Home » Posts tagged 'sip' (Page 9)
Tag Archives: sip
Independence Day for Elastix 4: Introducing Issabel 4

There was more than a little disappointment when PaloSanto Solutions closed up their Elastix® shop last year. The good news was that 3CX stepped in with a terrific free offer on their commercial PBX for Elastix users. And, of course, Sangoma® quickly learned Spanish to tout their closed source crippleware, the FreePBX® Distro. But today’s a new day, and there’s another great surprise as the discontinued Elastix 4 open source product is reincarnated as Issabel 4. Featuring a respin of CentOS 7 plus Asterisk® 11 and FreePBX GPL components (only), Issabel is the first new open source project in the Asterisk community in many, many years. And what a terrific GPL platform it is.
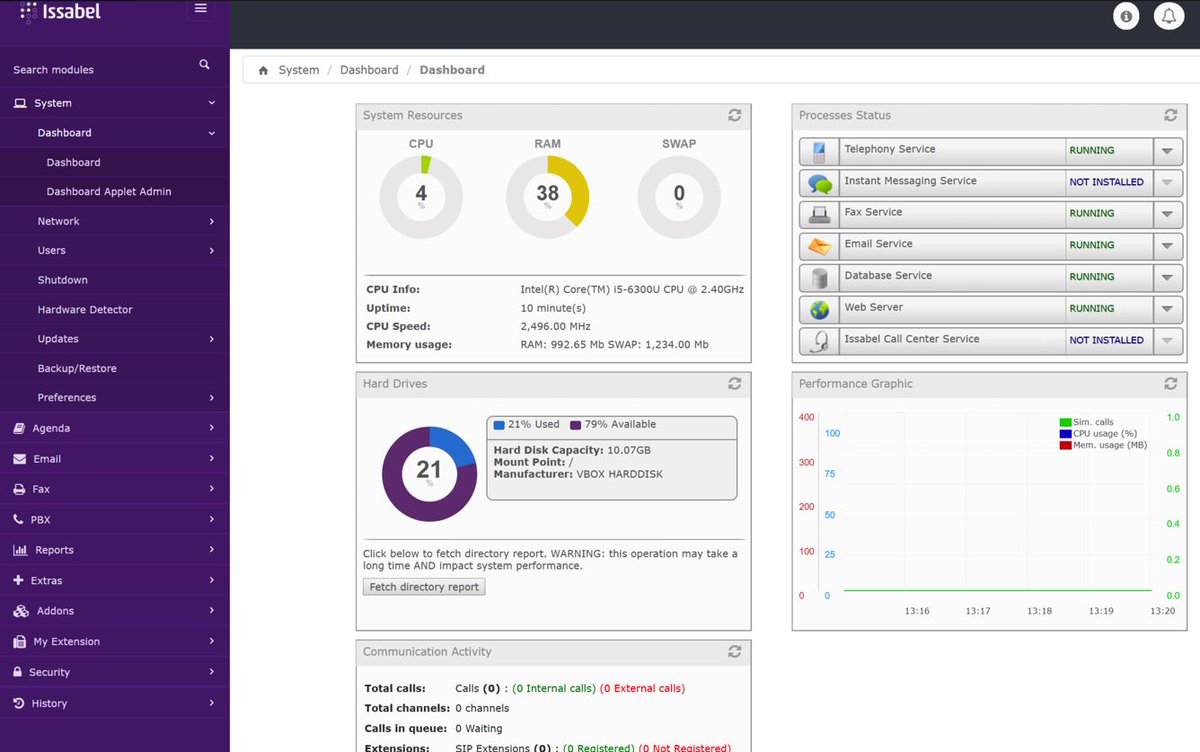
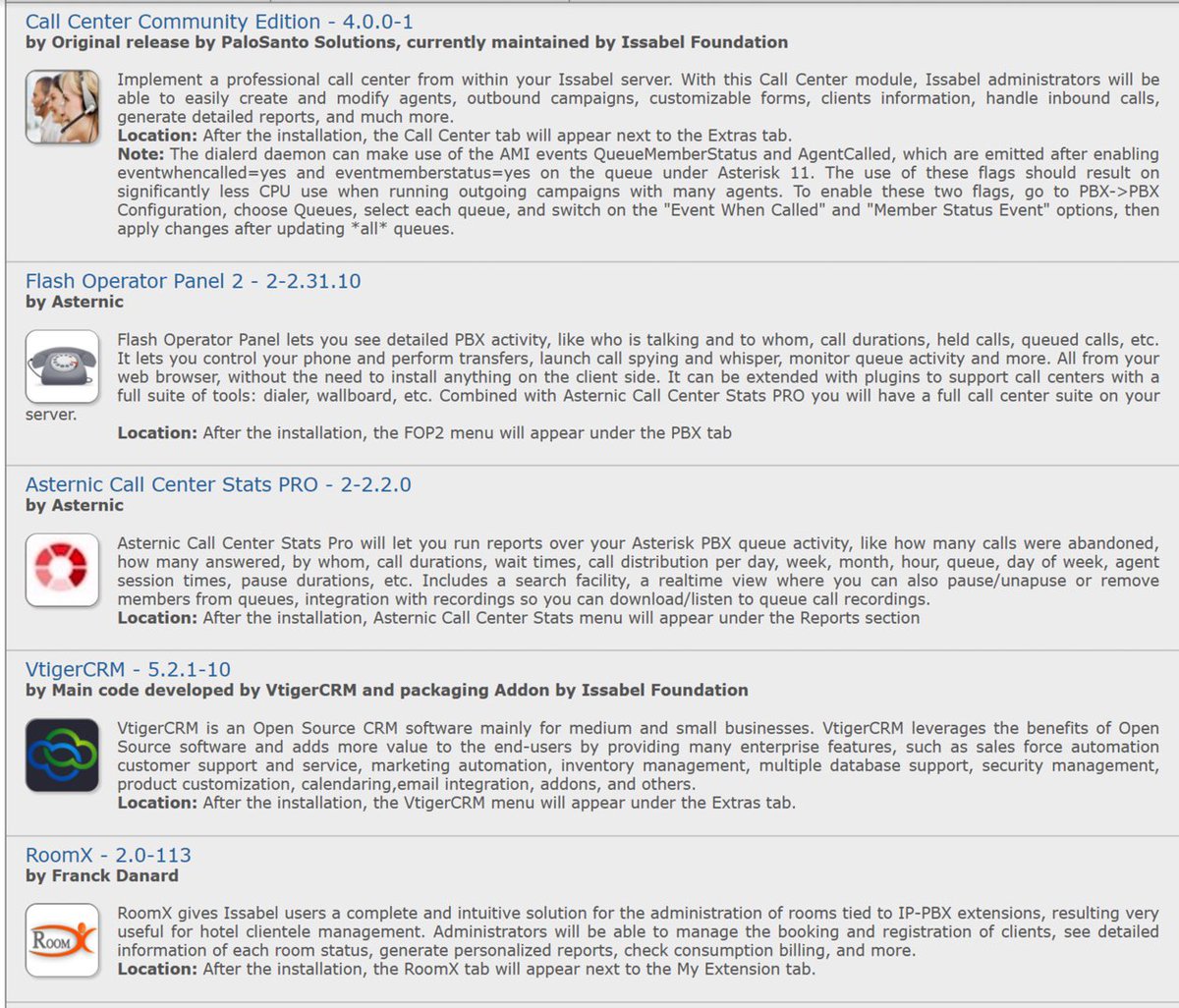
If you liked Elastix 4, you’re going to love Issabel. Its feature set not only matches Elastix 4, but it further enhances it with a collection of bells and whistles you won’t find anywhere else for free. In addition to a modern GUI and Dashboard, you’ll find a rich collection of add-ons to further enhance the FreePBX GPL components without any NagWare. There’s a native email server, a firewall, a fax server, chat service, Festival TTS, and optional add-ons for a Call Center, FOP 2, Vtiger CRM, and RoomX for hotel management.
2018 NEWS FLASH: Incredible PBX® 13 for the 2018 edition of Issabel supporting Asterisk 13 is now available for download. Complete tutorial available at this link.

