Home » Incredible PBX » Ubuntu/Debian (Page 10)
Category Archives: Ubuntu/Debian
Our Best VoIP Cloud Platform Recommendations for 2021

Once upon a time, spending $15 to $50 a month for a cloud-based KVM platform to manage your Asterisk® PBX was considered a good deal. But, in the words of Bob Dylan, Times They Are A-Changin’. Our testing over the past couple years confirms that paying premium prices for Google or Amazon EC2 VoIP platforms is nothing short of a waste of money. Today we’re pleased to recommend five cloud providers to host your VoIP server that range in price from $2 to $5 a month. We’ve used all five and have never experienced a single hiccup. Better yet, you won’t have to worry about power outages, IP address changes, and hardware failures. All five of these providers offer Debian 10 and CentOS 7 platforms to complement Incredible PBX 2021, Incredible PBX 2021 PUBLIC, and Incredible PBX 2020 and PUBLIC implementations.
What separates our two $5 a month providers from the rest of the pack are three noteworthy considerations: business longevity, location diversity, and scalability. While Vultr and Digital Ocean both provide referral credits to Nerd Vittles, suffice it to say that has no bearing on our unqualified endorsement of these two platforms. Both also offer system backups for an additional 20% of the monthly platform cost. For those with PBX platform requirements that don’t exceed 10 simultaneous calls, the $5 offerings are more than adequate. And, if your requirements change moving forward, it’s easy to scale up to a more robust platform.
In the middle of the pack price-wise is OVH starting at $3.50 a month for their 100Mbps Starter KVM with a free snapshot. For those in the United States, their nearest data center is in Eastern Canada; however, multiple locations are available in Europe and the Asian Pacific.
Last but not least are two more recent providers. HotlineServers offers a $3 a month platform using our coupon code of voip2021. You can add off-site backups for an additional 80¢ a month. Their data center offerings include New York, Chicago, Miami, and Los Angeles with some of the best performance specs we have ever seen. CrownCloud offers a $25 a year platform with a free snapshot and data centers in Los Angeles, Atlanta, and Western Europe. By request, they also will load an Incredible PBX 2020 image that installs in under a minute.
For our latest recommendations on all things VoIP, check out the new Incredible PBX Wiki.
Originally published: Monday, January 11, 2021

