Save the file.
Configuring Kamailio’s kamailio.cfg Startup File
(1) Edit kamailio.cfg: nano -w /etc/kamailio/kamailio.cfg
(2) Make the top of the startup file look like the following:
#!KAMAILIO #!define WITH_MYSQL #!define WITH_AUTH #!define WITH_USRLOCDB #!define WITH_ANTIFLOOD #!define WITH_PRESENCE # change next line to comment to disable logging #!define WITH_ACCDB # # Kamailio (OpenSER) SIP Server v4.2 - default configuration script
(3) Find the line: #!define DBURL "mysql://kamailio:kamailiorw@localhost/kamailio"
(4) Change the kamailiorw entry to the password you entered in step #5 above.
(5) Tighten up security a bit by searching for the line containing friendly-scanner.
(6) Immediately above that line, cut-and-paste this addition from Fred Posner at AstriCon:
### Posner additions
if ($ua =~ "(friendly-scanner|sipvicious|sipcli)") {
xlog("L_INFO","script kiddies from IP:$si:$sp - $ua \n");
$sht(ipban=>$si) = 1;
sl_send_reply("200", "OK");
exit;
}
if($au =~ "(\=)|(\-\-)|(')|(\#)|(\%27)|(\%24)" and $au != $null) {
xlog("L_INFO","[R-REQINIT:$ci] sql injection from IP:$si:$sp - $au \n");
$sht(ipban=>$si) = 1;
exit;
}
###
(7) Save the file.
(8) Generate the MySQL database and tables to support Kamailio: kamdbctl create
(9) At every prompt, type Y to add the feature.
(10) Open MySQL as root using the actual MySQL password you assigned when adding the MySQL package:
mysql -u root -ppassw0rd kamailio
(11) At the MySQL prompt, cut-and-paste the following commands:
ALTER TABLE acc ADD COLUMN src_user VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE acc ADD COLUMN src_domain VARCHAR(128) NOT NULL DEFAULT ''; ALTER TABLE acc ADD COLUMN src_ip varchar(64) NOT NULL default ''; ALTER TABLE acc ADD COLUMN dst_ouser VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE acc ADD COLUMN dst_user VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE acc ADD COLUMN dst_domain VARCHAR(128) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN src_user VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN src_domain VARCHAR(128) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN src_ip varchar(64) NOT NULL default ''; ALTER TABLE missed_calls ADD COLUMN dst_ouser VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN dst_user VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN dst_domain VARCHAR(128) NOT NULL DEFAULT ''; quit
Configuring Kamailio Defaults in /etc/default/kamailio
(1) Edit Kamailio defaults: nano -w /etc/default/kamailio
(2) Make the startup defaults look like the following:
# # Kamailio startup options # # Set to yes to enable kamailio, once configured properly. RUN_KAMAILIO=yes # User to run as USER=kamailio # Group to run as GROUP=kamailio # Amount of shared and private memory to allocate # for the running Kamailio server (in Mb) SHM_MEMORY=128 PKG_MEMORY=4 # Config file CFGFILE=/etc/kamailio/kamailio.cfg
(3) Save the file.
Managing Kamailio Startups & Shutdowns
With all the pieces in place, here’s how to start, restart, stop, and check status of Kamailio:
systemctl start kamailio systemctl restart kamailio systemctl stop kamailio systemctl status kamailio
Adding Users/Accounts to Kamailio
Now we’re ready to add accounts to Kamailio. These can be numeric, alphanumeric, or purely alpha entries. They become the user’s respective SIP URIs when coupled with @FQDN where FQDN is the fully-qualified domain name assigned to your server:
kamctl add username userpw
As you probably have guessed, kamctl is the main management tool for Kamailio. Issuing the command by itself will list all of the possible options that are available.
Monitoring Kamailio Access
There are a number of ways to monitor access (both legitimate and otherwise) to your Kamailio server. Here are a few of our favorites:
systemctl status kamailio cat /var/log/syslog | grep kamailio mysql -u root -ppassw0rd kamailio -e "select * from acc" mysql -u root -ppassw0rd kamailio -e "select * from missed_calls"
Connecting a SIP Phone to Kamailio
You can connect virtually any kind of SIP telephone or endpoint to Kamailio. You can find dozens of recommendations for hardware-based SIP phones both on Nerd Vittles and the PIAF Forum. For today we’ll get you started with one of our favorite (free) softphones, YateClient. It’s available for almost all desktop platforms.
Download YateClient from here. Run YateClient once you’ve installed it and enter the credentials for the account you created above. You’ll need the IP address of your server plus your account’s password. Fill in the Yate Client template using the IP address or FQDN of your Server as well as your Username and whatever Password you assigned to the account when you created it. Click OK to save your entries.
Once the Yate softphone shows that it has registered with Kamailio, try a test call to Lenny by dialing sip:2233435945@sip2sip.info.
Next week, we’ll tackle security. If you run systemctl status kamailio for a few days, you’ll understand why. We’ll also get your Kamailio server interconnected with Asterisk so that inbound calls to your new SIP URI pass through to Asterisk transparently. Enjoy!
Originally published: Monday, January 14, 2019