For today, let’s get Issabel up and running. Installation is a breeze. Just download the 64-bit ISO from SourceForge. Be sure to use the January 2018 release. We will upgrade it from there when we install Incredible PBX 13 for Issabel in this new tutorial. Then burn the image to a CD or, better yet, load it up on your desktop PC with VirtualBox and take it for a quick spin. We think you’ll be thrilled.
Once you’ve installed the image and created your passwords, simply log into the Issabel GUI as admin with your GUI password. Click on PBX in the left column of the Dashboard. Set up a SIP trunk with an inbound and outbound route. Add an extension and a softphone, and you’ll be making your first call in minutes. If you’re unfamiliar with Elastix and FreePBX GPL components, here’s a quick tutorial to get you started.
Getting Started with Issabel 4
Here’s a quick overview of the installation and setup process for Issabel 4:
- Choose HW Platform – Dedicated PC, Cloud, Virtual Machine
- Install Issabel 4 – 64-bit CentOS 7 platform
- Activate Trunks for Issabel 4
- Connect a Softphone to Issabel 4
- Configuring SMTP Mail with Issabel 4
1. Choose a Platform for Issabel 4
Issabel 4 works equally well on dedicated hardware, a cloud-based server, or a virtual machine. Just be sure you have a sufficiently robust Internet connection to support 100Kb of download and upload bandwidth for each simultaneous call you wish to handle with your new PBX.
For Dedicated Hardware, we recommend at least an Atom-based PC of recent vintage with at least a 30GB drive and 4GB of RAM. That will take care of an office with 10-20 extensions and a half dozen or more simultaneous calls if you have the Internet bandwidth to support it. Our favorite hardware platform remains the $200 Intel NUC, and you can read all about it here.
For Cloud-Based Servers, we recommend RentPBX, one of our financial supporters who also happens to size servers properly and restrict usage solely to VoIP. This avoids performance bottlenecks that cause problems with VoIP calls. Yes, we have a coupon code for you to get the $15/month rate: NOGOTCHAS.1 The new image to support Issabel 4 should be available shortly. In the meantime, you can roll your own VPS using the Issabel ISO at Vultr for just $5 $2.50 a month using our referral code. First, upload the ISO by choosing Servers -> ISO -> Add ISO after login. ISO image link: http://nerd.bz/2ukpAXC
Next, create a new Instance by clicking the + icon in Servers. Choose a Server Location close to you. For Server Type, choose Upload ISO and pick your new ISO image. Use $2.50/month Server Size. Enter issabel for your Hostname. Leave everything else at default settings. Click Deploy Now. Click the Manage tab once your Cloud Instance is up and running. Make note of your server’s IP address. You’ll need it shortly.
Wait about a minute and then click View the Console to connect to VNC with your booted Issabel installer. Expand the console window so you can see the entire screen. Highlight Install and press ENTER. Choose the default Installation Destination, and then click Begin Installation. Click Root Password and set a very secure root password. Click Done to proceed with install. Have a cup of coffee while you wait. At about the 60% mark in the post-installation setup, the install may appear to be hung. Relax. It’s not. While you’re waiting, on the Vultr console, go to Settings -> Custom ISO under Server Details for your instance and locate the button to remove the ISO from the instance. Don’t do it yet. Switch back to the console window and wait for the instance to reboot and redisplay the Issabel installer menu. Now switch back to the Vultr window in your browser and click the Remove ISO button, and your server will reboot again. Close the Console window and then reopen it. Enter passw0rd (with a zero) for your MySQL password when prompted and create a very secure admin password for the web interface. Once the installer finishes, you can login to the IP address of your instance using user account admin and the web password you just created. If you ever need to reset them, login with SSH as root using your root password and issue the following command: issabel-admin-passwords --change
Update: On other cloud platforms that do not directly support ISO image installs, you can begin by installing a minimal, 64-bit version of CentOS 7. Then issue the following commands via SSH or Putty after logging into your server as root. NOTE: The 2018 release of Issabel featuring Asterisk 13 is NOT yet supported:
yum -y install wget nano openssh-server wget -O - http://repo.issabel.org/issabel4-netinstall.sh | bash
For Virtual Machine Installs, we recommend Oracle’s VirtualBox platform which runs atop almost any operating system including Windows, Macs, Linux, and Solaris. Here’s a link to our original VirtualBox tutorial to get you started. We suggest allocating 1GB of RAM and at least a 20GB disk image to your virtual machine for best performance. We actually used VirtualBox to build our first Issabel 4 platform.
2. Install 64-bit Issabel 4 on Your Platform
Begin by downloading the 64-bit Issabel 4 ISO. For dedicated hardware, burn the ISO image to a DVD and boot your server with the Issabel 4 ISO to begin the install. You’ll be presented with the CentOS 7 Installation GUI:
Choose: Time Zone (click)
Choose: Keyboard (click)
Choose: Install Drive (double-click)
Choose: Root Password (Make it Secure!)
Wait for Install and Reboot to Complete
Set MySQL Password to: passw0rd (MANDATORY: with a zero!)
Set Issabel admin Password: minimum 10 alphanumeric characters with upper & lowercase
For VirtualBox, create an Issabel 4 virtual machine of Linux (RedHat 64-bit) type by clicking New. Click Settings button. In System, enable I/O APIC and disable Hardware Clock in UTC Time. In Audio, enable Audio for your sound card. In Network, enable Bridged Adapter for Adapter 1. In Storage, click on Empty in the Storage Tree. Then click on the Disk icon to the right of CD/DVD Drive attributes. Choose the Issabel 4 ISO file that you downloaded. Click OK. Then start the virtual machine to begin the installation process. Follow the setup steps above to install Issabel 4 in your virtual machine.
3. Activate Trunks with Issabel 4
For those migrating from another aggregation including PIAF 3, this should be familiar territory for you. Using a browser, log into Issabel 4 at the IP address of your server using your admin password. Before you can actually make or receive calls outside your PBX, you’ll need at least one trunk. In the Issabel 4 GUI, click PBX -> PBX Configuration -> Trunks. Once you have your credentials from a provider, choose a provider from the list of preconfigured trunks on the right or create a new one. If you’re using one of the preconfigured options, remember to enable the trunk after adding your desired CallerID and credentials. Then save your settings and reload your Asterisk dialplan. That’s it. You’re ready to go.
To display your trunk registrations: asterisk -rx "sip show registry"
Google Voice Setup. If you wish to use Google Voice for free calling in the U.S. and Canada, you’ll need to sign up for an account with Simonics SIP to Google Voice Gateway service. Complete documentation is here. With the latest version of Incredible PBX 13 for Issabel, Google Voice support is included in the GUI.
Connection Issues. If you experience problems getting trunks to register with providers, add or remove the following entry in /etc/asterisk/sip_custom.conf: nat=yes. Then restart Asterisk: amportal restart.
4. Configure a Softphone for Issabel 4
You can connect virtually any kind of telephone to your Issabel 4 PBX after you first create a SIP extension. Plain Old Phones require an analog telephone adapter (ATA) which can be a separate board in your computer from a company such as Digium. Or it can be a standalone SIP device such as ObiHai’s OBi100 or OBi110 (if you have a phone line from Ma Bell to hook up as well). SIP phones can be connected directly so long as they have an IP address. These could be hardware devices or software devices such as the YateClient softphone. We’ll start with a free one today so you can begin making calls. You can find dozens of recommendations for hardware-based SIP phones both on Nerd Vittles and the PIAF Forum when you’re ready to get serious about VoIP.
We recommend YateClient which is free. Download it from here. Run YateClient once you’ve installed it and enter your credentials once you create a 701 extension in Issabel 4. You’ll need the IP address of your server plus your extension 701 password. Fill in the blanks using the IP address of your server, 701 for your account name, and whatever password is assigned to the extension. Here’s what your entries should look like. Click OK to save your entries.
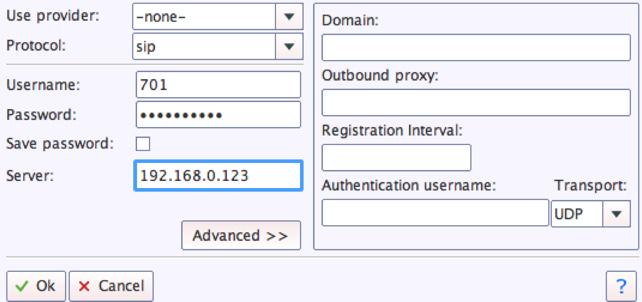
Once you are registered to extension 701, close the Account window. Then click on YATE’s Telephony Tab and place some test calls.
5. Configuring SMTP Mail with Issabel 4
Outbound email support using Postfix is preconfigured with Issabel 4. You can test whether it’s actually working by issuing the following command using your destination email address after logging in as root:
echo "test" | mail -s testmessage yourname@gmail.com
If you don’t receive the email message within a minute or two and you’ve checked your spam folder, chances are your ISP is blocking downstream SMTP servers in an effort to combat spam. Comcast is one of the usual suspects. To enable outbound email service for delivery of voicemail and other email messages with a provider blocking downstream SMTP servers, just follow our recent tutorial to reconfigure Postfix on your server.
Published: Monday, July 3, 2017
 Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.
Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
- Some of our links refer users to providers that support Nerd Vittles through referral fees or advertising. These funds help cover the costs of our blog. We never recommend particular products solely to generate revenue. However, when pricing is comparable or particular features warrant our recommendation, we support these vendors and deeply appreciate their financial support of our software development efforts. [↩]
3CX in the Cloud: 8 Great Ways to Secure Your Server