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

Happy New Year: Introducing Incredible PBX 2021 for Debian

Shifting gears is never easy, and sometimes it takes ill-advised corporate blunders to move the needle. But IBM®’s decimation of the CentOS project last month coupled with the Sangoma® Ransomware fiasco were just the motivation we needed to shift into overdrive and explore alternatives for the Incredible PBX® 2021 project. After six beta releases, we are delighted to introduce Incredible PBX 2021 with ClearlyIP’s FreePBX® 15 module protection and your choice of either Asterisk® 16 or the Asterisk 18 LTS release.
Before we get started, we want to offer our special thanks to the many talented individuals on the VoIP-Info.org Forum and the ClearlyIP development team who helped to bring this open source product to fruition. Keep in mind that it was produced during this holiday season without missing a beat and in spite of 2020’s Covid-19 pandemic and the Sangoma® infamous security breach, the handling of which was so bad that we can’t muster enough tact to write about it. With Incredible PBX 2021, Sangoma Ransomware protection is available.
Setting Up a Debian Platform for Incredible PBX 2021
If you’re using on-premise hardware, begin by downloading the netinst ISO image of Debian 10 for amd64. Follow our previous tutorials for tips on installation with VirtualBox or VMware ESXi. If you’d prefer to experiment in the cloud for about a penny an hour, open an account at Vultr or Digital Ocean using our referral links that support the Nerd Vittles project. You’ll also get some free credit to try out the service. Then create a new $5/month Debian 10, 64-bit instance in your favorite city.
If you’re using other cloud platforms with a Debian 10 offering, we strongly recommend a KVM platform. Also be advised that all Debian 10 releases are not equal. So be sure to upgrade to the latest Debian 10 release before you proceed. Here are the steps:
apt-get update --allow-releaseinfo-change apt-get upgrade # GRUB prompt: install to /dev/vda # SSH prompt: keep local version reboot
If your PBX is sitting behind a NAT-based router, you’ll need to redirect incoming UDP 5060-5061 and UDP 10000-20000 traffic to the private IP address of your server. This is required for all of the SIP providers included in the Incredible PBX 2021 build. Otherwise, all inbound calls will fail.
Installing Incredible PBX 2021 on Debian 10 Server
Once your Debian 10 platform is up and running, login as root using SSH or Putty. If you wish to use the default Asterisk 18 platform, issue the commands below to kick off the install. If you’d prefer to stick with Asterisk 16 for the time being and perhaps upgrade to Asterisk 18 later with the included upgrade script, then edit the script once you download it and change 18 to 16 in line 34 of the script before executing it.
wget http://incrediblepbx.com/IncrediblePBX2021.sh chmod +x IncrediblePBX2021.sh ./IncrediblePBX2021.sh
At about 5 minutes into the install procedure, you’ll be prompted for your telephone country code. It’s 1 for Canada and the United States. Just before the install completes, you’ll be prompted to save your default IPtables setup. Once the installation completes, reboot and you should be good to go.
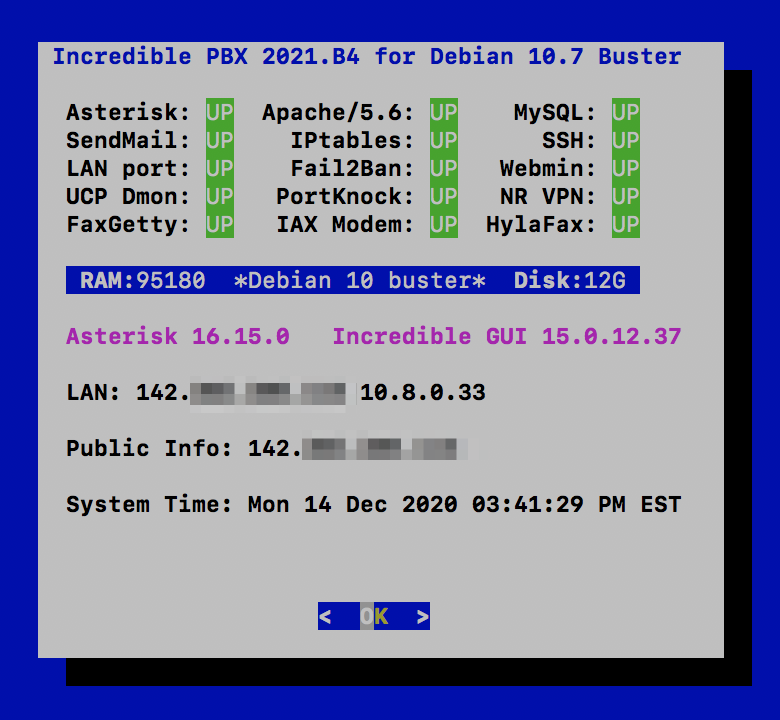
After you log back in following a reboot, check the version of Debian 10 in the pbxstatus display. If it’s less than 10.7, issue the following commands to bring your server up to Debian 10.10 or later, not Debian 11. Do NOT do this before the base install is finished, or Asterisk may fail to install properly.
apt-get update apt-get upgrade -y