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

- Some of our links refer users to sites or service providers when we find their prices are competitive for the recommended products. Nerd Vittles receives a small referral fee from these providers to help cover the costs of our blog. We never recommend particular products solely to generate commissions. [↩]
A Sobering Look at Asterisk and the 2019 VoIP Landscape

Every six months or so we like to gaze into our crystal ball for a quick look at the VoIP landscape. 2018 has been quite the transformative year with the acquisition of Digium® and Asterisk® by Sangoma®. Unfortunately, as we predicted, the Digium layoffs have already begun, and 2019 may only get worse. While we have no inside information, we wouldn’t be surprised to see Digium’s headquarters in Huntsville closed within six months in an effort to balance the books. Part of the problem may be attributable to the terms of the purchase itself. However, we sense there’s a more troubling development. And that is the reality that VoIP is becoming less and less appealing to home users and small businesses as more and more folks migrate purely to cell phones. Those with teenagers already know this transformation is underway. With services such as Google Fi starting at $20 for unlimited calling and texting, it’s difficult to justify VoIP services even at bargain basement prices. Making the cellular switch even more appealing are offers such as a $400 credit with the purchase of an LG G7 smartphone from Google or a free LG G7 with new Sprint service.
What you lose with a pure cellular platform are many of the features that have made PBXs popular in the VoIP space: call routing, text-to-speech and voice recognition applications, conferencing, SPAM call blocking, and much more. But 2018 also was the year that Google finally pulled the plug on free calling through your PBX. Instead, you now have to purchase and configure a $50 OBi200 to continue with Google Voice, and the integration is painful to put it charitably. The demise of Google Voice added one more nail to the free VoIP coffin. And, as many of you know, Vitelity, our long-time platinum sponsor, now has bowed out of the VoIP retail business due to a change in focus from Voyant, the company’s new owner. Finally, our bargain-basement cloud provider for experimentation, HiFormance, appears to have bitten the dust. Details here. Suggestions here. Reminder: "You get what you pay for."
It’s not all bad news for 2019. First, all of the Incredible PBX platforms are still alive and well. And they will remain open source GPL code. Second, we’ve found a terrific new VoIP provider, Skyetel, that will give you a $50 credit so you can kick the tires for a good long while. Effective 10/1/2023, $25/month minimum spend required. Third, if you’re looking for a robust Cloud platform, Digital Ocean still is offering a $100 signup credit for your first 60 days of service, and Incredible PBX runs swimmingly on their $5/month platform with CentOS. Spend another $1 a month, and you get automatic backups of your cloud-based server. It’s cheap insurance for something as important as your phone system.
If you’re like us, you may be getting a little nervous about the future of Asterisk. We’ve already provided a series of articles on FusionPBX for FreeSWITCH. Our original tutorial and the follow-on articles showing how to create voice prompts using IBM Watson and how to create and deploy TTS applications such as news and weather reports are worth a careful read. And, if you consider yourself a pioneer, then you owe it to yourself to try out the FreeSWITCH developers’ new cloud-based platform, SignalWire. Here’s the $55 Promo code that worked for us: ITEXPO2019. That should get you off to a great start. And check out the pricing: U.S. DIDs are $0.08 per month, U.S. Origination rate (incoming) is $0.00325 per minute, U.S. Termination rate (outgoing) is $0.0072 per minute, U.S. SMS Outbound is $0.0009 per message, and U.S. SMS Inbound messages are free. MMS also available. Once verified, you can spoof any CallerID name and number that you own! What’s not to like? Asterisk Trunk setup example available here.
CAUTIONARY NOTE: SignalWire should be considered EXPERIMENTAL SOFTWARE and is not yet suitable for production use.
That should be enough excitement to keep all of you entertained over the holidays. We’re planning a few days off to be with family and friends. Let us be the first to wish each of you a very Merry Christmas. We’re looking forward to an exciting 2019!
Originally published: Monday, December 17, 2018