Now that many of you have taken advantage of the opportunity to deploy a free 3CX server, it seemed like an opportune time to share what we’ve learned while deploying 3CX on hosted platforms in the cloud. If you’ve followed our Nerd Vittles adventures over the years, you already know that our number one consideration with any PBX deployment is security. Without that, you’re just paying somebody else’s phone bill. While 3CX is extremely secure as delivered, once you choose a cloud-based platform, it’s a new ballgame. There is no 3CX firewall sitting between your PBX and the Internet.
We hear some of you saying, "I love Asterisk. Why would I want to move to 3CX?" The short answer is don’t move, add a new 3CX server to supplement your existing Asterisk® infrastructure. Why? Because the 3CX Clients for Windows, Macs, iOS, and Android are incredibly compelling. You can make a connection from anywhere using WiFi or cellular infrastructure and make crystal clear calls with zero hassles. Better yet, folks can reach you on your mobile phone from anywhere in the world at zero cost by dialing your SIP URI using any SIP device including SIP softphones and other 3CX Clients. And the 3CX Client is literally plug-and-play. Send the welcome email for the extension you wish to activate on the 3CX Client, and in one-click your 3CX Client is automatically configured and on line. By interconnecting your 3CX server with your existing Asterisk infrastructure, you get the best of both worlds without the messy NAT and firewall problems that were daily fare using Asterisk alone. But we’re getting ahead of ourselves, let’s get your 3CX server in the Cloud properly secured before moving on to the fun stuff.
Five years ago, we first introduced our Failsafe PBX Security Tips to Sleep Like a Baby. That’s well worth a careful read before we begin. For today, we’ll be implementing most of the Travelin’ Man 3 Security Model with a few tweaks to take advantage of existing 3CX security features. We’ll walk you through (1) choosing a cloud platform, (2) deploying the IPtables Linux firewall, (3) implementing a WhiteList to hide your server from those that don’t need access, (4) installing PortKnocker to make it easy for end-users to give themselves access to your PBX, (5) configuring FQDNs and implementing dynamic DNS updates for remote users, (6) setting up a BlackList to complement 3CX’s existing Anti-Hacking mechanisms, (7) deploying IPset to facilitate blocking entire countries from accessing your server, and (8) protecting SSH by setting up Fail2Ban and changing ports.
Let’s spend a moment considering the best security methodology for your cloud-based server. The short answer is IT DEPENDS. If all of your users are situated in the same location and never travel and you don’t care to enable SIP URI calling from anywhere in the world to save on phone costs, then the solution is pretty easy. We can lock your server down to the public IP address of your private LAN, and nobody else will ever see your server. Once you add users outside your home office, things get more complicated. If they are all sitting behind local routers with public IP addresses that are static, things are still fairly straightforward. We can whitelist all of the static IP addresses, and again nobody else will see your 3CX server. If you have users that travel for a living or need 3CX Client connectivity from their smartphones or from PCs at various locations that only have dynamic IP addresses, then things get more complicated. You can take your chances and expose SIP communications ports while locking down other access, or you can lock down everything, assign FQDNs to each user, and use dynamic DNS clients running on Android or iOS devices or local PCs to regularly update IP addresses of users in the firewall whitelist.
Another option that we use when traveling is PortKnocker which will be installed as part of our Travelin’ Man 3 security suite. The way this works is you send a single packet to three different TCP ports on your server using a predefined sequence of 3 port numbers. When there is a match, the server will automatically whitelist your IP address. Then you can log into SSH or the Web portal or use a 3CX Client in the usual way. There are PortKnocker clients for smartphones (Android’s DroidKnocker and iOS PortKnock), or you can use the command line from a Linux server to immediately authorize remote access from any IP address. No firewall modification is required. By default, Travelin’ Man 3 temporarily authorizes IP address access until the next server reboot. But you can elect to permanently whitelist the IP addresses if desired. Again, all of this can be performed remotely by end-users without ever touching your server or calling upon assistance from an administrator.
Finally, we’ve provided utilities in /root to assist an administrator in whitelisting IP addresses (add-ip) or FQDNs (add-fqdn) as well as removing whitelisted entries (del-acct). In addition, if you prefer to leave your server exposed, we’ve included tools to blacklist IP addresses (add-blacklist), and our discussion below will provide some alternatives to secure SSH access. Whichever path you choose, just be aware that server security it totally your responsibility, not ours and not 3CX’s. We strongly recommend that you regularly monitor the Event Log in the 3CX Dashboard for security issues and attempted breaches. You then can make firewall adjustments to address the problems or to further lock down your server.
LEGAL DISCLAIMER: ALL OF THE SECURITY CODE WHICH FOLLOWS IS DISTRIBUTED AS IS AND PURSUANT TO THE GPL2 LICENSE. YOU AGREE TO ASSUME ALL RISKS BY USING THIS SOFTWARE. YOU ARE FREE TO MODIFY IT TO MEET YOUR REQUIREMENTS SO LONG AS YOU COMPLY WITH THE GPL LICENSE TERMS AVAILABLE HERE.
For today’s tutorial, we will cover both the WhiteList 3CX firewall methodology and the less secure BlackList alternative. We’ll walk you through exposing the necessary ports if you elect to use this relaxed security configuration for your server. Just be aware that it’s your phone bill at stake particularly if you have authorized calls to countries outside the location of your server as part of your 3CX setup.
1. Choosing a 3CX Cloud Platform
Here are a few things to consider when choosing a cloud platform for your 3CX server. Keep in mind that the cloud giants like Amazon charge for data bandwidth usage AND data storage AND processing cycles. Even though Amazon uses what are traditionally considered non-routable IP addresses internally, be advised that Amazon internally routes these private LAN addresses. What that means is that, if you have whitelisted private LAN addresses in the 172.16.0.0/12 range, you will expose your server to hacking attempts from anyone with an Amazon S3 account. For that reason coupled with the pricing structure, we recommend against using Amazon as your 3CX cloud platform.
We also recommend you stick with VPS hosting plans using the KVM architecture and avoid OpenVZ unless it’s hosted with Virtuozzo 7. The traditional shared kernel architecture of OpenVZ means you will forfeit the ability to use powerful tools such as IPset to blacklist country-wide IP addresses from countries such as China and Russia. Over 90% of the attacks we see on our web sites originate from IP addresses in just those two countries. Fortunately, the new Virtuozzo 7 implementations of OpenVZ support ipset. SSDnodes in Montreal is the provider we use.
The rest of the cloud platform equation comes down to balancing the feature set and performance against the cost. At the bottom of the barrel is CloudAtCost which offers lifetime cloud services for a one-time charge PLUS an annual maintenance charge. Performance and reliability range from awful to tolerable. As an experimental platform, it’s worth considering. For anything beyond that, don’t waste your time or money.
Our preferences in low-cost, moderate performance cloud platforms include OVH virtual private servers ($3.49/mo. for 2GB RAM, 10GB SSD, 100Mbps unlimited bandwidth, and DDoS protection), Vultr VPS ($5/mo. for 1GB RAM, 25GB SSD, 1TB bandwidth), and Digital Ocean ($5/mo. for 512MB RAM, 20GB SSD, 1TB bandwidth plus $10 usage credit). For high performance, long-term use, nobody beats our corporate sponsor, RentPBX.com, at $15/mo. with referral code: NOGOTCHAS.1
2. Deploying the IPtables Linux Firewall
We’ve taken the pain out of deploying IPtables as a 3CX firewall. Our Travelin’ Man 3 script for 3CX does the heavy lifting for you by installing and preconfiguring IPtables and a collection of other security components. There are two alternatives when running the installer. You can completely lock down your server and use a firewall whitelist to enable access from specified IP addresses or FQDNs. There are utilities to allow administrators and end-users to add their own addresses to the whitelist. The other option is to run 3CX without the whitelist functionality and employ blacklisting to reduce the exposure of your server. This obviously increases the security risks but reduces the administrative burden on administrators and end-users. And, as you probably know, 3CX includes some security mechanisms to block or reduce attacks on your server. A third option using 3CX Clients or SBCs in networks that prevent VoIP calls is to deploy 3CX’s VPN-like Tunnel. This is well documented in this server tutorial and this client tutorial. It’s worth a careful look if you’re in a country that blocks VoIP calls, and it works with either TM3 firewall configuration. A fourth option which we will save for another day is to employ virtual private networks such as OpenVPN and NeoRouter. With VPNs, there’s more work on the front end but less day-to-day administration once properly configured.
If you don’t have widely scattered users and traveling users that need to employ 3CX Clients, the WhiteList option is far preferable. It sets up a WhiteList of devices that are authorized to access your PBX. Nobody else can even see the server on the Internet. To get started, log into your server as root using SSH or Putty. Be sure to login from a computer that will be used to manage your server so that this computer’s IP address gets whitelisted. You don’t want to lock yourself out of your own server! Then issue the following commands at the Linux prompt to run the TM3 installer, accept the license agreement, and choose either the WhiteList or BlackList option when prompted:
cd / wget http://incrediblepbx.com/tm3-3cx.tar.gz tar zxvf tm3-3cx.tar.gz rm -f tm3-3cx.tar.gz cd /root ./tm3-3cx.sh
When the installer finishes, press ENTER. You now have a functioning 3CX firewall with IPtables and Fail2Ban functionality to protect SSH logins from hacking attempts, IPset to block server access from certain countries, PortKnocker to facilitate remote user access to servers employing a WhiteList, and a collection of utilities in /root to facilitate WhiteListing and BlackListing of IP addresses and FQDNs by administrators.
3. Implementing the 3CX Firewall WhiteList
For the more technical types, here’s an overview of how the IPtables firewall is configured and functions. Currently, only IPv4 is protected. The basic setup is handled in /etc/iptables/rules.v4 by making a copy of rules.v4.tm3 and whitelisting 3 IP addresses: your server, your user PC from which you logged into SSH, and your public IP address. Additional whitelist entries are added using add-ip or add-fqdn in /root. Or end users can whitelist themselves using the PortKnocker credentials stored in /root/knock.FAQ. IPtables ALWAYS must be restarted/reloaded using the command: iptables-restart. This assures that all necessary components are reloaded including the base rules.v4 IPtables config plus the custom config in /usr/local/sbin/iptables-custom plus Fail2Ban. An administrator can remove whitelisted entries using /root/del-acct using the *.iptables filename associated with the entry to be removed. PortKnocker whitelist entries are stored by creation date.
Two templates for the TM3 custom configuration are stored in /usr/local/sbin. The WhiteList is iptables-custom.secure. The BlackList is iptables-custom.insecure. As part of the install, one or the other is copied into iptables-custom for use with your IPtables firewall. The code is well documented so that administrators can easily make modifications to support your own requirements. Simply rerun the tm3-3cx.sh installer once you have made changes, and your server will be reconfigured. Be advised that any previously added whitelist entries should be removed (/root/*.iptables) BEFORE rerunning the installer as these entries will not be replicated.
4. Using PortKnocker with the TM3 Firewall
There are two ways to use PortKnocker for end user management of the WhiteList. The default methodology is to temporarily WhiteList qualifying IP addresses whenever a successful port knock is performed from any remote site. This WhiteList addition to the firewall lasts only until the firewall is restarted with iptables-restart or the server is rebooted. For a mobile workforce, this is probably the preferable alternative with frequently updated remote IP addresses. The other alternative is to permanently add successful PortKnock IP addresses to the iptables-custom whitelist. The administrator can activate this by running the following command: iptables-knock activate. As with other WhiteList additions, these are stored in /root as *.iptables. To use PortKnocker, remote users will need the secret knock credentials stored in /root/knock.FAQ. Should you ever need to modify these codes when an employee is fired, simply edit /etc/knockd.conf and change the codes. Remember to revise /root/knock.FAQ with the new codes. Then restart PortKnocker: /root/knock-tester.sh.
5. Configuring Dynamic DNS for End Users
Here’s an easier way to set up remote users whose IP addresses regularly change either because of an ISP’s dynamic IP addressing scheme or because the user travels or frequently uses 3CX Clients from a smartphone. The trick here is to assign a fully-qualified domain name (FQDN) to each remote user’s device and then deploy a dynamic DNS update application on their device to keep the user’s current IP address in sync with their FQDN. As part of the TM3 implementation on 3CX, we included the /root/ipchecker script which checks for IP address changes every 10 minutes and updates the firewall whitelist accordingly. All that is required from the administrator is running /root/add-fqdn once for each remote user. Everything else is automatic on the 3CX server and the end user device.
There are a number of Dynamic DNS providers. Some are free and others have a modest annual fee. When it comes to DNS service, you get what you pay for. And our favorite remains dyndns.com. There are hundreds of domain names from which to choose, and there are update clients for most client platforms: Windows, Mac, Linux, iOS, and Android.
The setup procedure is straight-forward. (1) Choose a FQDN for each of your users on the dynamic DNS provider site. (2) Install and configure the DNS updater on each client device. (3) Run /root/add-fqdn on your 3CX server to add the FQDNs of each user to the TM3 WhiteList. (4) Restart IPtables: iptables-restart.
6. Implementing BlackLists with the TM3 Firewall
If an administrator elects NOT to deploy the 3CX firewall with a WhiteList and opts for the open 3CX firewall, then there are some additional steps to assure that your server remains secure. First, you’ll want to carefully monitor the 3CX Event Log in the 3CX web dashboard. When you spot hacking attempts that are being temporarily blocked by your 3CX server, immediately add them to your IPtables BlackList: /root/add-blacklist ipaddress. Thereafter, those users will no longer be able to access your server. After adding less than a handful of entries, our exposed server has not seen any further hacking attempts. YMMV!
7. Configuring Country Blocking with IPtables
The primary reason individual blacklist entries are unnecessary is because the TM3 installer automatically configures IPset to block access from a number of problematic countries. You can review these in /etc/block-china.sh and make modifications based upon your own requirements. Keep in mind that, if you add or remove countries from the script, you will need to add/remove the same entries in /usr/local/sbin/iptables-custom to assure that all of the countries you intend to block are assimilated into your firewall’s blacklist. Then reload the IPset tables and restart IPtables with this command: /etc/block-china.sh. To begin, you’ll need to decipher the country code for additional countries you wish to block. The country listing with codes is available here. The IPset country zones are available here.
The syntax for a new country addition in /etc/block-china.sh looks like this with the country name inserted in lines 1 & 4 and the country code inserted in lines 2 & 3:
/sbin/ipset -N china hash:net rm cn.zone /usr/bin/wget -P . http://www.ipdeny.com/ipblocks/data/countries/cn.zone for i in ; do /sbin/ipset -A china ; done
The blacklist entries in /usr/local/sbin/iptables-custom look like this using the country name from above:
/sbin/iptables -A INPUT -p tcp -m set --match-set china src -j DROP /sbin/iptables -A INPUT -p udp -m set --match-set china src -j DROP
None of the country modifications take effect until you reload the IPset tables and restart IPtables. Both are accomplished by running /etc/block-china.sh.
8. Hardening SSH with 3CX in the Cloud
If you chose to implement the TM3 WhiteList option, SSH on your 3CX server is insulated from SSH attacks because the bad guys can’t see or access port 22 on your server. However, if you’re using the non-WhiteList approach with IPtables, then some additional safeguards to secure SSH are appropriate. As part of the TM3 security suite, Fail2Ban was installed to block repeated attempts to login to SSH. While this offers some protection, be advised that Fail2Ban scans logs and, as such, requires a sufficient time slice of processing power to complete the task regularly. Some of the more vicious hacking attempts originate from extremely powerful server platforms that can monopolize processor resources thereby depriving Fail2Ban of the necessary horsepower to adequately protect your server from brute force SSH attacks. The most important thing you can do to protect SSH on your server is to regularly review /var/log/auth.log for hacking attempts and block those IP addresses using the add-blacklist script.
The most effective way to configure SSH access is to deploy key-based authentication using cryptographically secure keys. Once enabled and tested, be sure to remove the ability to login using your root password. But be aware that removing root password access will mean that you cannot login to your server from multiple devices without copying your private key to every device from which you wish to obtain access. An excellent tutorial that will walk you through the basic implementation procedure is available from Digital Ocean.
The other effective way to minimize SSH attacks is to change the default access port on your server from port 22 to some other TCP port above 1024. While there are arguments against this approach, if you have a dedicated IP address assigned to your server, the likelihood of a bad guy hijacking your IP address and setting up a script to fake SSH behavior and surreptitiously collect your passwords is extremely remote. Most of the bad guys use toolkits that target port 22 for brute force SSH attacks. By changing the port, you cut your vulnerability by about 99 per cent. Here’s how. First, edit /etc/ssh/sshd_config. Change the line near the top of the file from Port 22 to some port number above 1024. If the line is commented out with #, remove the #. Second, edit /etc/iptables/rules.v4. On or about line 27, change 22 to the port number you assigned in the first step. Third, edit /etc/fail2ban/jail.conf. Scroll down to the [ssh] section of the file and change the port entry to: port = ssh,1234 where 1234 is the port number you assigned in step one. Save the file. Fourth, restart SSH: /etc/init.d/ssh restart. Finally, restart IPtables: iptables-restart.
When using an SSH client to login to your server, the new syntax should look something like this: ssh -p 1234 root@ipaddress where 1234 is the port you assigned for SSH access to your server and ipaddress is the IP address or FQDN of your server. When using putty, be sure to change the port to match the SSH port you assigned for SSH access to your server.
Nerd Vittles Exclusive: Grab your new (free) 3CX perpetual license with unlimited SIP trunks, 10 extensions, 4 simultaneous calls, and 10-user conferencing here.
Originally published: Friday, June 23, 2017

Need help with 3CX or VoIP? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
- Some of our links refer users to providers that support Nerd Vittles through referral fees or advertising. These funds help cover the costs of our blog. We never recommend particular products solely to generate revenue. However, when pricing is comparable or particular features warrant our recommendation, we support these vendors and deeply appreciate their financial support of our software development efforts. [↩]
The World Traveler and 3CX: A Match Made in Heaven

Last week we introduced the new (free) version of PIAF5 powered by 3CX v15.5 supporting four simultaneous calls, unlimited trunks, 10 extensions, and 10-user conference calls. And today we’re torture-testing our new 3CX server in the Bahamas aboard one of Carnival’s 3,000-passenger floating cities. Somebody’s gotta do it, right? What makes this such a challenging test for any PBX are several things. First, we’re using a free Google Voice trunk on a free 3CX PBX that we configured in under 10 minutes at CloudAtCost for a one-time cloud server charge of $17.50. Second, we’re sharing a satellite Internet connection with 3,000 other people in the middle of the Caribbean. The weekly charge is about $100 so every Internet junkie subscribes. Third, we’re using a 3CX Client on an iPhone in Airplane Mode. And, finally, we’re sitting behind the most Draconian firewall you can imagine because Carnival assumes everyone is a bad guy trying to bring their Internet service to its knees.
For those coming from the Asterisk® world, I don’t have to remind you how challenging this NAT-based setup would be even assuming you had a flawless Internet connection. Believe me. We don’t. And the secret sauce that makes all of this seem like child’s play is the latest collection of 3CX Clients for PCs, Macs, Android devices, and iPhones/iPads. Simply download the client for your platform, log into your 3CX portal and send the welcome email from a configured extension to your phone, open the email on your phone and double-click on the attachment, and boom. Your 3CX Client is automatically configured in seconds and ready to make your first call. A monkey could do it. It’s that easy!

So our torture-test for today looks more like a final exam in VoIP telephony. We’ll be using Carnival’s WiFi connection from our iPhone with its iOS 3CX Client. We’ll dial into the Incredible PBX™ at our office in Charleston. The office number is configured with a Stealth AutoAttendant which we’ll use to make an outbound call to our Demo IVR in Marbella, Spain using DISA and a FreeVoipDeal trunk. For the techies, it’s the NAT Trifecta with DTMF hurdles that are virtually impossible to traverse using Asterisk and any SIP client.
Guess what? It not only works, but it sounds like you’re sitting in the adjoining office. No echo, no DTMF problems, no missing audio, and no detectable problems in voice quality with either the Charleston IVR or the Marbella IVR. If cost matters and traveling is a key component in your telephony requirements, you owe it to yourself to set up a free 3CX PBX and take it for a spin. Whether you use it to supplement an existing Asterisk setup or as a standalone PBX, we think you’ll be thrilled with the results.
Continue reading about the new, free PIAF5 server powered by 3CX v.15.5…
Originally published: Monday, June 12, 2017

Need help with 3CX or VoIP? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
Introducing IVRs in a Flash with Incredible PBX for Wazo
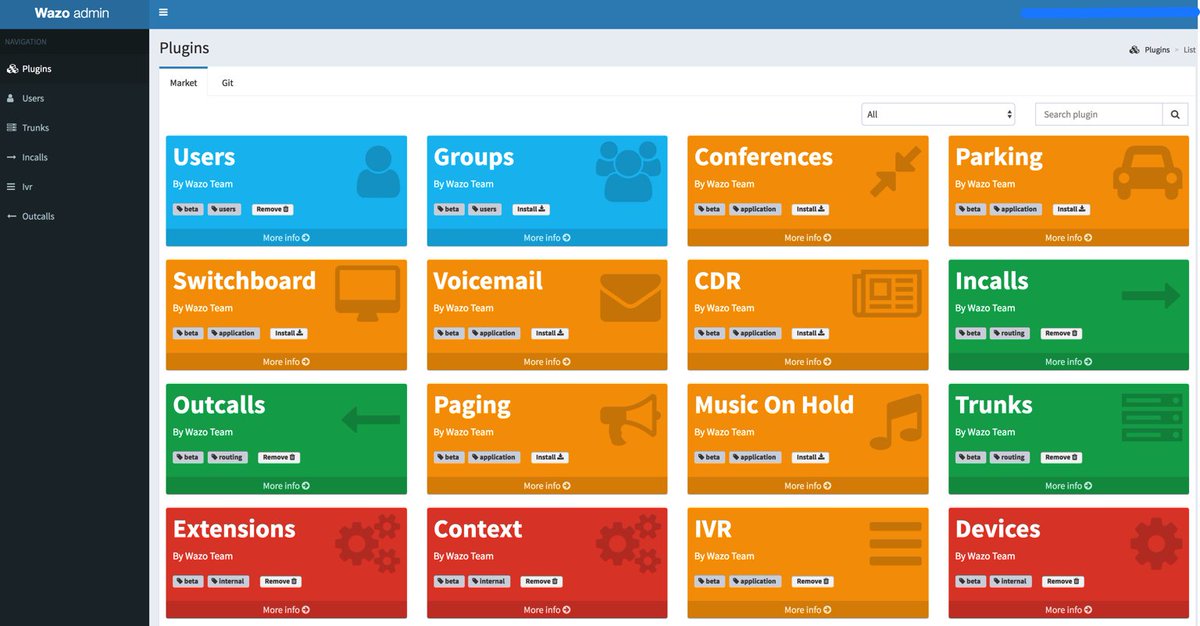
Last week we introduced the all-new, API-driven Admin User Interface for Wazo 17.07. But pretty pictures are only the icing on the cake. It’s what’s under the hood that really matters. And today we want to walk you through the new IVR User Interface with Incredible PBX for Wazo. The Wazo developers heard from many of you that were missing the GUI-driven IVR tools available in other products. And we’re pleased to tell you it’s another Home Run for Wazo. The UI is well-documented, easy to use, and incredibly simple to implement.
We should mention that our focus today is on the mechanics of using the new Wazo IVR Builder. We won’t be covering how to design a good IVR. If you want some great examples of poor IVR design, look no further than the main number of your favorite cellular or cable provider. Insofar as good design tips go, you can’t do better than learning from the master, Allison Smith. Here’s a link to her previous articles on Nerd Vittles.
We’re assuming you followed last week’s tutorial and added the basic components for the Admin user interface after using your browser to login to https://IPaddress/admin/. If not, start there and install the following plugins to begin: Users, Extensions, Contexts, and Devices. Next, add the plugins for Incalls, Outcalls, Trunks, and IVR. The whole setup procedure takes less than a minute. When you’re finished, your Navigation Sidebar should look like what’s shown above.
You’re obviously going to need a SIP or Google Voice trunk to handle incoming IVR calls so start there if you haven’t already set up at least one trunk that can be dedicated to your IVR. For the time being, add an Inbound Route for the Trunk that points to an extension.
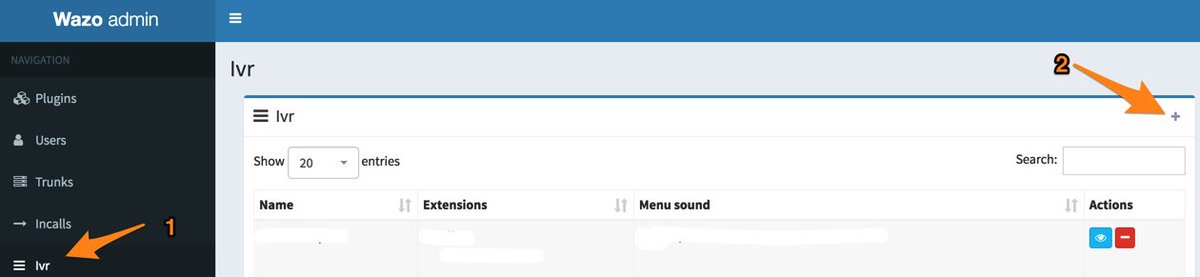
Now we’re ready to create your first IVR using the new IVR template in the Admin UI. Using your web browser, log back in to https://IPaddress/admin/ and (1) click IVR in the Navigation bar. Then (2) click + Add to create a new IVR.
Since the pieces already are in place for the hard-coded Demo IVR that comes with Incredible PBX for Wazo, let’s use those components to demonstrate how easy it is to build your own IVR with the new GUI. As you can see from the completed form below, there are two main sections in setting up an IVR. There are some basic settings that handle answering the call, playing the welcome message, and managing error conditions. Then there are IVR options that correspond to the Digit pressed by the caller using a touchtone phone. Each of these options has a destination. Currently, the available options include playing a sound file, ringing an extension, running custom dialplan code, or hanging up a call. There also is the ability to nest IVRs. Once you have built the secondary IVRs, the options list will also include an IVR option.
Since our sample IVR uses custom contexts for each of the Incredible PBX applications, we’ll rely heavily on the Custom option to route calls to extensions that were created when these applications were installed: Call by Name (411), Join Conference (2663), Lenny (53669), Yahoo News (951), and Weather Forecasts by ZIP Code (947). We’ll also show you how to direct a call to an extension using the default WebRTC extension (701). To get things going, simply copy the entries shown below and then Save/Update the template. The Wazo syntax to call a Custom destination looks like this: Dial(Local/951@default).
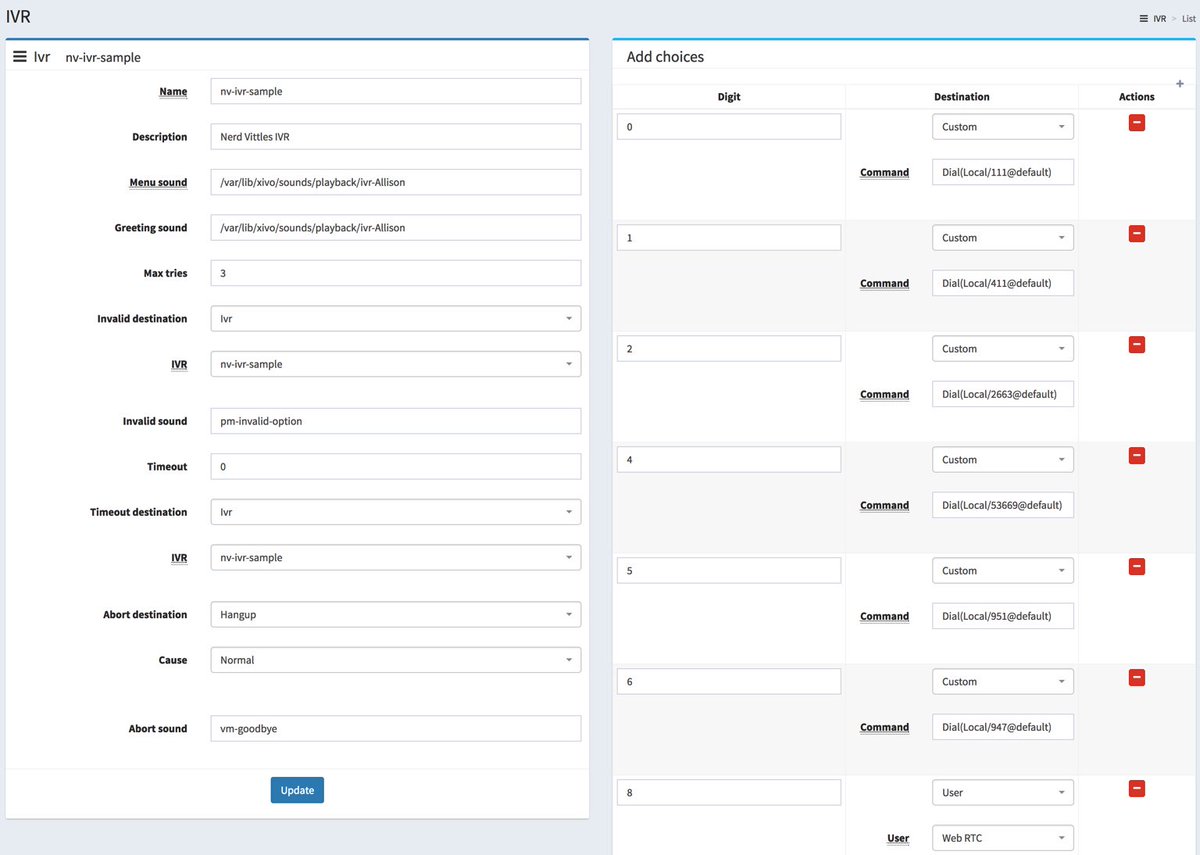
Before you attempt to build your own IVR, keep in mind that you’ll need at least a greeting message that tells callers which buttons to press. This file should be placed in /var/lib/xivo/sounds/playback. You can also use any of the default sound recordings found in /usr/share/asterisk/sounds/en for error messages and retry alerts.
Once you have your IVR built, the last step is to adjust an incoming route for one of your DIDs so that it points to your newly created IVR. We do this using the Incalls option in the Navigation bar. If you’re adjusting an existing inbound route, just call it up and make the changes as shown below:
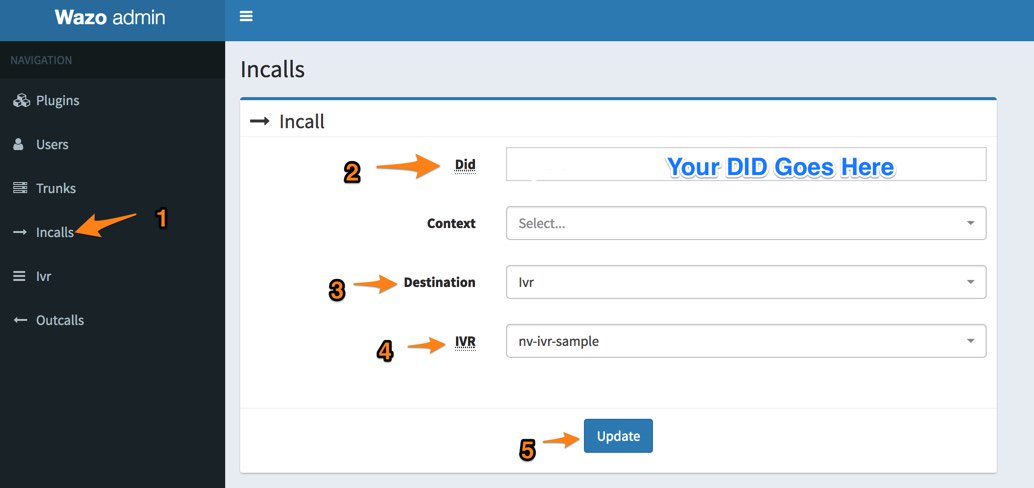
You’re good to go now. Call your DID from another phone and try out your first custom IVR.
Enjoy!
Published: Monday, May 22, 2017
 Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.
Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
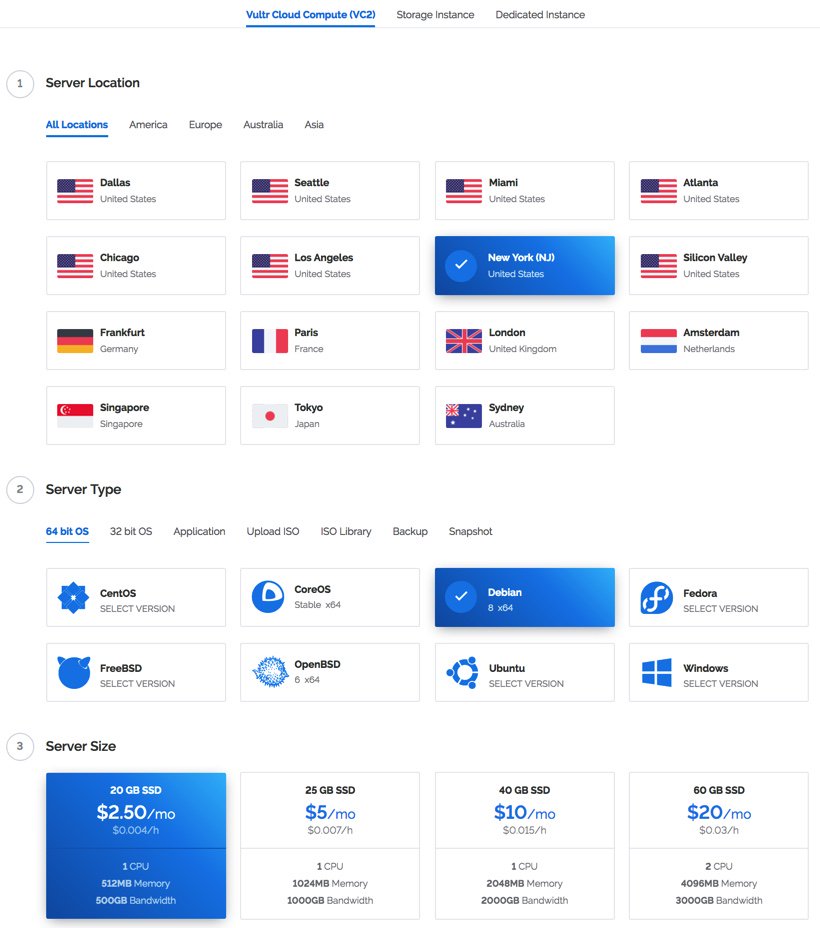
Cloud 9: VoIP on Steroids with Wazo and Vultr for $2.50/mo.