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

Skyetel Smorgasborg: SMS Blasting, SMS Dictator, and more

Just in time for Santa, we’ve got a great treat for those of you that have taken advantage of the Nerd Vittles special offer from Skyetel which gets you a $50 credit on their powerful VoIP platform. Today we’re adding not one, but three, SMS messaging utilities to the Incredible PBX UC platform. Effective 10/1/2023, $25/month minimum spend required. In addition to a command line utility to send SMS messages, we’re also introducing SMS Message Blasting which lets you send an SMS message to as many recipients as you would like. It’s perfect for sports team and community group messaging. To round out the trifecta, we’ve updated our SMS Dictator utility by integrating Skyetel messaging with IBM’s powerful voice recognition software.1 Simply dial S-M-S (767) from any extension on your PBX and dictate an SMS message to send to a recipient of your choice. Gone are the days of wrestling with Google’s ever-changing voice recognition platform. Good riddance!
To get started, you’ll need to have an IBM Watson account with an APIkey for their Speech-to-Text (STT) engine. Next, you will need a Skyetel SMS-enabled DID. Before we install today’s SMS scripts, it should be noted that SMS messages must be sent from the PBX registered as the Skyetel Endpoint Group for the SMS-enabled DID specified in the Skyetel SMS scripts. So let’s begin with the configuration steps to put all the pieces in place.
Getting Started with IBM Watson STT Service
We’ve created a separate tutorial to walk you through obtaining and configuring your IBM Watson credentials. Start there.
Now let’s get IBM’s Speech to Text service activated. Log back in to the IBM Cloud. Click on the (upper left) Menu icon and select Dashboard. Click on the Speech to Text app. Choose a Region to deploy in, choose your Organization from the pull-down menu, and select STT as your Space. Choose the Standard Pricing Plan or LITE Plan. Then click Create. When Speech to Text Portal opens, click the Service Credentials tab. In the Actions column, click View Credentials and copy down your STT APIkey. Then logout of IBM Watson.
Getting Started with Skyetel Messaging
If you haven’t already signed up for a Skyetel account, read our tutorial and take advantage of the $50 coupon for free service. Sign up for a DID and activate the SMS feature for your number. Create an Endpoint Group with the public IP address of your PBX. Then edit your phone number and link it to the Endpoint Group of your server. If you want to forward incoming SMS messages to either an email address or to your smartphone’s messaging service, configure it under the SMS & MMS tab. Finally, click on the settings icon beside your account name in the upper right corner of the Skyetel portal and then click the API Keys tab. Click the Create button and copy down your SID and SECRET for Skyetel’s API service. This secret is not retrievable once you close the window so put the credentials in a safe place for subsequent use. Then logout of the Skyetel portal.
Installing the SMS Components on Your PBX
There are three separate applications which we will install on your PBX: (1) a stand-alone utility that lets you send SMS messages from the Linux CLI by entering a recipients 11-digit phone number and an SMS message surrounded by quotes, (2) an SMS message blasting utility that lets you send a previously prepared SMS message to a group of recipients whose 11-digit SMS numbers have been entered into a text file, and (3) the SMS Dictator application which lets you pick up any phone on your PBX and dial S-M-S (767) to dictate a message and send it to a recipient whose number you’ve key in from your phone. For those not residing in North America, the number of phone number digits can easily be changed in all of the scripts. After we install the three applications, we’ll edit each of the scripts to insert your IBM STT and Skyetel API credentials. Then you’re ready to start messaging.
First, let’s install the stand-alone and message blasting SMS utilities. Log into your server as root and issue the following commands:
cd /root mkdir sms-skyetel cd sms-skyetel wget http://incrediblepbx.com/smsblast-skyetel.tgz tar zxvf smsblast-skyetel.tgz rm -f smsblast-skyetel.tgz
Next, let’s install the SMS Dictator application while still logged into your server:
cd /var/lib/asterisk/agi-bin wget http://incrediblepbx.com/sms-767-skyetel.tgz tar zxvf sms-767-skyetel.tgz rm -f sms-767-skyetel.tgz ./install-sms767-dialplan.sh
Configuring the Skyetel SMS Components
While still positioned in the agi-bin directory, edit smsgen.sh. Insert apikey as your API_USERNAME and your actual STT APIkey as API_PASSWORD in the fields provided. Insert your Skyetel SID, SECRET, and 11-digit DID in the fields provided. Then save the file.
Next, change directories to /root/sms-skyetel and edit BOTH sms-skyetel and smsblast and insert your Skyetel credentials and DID in the fields provided at the top of both files.
Finally, when you’re ready to use the message blasting application (smsblast), first insert your SMS message in the smsmsg.txt file. Then insert the list of SMS numbers in smslist.txt.
Testing the Skyetel SMS Components
To try out the SMS Dictator application, dial S-M-S (767) from a phone connected to your PBX. When prompted, enter the 11-digit number of the SMS recipient. When prompted, dictate the message to be sent and press #.
To try out the stand-alone SMS application, navigate to /root/sms-skyetel and issue the following command using the 11-digit number of the SMS recipient followed by a space and an SMS message to be sent surrounded by quotes: ./sms-skyetel 18005551212 "Howdy."
To try out the message blasting SMS application, navigate to /root/sms-skyetel. Enter the message to be sent in smsmsg.txt and enter the list of SMS numbers in smslist.txt. Kick off the message blast by entering the command: ./smsblast.
Originally published: Monday, December 10, 2018
 Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.
Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.

Need help with Asterisk? Join our new MeWe Support Site.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

- Skyetel outbound SMS messages are billed at 1¢/message plus a monthly SMS surcharge of 10¢ per SMS-enabled DID. With IBM’s STT service, users have a choice of the LITE tier providing 100 minutes a month of free transcription or the STANDARD tier providing unlimited message transcription at a cost of 2¢/minute. [↩]


 JUST RELEASED: Visit the Incredible PBX Wiki
JUST RELEASED: Visit the Incredible PBX Wiki