It tells you just how far we’ve come in Cloud Computing when $2.50 per month now buys you an Incredible PBX™ platform with great performance for a SOHO or home deployment. So what’s the catch? What else do you have to buy? If you’re in the United States, nothing! With a free Google Voice trunk, all of your incoming and outgoing calls to the United States and Canada are totally free. Does it matter where your phones are situated? Not at all. And how about scaling for large organizations? Not to worry! When you decide to move your entire organization to the Cloud, our friends at RentPBX stand ready to provide a 24×7 platform specifically engineered for VoIP at only $15 a month. Coupon code: NOGOTCHAS.
Getting Started with Vultr
We’ve used Vultr as our primary development platform for Nerd Vittles not only because of its price but also because of its reliability and feature set. With the recent reduction in the price of cloud instances, it’s now more than compelling as a stand-alone cloud solution for VoIP applications. An additional 50¢ a month buys you automatic daily, weekly, or monthly backups to a separate, fault tolerant storage system in the same data center. And, of course, Wazo itself generates nightly backups as well. What’s not to like? But don’t take our word for it. Walk through this tutorial with Vultr. You can even pay by the hour and kick the tires. Five hours of experimentation will set you back a whopping 2¢. Nope, that’s not a typo!
As you might imagine, the $2.50/month cloud instances at Vultr have been well received. In fact, that’s an understatement. Rather than oversubscribe users on their cloud platforms, Vultr limits the number of $2.50 cloud instances on each server. Lucky for all of us, Vultr maintains cloud hosting services in 15 cities around the world. As this is written, the $2.50 instances still were available in New York and Miami. Those locations obviously can change by the hour, but we have yet to see them disappear completely. A word to the wise: HURRY!
Getting Started with Incredible PBX for Wazo
After you have set up your account at Vultr using our referral link,1 the first step is to create your new cloud instance. Choose the desired site that has $2.50/month availability and select the 64-bit Debian 8 as your server platform. IMPORTANT: With Wazo, it’s extremely important that you leave the Server Hostname & Label blank. Otherwise, Wazo’s setup wizard will fail.
(1) Once you’ve built and started your new virtual machine, log into your server as root using SSH/Putty and immediately change your root password: passwd.
(2) With the $2.50 size VULTR virtual machine, you must create a swapfile before beginning the Incredible PBX for Wazo installation. Here are the commands:
dd if=/dev/zero of=/swapfile bs=1024 count=1024k chown root:root /swapfile chmod 0600 /swapfile mkswap /swapfile swapon /swapfile echo "/swapfile swap swap defaults 0 0">>/etc/fstab sysctl vm.swappiness=10 echo vm.swappiness=10>>/etc/sysctl.conf free -h cat /proc/sys/vm/swappiness
(3) Now you’re ready to kick off the Incredible PBX for Wazo install. The first phase is to bring Debian 8 up to current specs. Here are the commands:
cd /root apt-get -y install cloud-init wget http://incrediblepbx.com/IncrediblePBX14-Wazo.sh chmod +x IncrediblePBX14-Wazo.sh ./IncrediblePBX14-Wazo.sh
(4) Once the Debian 8 upgrade is complete, reboot your server and log back in as root. Then run the Incredible PBX for Wazo installer a second time:
./IncrediblePBX14-Wazo.sh
(5) Your server will pause after the Wazo install is complete. Verify that Wazo started successfully by pressing the ENTER key.
(6) Your server then will run the Wazo setup wizard. Verify that the wizard completed without errors by pressing the ENTER key.
(7) The Incredible PBX for Wazo installer then will complete the remainder of the setup without user intervention. It takes less than 10 minutes.
(8) Now proceed to the Incredible PBX Initial Configuration tutorial to continue your setup and begin your adventure. Enjoy!
Published: Monday, May 15, 2017
 Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.
Support Issues. With any application as sophisticated as this one, you’re bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It’s the best Asterisk tech support site in the business, and it’s all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won’t have to wait long for an answer to your question.

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
- Vultr provides a modest referral credit to Nerd Vittles for those that use our referral code. It in no way colors our recommendation of Vultr. As we noted, we use Vultr as our primary development platform, and we did so long before there were referral credits. You won’t be disappointed. [↩]
Meet the New Incredible Fax: A $10 Fax Machine for Asterisk

Every year, technology gets better and cheaper. And, believe it or not, that even includes faxing especially with Asterisk® and Incredible PBX™. Today we take another giant leap forward by introducing fax technology with the $10 Raspberry Pi Zero W. Adding a free Google Voice trunk provides not only free calling in the U.S. and Canada, but now you also get free faxing as well. And the latest release of Incredible PBX lets your RasPi determine whether incoming calls are humans or faxes, and it’ll route them accordingly. To send faxes, you can use the bundled AvantFax GUI client which lets you send PDF documents as faxes with a couple button clicks.

Overview. Once you’ve downloaded the Incredible PBX for RasPi image and made yourself a microSD card for your RasPi, the setup goes like this. First, we’ll configure a WiFi connection to support your server. Then we’ll install a Google Voice trunk. Next, we’ll use the included Incredible Fax installer to put the HylaFax and AvantFax components in place and to set up an email address for delivery of incoming faxes in PDF format. And finally we’ll use the GUI to configure your Google Voice trunk to manage incoming calls from both fax machines and individuals that actually want to talk to you. Faxes will be delivered to your email address, and traditional calls will be routed to a SIP phone or smartphone of your choice. In under 30 minutes, you’ll have a plug-and-play computer that’s about the size of a couple sticks of chewing gum.
Raspberry Pi Zero W Shopping List
Before you can install Incredible PBX, you’ll need a compatible Raspberry Pi Zero W platform. Unless you already have some of the components, the easiest way to begin is to purchase a bundle that includes all the components you’ll need. Here’s your best bet. It’s $35 and includes everything except a USB keyboard and an HDMI monitor and cable. Click on the image for ordering info:

Incredible PBX Installation Tutorial
Here’s everything you need to know about installation and setup. Just follow the links.
- Download and unzip Incredible PBX image from SourceForge (with GV OAuth support!)
- Transfer Incredible PBX image to microSD card
- Boot Raspberry Pi Zero W from new microSD card
- Login to RasPi console as pi:raspberry to initialize your server and configure WiFi
- Reboot after writing down your server IP address
- Login via SSH as root:password to secure your passwords & configure firewall
- Download latest Incredible Fax installer: http://nerd.bz/2nSeHKs
- Install Incredible Fax: /root/incrediblefax13_raspi3.sh (Credentials: admin:password)
Once everything is set up and working, you can remove the keyboard and monitor and put the Raspberry Pi Zero W on a shelf and run it with nothing more than a power adapter. Each time you reboot Incredible PBX, you’ll get an email with the IP address of your server. The recommended setup is to reserve the IP address assigned by your DHCP server in your router’s configuration. Then you have the equivalent of a static IP address while preserving the flexibility to move your RasPi to another network if the need ever presents itself.
Incredible PBX Initialization Steps
With a USB keyboard and HDMI monitor attached to your RasPi, power up the device. Login as pi with the password: raspberry. Incredible PBX first will whir through a few initialization steps. As part of the Raspbian OS, the Raspberry Pi Foundation includes a handy utility called raspi-config. This gets run automatically as part of the initial setup procedure in Step #4. At a minimum, you should configure the following options:
- Expand Filesystem (to use your entire microSD card)
- Wait for Network at Boot (choose Slow to Enable)
- International Options (configure all four options)
- Advanced Options – HostName (name your server)
- Finish (Save your settings but Delay reboot)
Incredible PBX WiFi Setup
The Raspberry Pi Zero W has WiFi-only networking. To get Internet connectivity, you’ll need to configure your server in Step #4 so that it can find your WiFi Access Point. Edit /etc/wpa_supplicant/wpa_supplicant.conf and insert the SSID and password (psk) for your WiFi network. Then save the file. Finally, stop and restart the wlan0 interface on your RasPi device, count to 15, and check the status of your server to decipher the new IP address for your WiFi connection. If no WiFi address, rinse and repeat.
ifdown wlan0 ifup wlan0 pbxstatus
Incredible PBX Phase 2 Configuration
Once you have your network IP address in hand, reboot your RasPi: reboot. Then use SSH or Putty to login to your RasPi from your desktop computer. The credentials are root:password. Complete the setup process by answering the prompts and be sure to set up a very secure root password and GUI admin password for your server.
Configuring a Gmail SmartHost for SendMail
Because of spammers, most Internet service providers now block mail from downstream mail servers. Your RasPi qualifies. There’s an easy way to determine if email service from your server is blocked. Just run the following command substituting your email address. Be sure to check your inbox and spam folder to determine whether you received the email.
echo "This is a test message." | mail -s testmessage yourname@youremaildomain.com
If you flunked the test, here’s what to do next. Modify SendMail to use an existing Gmail account as a SmartHost for email delivery. This means Gmail will actually send the messages rather than your server. Log into your RasPi as root and issue these commands:
cd /etc/mail hostname -f > genericsdomain touch genericstable makemap -r hash genericstable.db < genericstable mv sendmail.mc sendmail.mc.original wget http://incrediblepbx.com/sendmail.mc.gmail cp sendmail.mc.gmail sendmail.mc mkdir -p auth chmod 700 auth cd auth echo AuthInfo:smtp.gmail.com \\"U:smmsp\\" \\"I:user_id\\" \\"P:password\\" \\"M:PLAIN\\" > client-info echo AuthInfo:smtp.gmail.com:587 \\"U:smmsp\\" \\"I:user_id\\" \\"P:password\\" \\"M:PLAIN\\" >> client-info echo AuthInfo:smtp.gmail.com:465 \\"U:smmsp\\" \\"I:user_id\\" \\"P:password\\" \\"M:PLAIN\\" >> client-info nano -w client-info
When the nano editor opens the client-info file, change the 3 user_id entries to your Gmail account name without @gmail.com and change the 3 password entries to your actual Gmail password. Save the file: Ctrl-X, Y, then ENTER.
Now issue the following commands. In the last step, press ENTER to accept all of the default prompts:
chmod 600 client-info makemap -r hash client-info.db < client-info cd .. make sed -i 's|sendmail-cf|sendmail\/cf' /etc/mail/sendmail.mc sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.mc sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/Makefile sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.cf sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/databases sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.mc.gmail sed -i 's|sendmail-cf|sendmail\/cf|' /etc/mail/sendmail.cf.errors sendmailconfig
Finally, stop and restart SendMail and then send yourself a test message. Be sure to check your spam folder!
/etc/init.d/sendmail stop /etc/init.d/sendmail start apt-get install mailutils -y echo "test" | mail -s testmessage yourname@yourdomain.com
Check mail success with: tail /var/log/mail.log. If you have trouble getting a successful Gmail registration (especially if you have previously used this Google account from a different IP address), try this Google Voice Reset Procedure. It usually fixes connectivity problems. If it still doesn’t work, enable Less Secure Apps using this Google tool.
The last step is to add the following command to /etc/rc.local to send you an email with your IP address and SSID whenever the RasPi is rebooted. Insert the following commands just above the exit 0 line at the end of the file. Use an email address to which you have access on the road!
echo "IP address for your Raspberry Pi: $(hostname -I) plus wireless network, if any: `iwconfig`" | mail -s "Raspberry Pi IP Address" yourname@yourdomain.com
Installing a Google Voice Trunk for Free Calling
If you want to use Google Voice, you'll need a dedicated Google Voice account to support Incredible PBX. The more obscure the username (with some embedded numbers), the better off you will be. This will keep folks from bombarding you with unsolicited Gtalk chat messages, and who knows what nefarious scheme will be discovered using Google messaging six months from now. So keep this account a secret!
IMPORTANT: Do NOT under any circumstances take Google’s bait to switch from Google Chat to Hangouts, or you may forever lose the ability to use Google Chat with Incredible PBX. Also be sure to enable the Google Chat option as one of your phone destinations in Settings, Voice Setting, Phones. That's the destination we need for The Incredible PBX to work its magic! Otherwise, all inbound and outbound calls will fail. Good News! You're in luck. Google has apparently had a change of heart on discontinuing Google Chat support so it's enabled by default in all new Google Voice accounts. Once you've created a Gmail and Google Voice account, go to Google Voice Settings and click on the Calls tab. Make sure your settings match these:
- Call Screening - OFF
- Call Presentation - OFF
- Caller ID (In) - Display Caller's Number
- Caller ID (Out) - Don't Change Anything
- Do Not Disturb - OFF
- Call Options (Enable Recording) - OFF
- Global Spam Filtering - ON
Click Save Changes once you've adjusted your settings. Under the Voicemail tab, plug in your email address so you get notified of new voicemails. Down the road, receipt of a Google Voice voicemail will be a big hint that something has come unglued on your PBX.
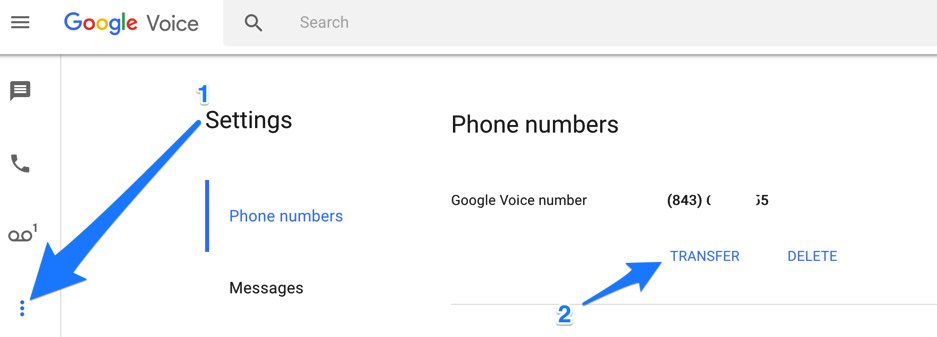
UPDATE: Google has improved things... again. You may not see the options documented above at all. Instead, you may be presented with the new Google Voice interface which does not include the Google Chat option. But fear not. At least for now there's still a way to get there. After you have set up your new phone number, click on (1) Settings -> Phone Numbers and then click (2) Transfer (as shown below). That returned the old UI. Make sure the Google Chat option is selected and disable forwarding calls to default phone number.
One final word of caution is in order regardless of your choice of providers: Do NOT use special characters in any provider passwords, or nothing will work!
Now you're ready to configure your Google Voice account in Incredible PBX. First, you'll need to obtain an OAuth 2 token for your Google Voice account. For a complete Google Voice OAuth tutorial, follow steps 8-10 in this Nerd Vittles tutorial. Once you have your credentials, you can do the rest of the Google Voice setup from within the Incredible PBX GUI. Choose Connectivity -> Google Voice. Once you've entered your credentials, you MUST restart Asterisk from the command line, or Google Voice calls will fail: amportal restart
If you have trouble getting Google Voice to work (especially if you have previously used your Google Voice account from a different IP address), try this Google Voice Reset Procedure. It usually fixes connectivity problems. If it still doesn’t work, enable Less Secure Apps using this Google tool.
Another option is to use an inexpensive SIP Gateway to Google Voice. The Simonics trunk in the Incredible PBX GUI is preconfigured for this purpose. All you'll need is your Google Voice credentials. Get started with this tutorial.
Installing Incredible Fax with HylaFax & AvantFax
Once you complete the initial configuration and get your mail server and Google Voice trunk squared away, it's time to run the Incredible Fax installer: ./incrediblefax13_raspi3.sh. You'll be prompted for an email address to which to deliver incoming faxes. After that, everything is pretty much automatic. A few prompts will appear during the installation process. Just press the ENTER key each time and ignore any errors you might see scrolling across your screen. They're harmless. When the HylaFax and AvantFax installs finish, reboot your server. Faxing won't work until you do!
Next, you need to change the default password for AvantFax which is a web-based interface to send faxes and read incoming faxes. From a browser, log into the IP address of your server. When the Incredible PBX menu appears, click the Users tab to display the Administrator menu. Then click on the AvantFax icon to load AvantFax. When prompted for credentials, enter admin:password for your username and password. You'll be prompted to change your password. Make it secure!
Finally, we need to configure your PBX to properly answer calls from fax machines as well as humans. Return to the Incredible PBX Admin menu and click the Incredible GUI icon. Then click the Server Administration icon. When prompted for your username and password, enter admin and the password you configured when you set up your server above. When the System Status screen displays, choose Connectivity -> Inbound Routes -> Default. Make the bottom section of the template look like this substituting your desired Destination for voice calls if you don't want them sent to the Incredible PBX IVR. Click Submit to save your changes and then reload your dialplan when prompted.
The best way to test things out is to send yourself a test fax. FaxZERO lets you send 5 free faxes of up to 3 pages every day. Give it a whirl. When you're ready to send a fax from Incredible PBX, log back into AvantFax, click on the Send Fax icon, and follow your nose.
Mastering the Incredible PBX Feature Set
Now would be a good time to explore the Incredible PBX applications. Continue reading there. If you have questions, join the PBX in a Flash Forums and take advantage of our awesome collection of gurus. There's an expert available on virtually any topic, and the price is right. As with Incredible PBX, it's absolutely free. Enjoy!
Originally published: Monday, March 27, 2017 Updated: Friday, May 12, 2017
 Support Issues. With any application as sophisticated as this one, you're bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It's the best Asterisk tech support site in the business, and it's all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won't have to wait long for an answer to your question.
Support Issues. With any application as sophisticated as this one, you're bound to have questions. Blog comments are a difficult place to address support issues although we welcome general comments about our articles and software. If you have particular support issues, we encourage you to get actively involved in the PBX in a Flash Forum. It's the best Asterisk tech support site in the business, and it's all free! Please have a look and post your support questions there. Unlike some forums, the PIAF Forum is extremely friendly and is supported by literally hundreds of Asterisk gurus and thousands of users just like you. You won't have to wait long for an answer to your question.

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest...
Free SMS Messaging Returns to Incredible PBX for Wazo

We continue our Wazo adventure today with a few simple additions to the Incredible PBX for Wazo dialplan. We will enable SMS messaging both from SIP phones such as the Yealink T46G and using voice recognition from any phone connected to Wazo including WebRTC. Of course, you still can use the command line to send SMS messages to one or more recipients using SMS Message Blasting which is covered below. To implement SMS messaging, you’ll need at least one Google Voice account configured. To implement the voice recognition option, you’ll also need to first enable voice recognition with Incredible PBX for Wazo.
The prerequisites for SMS Messaging with Incredible PBX for Wazo look like this:
- Incredible PBX for Wazo Server
- Preconfigured Google Voice Trunk
- Activate Google Speech Recognition on your server
Activating Google Speech Recognition on Your Server. If you haven’t previously activated Google Speech Recognition on your Wazo server, you’ll need to complete this step if you want to be able to dictate SMS messages from phones connected to Wazo. Follow this tutorial to obtain a speech recognition API key and activate the Google service on your server. It only takes a couple minutes.

SMS Dictator for Wazo. True to form, Google broke the command-line SMS messaging component a few weeks ago. So let’s get that squared away before we begin. Install the latest Google Voice python scripts and the updated SMS Dictator components by issuing the following commands after logging into your server as root. You’ll need your Google Voice credentials to install the update:
cd /root wget http://incrediblepbx.com/sms-dictator-wazo.tar.gz tar zxvf sms-dictator-wazo.tar.gz rm -f sms-dictator-wazo.tar.gz ./sms-dictator.sh
Wazo SMS Messaging Setup. You may also want to enable your SIP phones to send SMS messages directly. Login to your Wazo PBX using your favorite web browser. We need to review the existing gv.conf file by navigating to IPX Configuration → Configuration Files → gv.conf. Review the first context in the file. It should look like the following. Be sure that the third from the last line below does NOT wrap to a separate line in the Wazo editor! Insert your Google Voice credentials for GVACCT and GVPASS.
;# // BEGIN gv-outcall
[subr-gv-outcall]
exten = s,1,Set(XIVO_CALLOPTIONS=r)
same = n,GotoIf($["${MESSAGE(body)}" = ""]?skipsms)
same = n,Set(GVACCT=yourname@gmail.com)
same = n,Set(GVPASS=yourpassword)
same = n,System(/usr/bin/gvoice -e ${GVACCT} -p ${GVPASS} send_sms ${XIVO_DSTNUM} "${MESSAGE(body)}")
same = n(skipsms),Return()
;# // END gv-outcall
Once you get this set up and since we’ll be using plain text passwords to send the SMS messages through Google Voice, you’ll need to perform these two additional steps after first logging into your Google account with a browser using the same IP address as your Wazo server: (1) Enable Less Secure Apps and (2) Activate the Google Voice Reset Procedure. Now promptly send an SMS message from a phone registered to your Wazo server.
Dial S-M-S (767) from any phone connected to your Wazo PBX to send an SMS message. After dictating your message, you have the choice of keying in a 10-digit phone number for the SMS recipient or you can say the name of anyone in your AsteriDex phone book.
Sending SMS Messages. We obviously can’t cover the SMS messaging methodology for every SIP phone on the market. But here’s how to send an SMS message using Yealink’s T46G. First, configure one of the buttons on the phone as an extension on your Wazo PBX. Next, press the Menu button. Highlight Messages and press OK. Choose Text Message and OK. Choose New Message and OK. Type your SMS message using the keypad and press Send button. For the From: field, use the left and right arrow keys to select your Wazo extension. Press the down arrow and fill in the SMS number of your recipient just as you would do on your smartphone. Press the Send button. "Sending Message" will appear briefly on the T46G’s display. Wazo’s Asterisk CLI also will show transmission of the SMS message.
Interestingly, the same SMS functionality exists on the $29 UTP E-62 (if you can find one). Choose Menu → Applications → SMS → New. Type your SMS message using the keypad and press Send button. For the From: field, use the left and right arrow keys to select your Wazo extension. Press the down arrow and fill in the SMS number of your recipient just as you would do on your smartphone. Press the Send button. "Sending Message" will appear briefly on the UTP’s display. Wazo’s Asterisk CLI also will show the SMS transmission.
For bargain hunters that can’t find a UTP E-62, Yealink’s $50 YEA-SIP-T19P-E2 Entry-level SIP phone also appears to support SMS messaging. As with the UTP phones, you’ll need a $9 power supply unless your network supports POE.
Creating an SMS Message Blast with Wazo. Here’s how to take advantage of SMS Message Blasting using a Google Voice account with Incredible PBX for Wazo. Log into your server as root and do the following:
- Edit /root/smsmsg.txt and insert the text message to be sent
- Edit /root/smslist.txt and create a list of the phone numbers to receive the message
- Edit /root/smsblast and insert your gvoice username and password
- Run /root/smsblast to kick off the SMS Blast
Receiving SMS Messages. Typically reply messages to Google Voice numbers are forwarded either to an email address or to Hangouts. We don’t recommend enabling incoming mail on your Wazo PBX. Instead, add a New Alternate Email Address to your Google Voice account in Settings → Voicemail & Text. After verifying the new email address, set it as your Voicemail Notification email address and Save changes. Go back into Settings → Voicemail & Text and make certain that you have also checked the Text Forwarding checkbox which now should reflect your alternate email address. Now all of your incoming SMS messages will be delivered to this email address.
TIP: Google will no longer let you forward incoming SMS messages directly to another SMS destination, but you can cheat. If you have your own mail server or a non-Gmail account on which you can redirect incoming mail without verification, then simply set up the alternate email address as documented above. Then reroute that email address to point to an SMS-email gateway that forwards incoming messages to SMS, e.g. 8431234567@txt.att.net to send an SMS message to your AT&T cellphone. The complete list of providers is here. Enjoy!
Originally published: Monday, April 3, 2017

Need help with Asterisk? Come join the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
Best of Both Worlds: Marrying Asterisk to 3CX’s Free PBX with a $35 Raspberry Pi

One of the real beauties of Asterisk® has always been its flexibility in talking to other PBXs, both commercial and open source. There are numerous reasons why you might want to try this. First, it makes it easy to migrate to a commercial platform where you can get support for mission critical telephony requirements. Second, you may want a hybrid setup where servers with on-site support personnel can run Asterisk while remote satellite offices can take advantage of a commercial PBX and the support options it offers. Third, you may want to take advantage of specific features that are only available by relying upon multiple PBX solutions. In the case of 3CX, their integrated softphone clients with one-click setup simplicity, conferencing and WebRTC apps, and Call Center offerings are the best in the business while providing unmatched VoIP security. Asterisk on the other hand is light-years ahead of almost everybody in the text-to-speech and voice recognition fields while offering the most powerful VoIP toolkit to build any custom VoIP application imaginable.
Today we thought it would be fun to walk you through the easy way to tie an Incredible PBX server with all its features to a powerful (free) 3CX platform with its virtually flawless softphone clients.1 When we’re finished, you’ll have a free 3CX server in the Cloud at a one-time total cost of $17.50. And you’ll be able to place and receive free U.S./Canada calls from any iPhone, Android phone, or PC using the 3CX client from anywhere in the world with nothing more than a WiFi connection. The Google Voice trunk supporting the calls will reside on Incredible PBX for the Raspberry Pi. When you’re sold on the power of the 3CX platform, you can upgrade to the 3CX 4-simultaneous call commercial offering with unlimited users and trunks at an annual cost of just $149. Maintenance and upgrades are included. Large organizations have relied upon back office servers for custom applications forever. And now you can take advantage of the same flexibility using a tiny $35 Raspberry Pi and our free (as in really free) Incredible PBX software. No Gotchas!
Initial Raspberry Pi Platform Setup
Before we can interconnect 3CX’s Free PBX with a Raspberry Pi, you obviously have to set up both PBX platforms. For the Raspberry Pi, our recent Nerd Vittles tutorial will walk you through the setup process. In lieu of a Raspberry Pi, you can use any legacy FreePBX®-based Asterisk platform including Incredible PBX 13, PIAF3, Elastix®, AsteriskNOW®, or FreePBX Distro®. The setup procedure is exactly the same.
Building a 3CX Server in the Cloud
Building a 3CX server in the Cloud is equally easy. Let’s go through the process once again. If you’re just experimenting, a lifetime Cloud-based server at CloudAtCost for a one-time charge of $17.50 cannot be beat. We would hasten to add that we don’t recommend this platform for production use, but it’s a terrific proof-of-concept option. When you’re actually ready to deploy 3CX for production use, the least costly Cloud solution is the $3.49 per month OVH RAID offering with 2GB of RAM and 10GB storage. The $5 per month offerings from Digital Ocean and Vultr are other alternatives worth a look. Both of these platforms come with free credits ($10 and $20, respectively) to let you try things out.
To get started, sign up for a $17.50 server at Cloud at Cost. They will send you credentials to log into the Cloud at Cost Management Portal. Change your password IMMEDIATELY after logging in. Just go to SETTINGS and follow your nose.
To build your free 3CX PBX, create a virtual machine by clicking on the CLOUDPRO button in the CloudAtCost control panel. Then click Add New Server. Choose 1 CPU, 512MB RAM, and 10GB storage for your server. Choose Debian 8 64bit as the OS Type and click Complete.
While CloudAtCost is building your server platform, obtain a free license key for 3CX.
Once the Debian 8 server appears in your Control Panel, it will look something like what’s shown above, not CentOS obviously. The red arrow points to the i button you’ll need to click to decipher the password for your new virtual machine. You’ll need both the IP address and the password for your new virtual machine in order to log into the server which is now up and running with a barebones Debian 8 operating system. Note the yellow caution flag. That’s telling you that Cloud at Cost will automatically shut down your server in a week to save (them) computing resources. You can change the setting to keep your server running 24/7. Click Modify, Change Run Mode, and select Normal – Leave Powered On. Click Continue and OK to save your new settings.
Finally, you’ll want to change the Host Name for your server to something more descriptive than c7…cloudpro.92… Click the Modify button again and click Rename Server to make the change. Your management portal then will show the new server name as shown above.
Next, log in to your new Debian server as root using SSH or Putty and issue the commands below. Step #1 is to change your root password. What appears as the fourth line below is actually part of the third line and needs to be run as a single command. The last line to install SendMail will actually be run after you elect to use the Web Interface Wizard to configure 3CX. Just run it from the SSH command line before you switch to a browser to complete the 3CX setup.
passwd wget -O- http://downloads.3cx.com/downloads/3cxpbx/public.key | apt-key add - echo "deb http://downloads.3cx.com/downloads/3cxpbx/ /" | tee /etc/apt/sources.list.d/3cxpbx.list apt-get update rm -f /zang-debian.sh apt-get -y install 3cxpbx apt-get -y install sendmail sendmail-bin
When the initial setup finishes, choose the Web Interface Wizard and complete the install using your favorite web browser. Enter your 3CX license key when prompted. Make up a very secure Username and Password to access your 3CX portal. Specify that your IP address is Dynamic when prompted (even though it isn’t). This tells 3CX to generate an FQDN for your server. Accept the default ports for HTTP (5000) and HTTPS (5001) access to your server. We recommend choosing 4-digit extensions numbers which will make it easy to distinguish 3CX extension numbers from 3-digit extension numbers of the RasPi platform. While logged into the 3CX management portal, adjust Settings → Email to Mail Server → 127.0.0.1 and Reply to → noreply@YourActual3CX-FQDN. Leave the other settings blank and click TEST then OK. Now download your favorite 3CX smartphone client, send yourself the Welcome Email for your default extension, and your 3CX initial setup is complete.
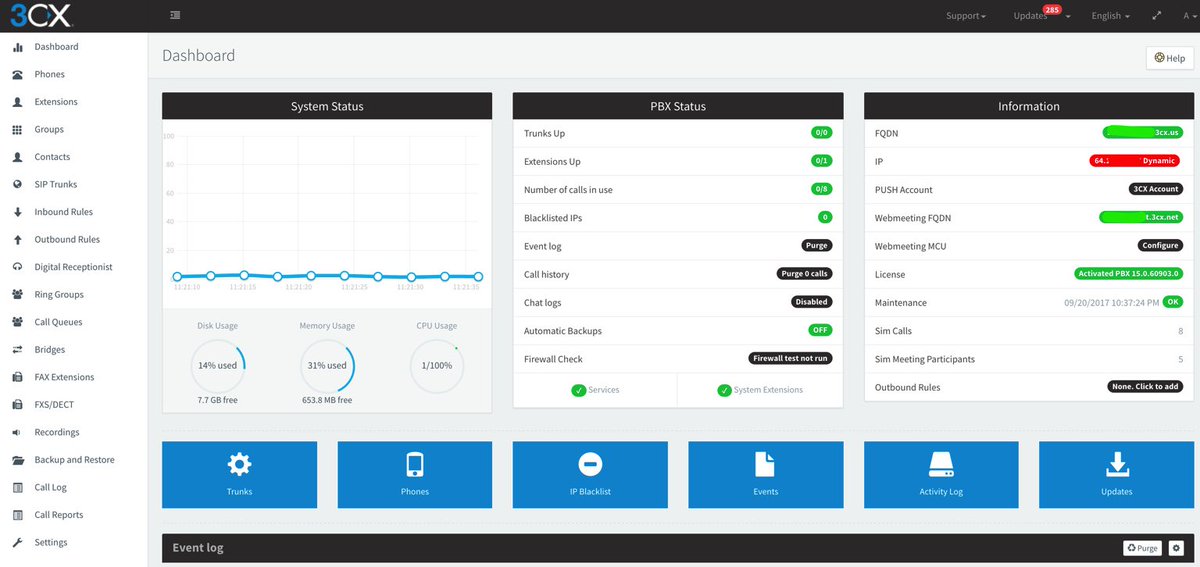
Server Interconnection Overview
Now we’re ready to interconnect the two servers. What we’ll be doing is creating Trunks on both the Raspberry Pi and the 3CX server and tying them together. We’ll use this trunk to handle the call traffic between the two PBXs. Then we’ll add incoming and outgoing call routes on both servers to specify how the individual calls should be routed. Because the free version of 3CX limits the administrator to a single trunk, we’ll offload all of the provider trunks to the Raspberry Pi and reserve the one available 3CX trunk as the interconnect path to the Raspberry Pi. For today’s setup, we’ll use 3CX’s free softphone clients as the actual phone devices for end-users. Of course, you could also use your favorite SIP phones, and 3CX provides automatic configuration for dozens of devices. But we want to introduce the 3CX smartphone clients because they provide an incredibly easy way to get users connected without having to worry about punching holes in firewalls.
To place outbound calls on the 3CX side, 3CX provides enormous flexibility in call routing. Because we chose 4-digit local extensions when we set up the 3CX server, it will make it easy to route other calls through the outbound trunk to the Raspberry Pi using nothing more than the length of the dial string. For example, 3-digit calls line up perfectly with extension numbers on the Incredible PBX for RasPi platform. So 3CX users can easily reach extensions connected directly to the Raspberry Pi. And 10-digit 3CX calls will be forwarded to the Raspberry Pi as traditional outbound calls. They will be processed just as if you had dialed a 10-digit call from a Raspberry Pi extension. For example, if you have a registered Google Voice trunk to handle 10-digit calls on the Raspberry Pi, then the same call path would be used for calls originating from 3CX extensions. And, yes, calls to the U.S. and Canada would still be free and would display the CallerID associated with the Raspberry Pi’s Google Voice trunk. You could get more creative and add an additional dialing prefix on the 3CX side to route specific types of calls to a designated outbound trunk on the Raspberry Pi side based upon the dialing prefix, but we’ll leave that as a homework project for you.
For incoming calls on the 3CX side, in addition to 4-digit local extension-to-extension calling, we can define the destination for incoming calls that originate from either a Raspberry Pi extension or from outside calls coming in from one of the Raspberry Pi’s provider trunks. These are managed by assigning one or more DIDs in the 3CX trunk configuration and then creating 3CX Inbound DID Rules that tell 3CX where to route calls to each defined DID. For 3CX softphone clients registered to extensions, it means your cellphone will ring whenever a call is routed to that particular extension. On the Raspberry Pi side, we create Incoming Call Routes for each DID to be routed to 3CX and specify our defined 3CX trunk as the destination for incoming calls from those DIDs. Not all DIDs on the Raspberry Pi have to be routed to the 3CX server obviously. That is merely one of many call destination options available to the administrator on the Raspberry Pi server.

Here’s a typical call path for an outside call that is placed to a Google Voice number registered with your Raspberry Pi. The Asterisk server running on the Raspberry Pi would answer the call placed to the Google Voice Trunk. Asterisk then would check for an Incoming Route on the Raspberry Pi with a DID matching the number of your Google Voice trunk. Finding a match, Asterisk would check for the desired destination of the call and would note that it is listed as the registered 3CX trunk. Asterisk would pass the call through this trunk to the 3CX server including its associated DID and CallerID info. The 3CX server would answer the incoming call and would check for an Incoming Route matching the DID passed from Asterisk. Finding a match, it would pass the call to the Extension specified in the Incoming Route. When 3CX rings the extension, it would also detect that a softphone was registered to that extension and would also ring the 3CX client on the user’s smartphone. The user answers the call on the 3CX client of their smartphone and begins a conversation. The free version of the 3CX server supports 8 simultaneous calls so you are unlikely to ever run out of call paths for calls in the home and small office environment.
Firewall Setup for Server Interconnection
Because the 3CX server is sitting in the Cloud, its firewall is configured automatically as part of the setup process. If your Raspberry Pi is sitting behind a NAT-based firewall, then you would need to map port UDP 5060 from the router on your public IP address to the private IP address of your Raspberry Pi. In addition, login to your Raspberry Pi as root using SSH and run /root/add-ip to whitelist the public IP address of your 3CX server in the cloud. Otherwise, the 3CX server cannot establish a connection to your Raspberry Pi.
Raspberry Pi Trunk Configuration
Using a browser, login to the web interface for FreePBX on your Raspberry Pi and choose Connectivity → Trunks → Add SIP (chan_sip) Trunk. Name the trunk remote. In the Outgoing Settings, make the entries shown below naming the trunk remote and using a secure secret that will be used to interconnect the two servers. The Register String looks like the following: main:secret@3CX-IP-Address where main is the 3CX server trunk name, secret is your secure secret, and 3CX-IP-Address is the 3CX public IP address.
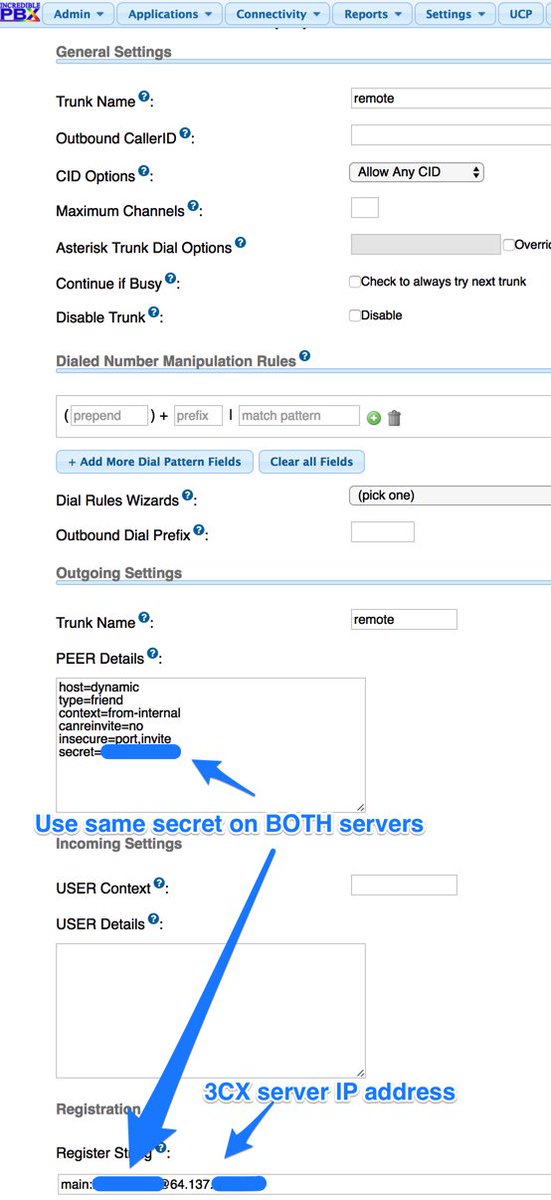
3CX Trunk Configuration
Using a browser, login to your 3CX server: https://3CX-IP-Address:5001 or http://3CX-IP-Address:5000. From your Dashboard, choose SIP Trunks → Add SIP Trunk. Create a Generic SIP Trunk and then fill in the blanks as shown below. For Registrar/Server/Gateway Hostname or IP, use the public IP address or FQDN of your Raspberry Pi. For Type of Authentication choose Outbound. The authentication credentials should be remote and the secure secret you chose, and the Main Trunk No should match the DID of the Google Voice trunk you set up on your Raspberry Pi. Then pick a default Destination for incoming calls.
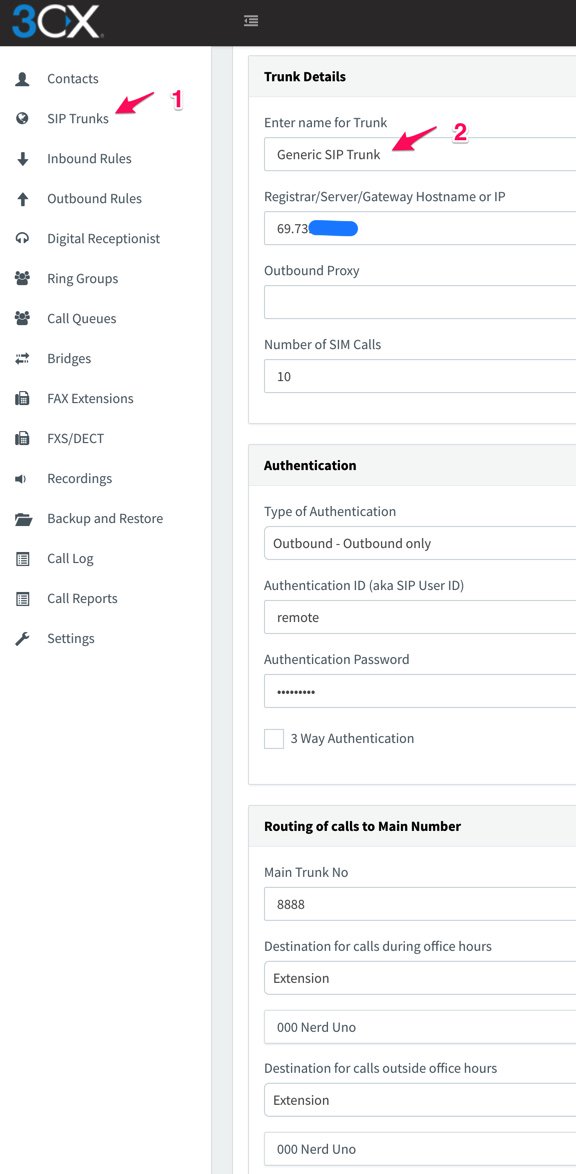
3CX Outbound Rules Configuration
Next, we need to tell 3CX which outgoing calls to send out through the Raspberry Pi trunk we just set up. In our example today, we’re going to send all 10-digit calls and 3-digit calls. The 10-digit calls will be routed out the Google Voice trunk on the Raspberry Pi side. And the 3-digit calls will be sent directly to Raspberry Pi extensions. So we’ll need two Outbound Rules.
For the first rule, choose Outbound Rules → Add. For the Rule Name, specify StandardOut. Apply the rule to Calls to Numbers with a length: 10. For Route 1, choose Generic SIP Trunk as the Destination. Click OK to save the new rule.
For the second rule, choose Outbound Rules → Add. For Rule Name, specify StandardInt. Apply the rule to Calls to Numbers with a length: 3. For Route 1, choose Generic SIP Trunk as the Destination. Click OK to save the new rule.
If you already have configured a 3CX smartphone client for one of your 3CX extensions, you now should be able to dial any 3-digit or 10-digit number and have the call processed through your new 3CX→RasPi trunk without any further setup assuming you’ve created a Google Voice trunk on the Raspberry Pi side. That wasn’t too hard, was it?
Routing Incoming Google Voice Calls to 3CX
Depending upon your own requirements, you may want to route incoming Google Voice calls or other trunks directly to an extension and/or softphone on your 3CX server. You obviously could set up multiple trunks of any type on the Raspberry Pi side and have the calls to each trunk routed to a different extension or softphone on the 3CX side. To enable this on the 3CX side, edit your Generic SIP Trunk and click the DIDs tab. Then Add each of the 10-digit DIDs of the Raspberry Pi trunks you wish to redirect. Next, create an Inbound Rule for every DID and tell 3CX where to route the calls.
On the Raspberry Pi side, add each of your Google Voice Trunks. Then create an Inbound Route for each DID and specify the Destination as Trunks → Remote (sip). The 3CX server will take care of routing the various incoming calls to each of the Google Voice trunks to its predefined extension and/or softphone. Enjoy!
Originally published: Monday, March 6, 2017
9 Countries Have Never Visited Nerd Vittles. Got a Friend in Any of Them https://t.co/wMfmlhiQ9y #asterisk #freepbx pic.twitter.com/TPFGZbqWB6
— Ward Mundy (@NerdUno) April 22, 2016

Need help with Asterisk? Visit the PBX in a Flash Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Some Recent Nerd Vittles Articles of Interest…
- A simpler Bridge setup is available in the paid versions of 3CX. [↩]


 JUST RELEASED: Visit the Incredible PBX Wiki
JUST RELEASED: Visit the Incredible PBX Wiki