Next Steps with Incredible PBX 2021
Before you can manage your PBX through a web browser, you first will need to set the admin passwords for FreePBX, Apache web apps such as Reminders and AsteriDex, and AvantFax (if you are using Incredible Fax). These all can be set by logging into your server as root and issuing the following commands: admin-pw-change, apache-pw-change, and avantfax-pw-change. The AvantFax password can also be reset with a browser by first logging in as admin with a password of password.
Outbound mail functionality needs to be working so that you can receive voicemail messages and faxes by email. To prevent SPAM, most ISPs and ITSPs block messages from downstream mail servers. That would be you. The easiest way to resolve this is to configure SendMail using Gmail as an SMTP Smarthost. You obviously need a Gmail account to implement this and, if you have turned on two-factor authentication for your Gmail account, you also will need to obtain an App password for your Gmail account, and use that in lieu of your regular Gmail password when configuring SendMail. With your Gmail username and password in hand, log into your server as root and run: /root/enable-gmail-smarthost-for-sendmail.
If your Incredible PBX 2021 is hosted with a cloud provider, be advised that many providers do not include a swap file as part of their offering. FreePBX requires a swap file. To add one, issue this command after logging into your server as root: /root/create-swapfile-DO.
To correctly set the time on your PBX, run: /root/timezone-setup.
By default, the voicemail password for each of the configured extensions (701-705) is set to the extension number. This means the user will be prompted to set a voicemail password on the first login to voicemail for each extension. A phone must be registered to the actual extension to access its voicemail account. For example, once a phone is registered to extension 701, the voicemail setup can be accessed by dialing *98701.
If you want to send and receive faxes with Incredible PBX 2021, run the following script while logged into your server as root: /root/incrediblefax2020-debian10.sh. When prompted, accept all the defaults. Once the HylaFax and AvantFax components are installed, reboot your server. To send faxes, click on the AvantFax tab in the FreePBX GUI and enter your login credentials (default: admin/password). To receive incoming faxes once you have configured a trunk and DID for your PBX, login to the FreePBX GUI as admin. Navigate to Connectivity -> Inbound Routes. For each of your DIDs on which you wish to receive faxes, select the inbound route and click the Fax tab. Review the Default Inbound Route Fax settings for proper setup.
NOTE: If you get a database error when you attempt to access AvantFax from a web browser, log into your server as root and reinstall the AvantFax database: ./avantfax-db-replace.
Overview of the Initial Asterisk Setup Process
For those new to PBXs, here’s a two paragraph summary of how Voice over IP (VoIP) works. Phones connected to your PBX are registered with Extensions so that they can make and receive calls. When a PBX user picks up a phone and dials a number, an Outbound Route tells the PBX which Trunk to use to place the call based upon established dialing rules. Unless the dialed number is a local extension, a Trunk registered with some service provider accepts the call, and the PBX sends the call to that provider. The provider then routes the call to its destination where the recipient’s phone rings to announce the incoming call. When the recipient picks up the phone, the conversation begins.
Looking at things from the other end, when a caller somewhere in the world wishes to reach you, the caller picks up a telephone and dials a number known as a DID that is assigned to you by a provider with whom you have established service. When the provider receives the call to your DID, it routes the call to your PBX based upon destination information you established with the provider. Your PBX receives the call with information identifying the DID of the call as well as the CallerID name and number of the caller. An Inbound Route on your PBX then determines where to send the call based upon that DID and CallerID information. Typically, a call is routed to an Extension, a group of Extensions known as a Ring Group, or an IVR or AutoAttendant giving the caller choices on routing the call to the desired destination. Once the call is routed to an Extension, the PBX rings the phone registered to that Extension. When you pick up the phone, the conversation begins.
Configuring Trunks with Incredible PBX GUI
Perhaps the most difficult component to configure in the PBX is the Trunk. Almost every provider has a different way of doing things. We’ve taken some of the torture out of the exercise by providing a script which will configure settings for dozens of providers in seconds. Once installed, all you need to do is edit the desired Trunk (Connectivity:Trunks), change the Disable Trunk entry to No, and insert your credentials in both the PEER Details and Registration string of the SIP Settings Outgoing and Incoming tabs. Skyetel is enabled by default and needs no setup on the PBX side.
Configuring Skyetel for Incredible PBX 2021
If you’ve decided to go with Skyetel, here’s the drill. Sign up for Skyetel service and take advantage of the Nerd Vittles specials. First, complete the Prequalification Form here. You then will be provided a link to the Skyetel site to complete your registration. Once you have registered on the Skyetel site and your account has been activated, open a support ticket and request the $10 credit for your account by referencing the Nerd Vittles special offer. Once you are satisfied with the service, fund your account as desired, and Skyetel will match your deposit of up to $250 simply by opening another ticket. That gets you up to $500 of half-price calling. Credit is limited to one per person/company/address/location. Effective 10/1/2023, $25/month minimum spend required.
Skyetel does not use SIP registrations to make connections to your PBX. Instead, Skyetel utilizes Endpoint Groups to identify which servers can communicate with the Skyetel service. An Endpoint Group consists of a Name, an IP address, a UDP or TCP port for the connection, and a numerical Priority for the group. For incoming calls destined to your PBX, DIDs are associated with an Endpoint Group to route the calls to your PBX. For outgoing calls from your PBX, a matching Endpoint Group is required to authorize outbound calls through the Skyetel network. Thus, the first step in configuring the Skyetel side for use with your PBX is to set up an Endpoint Group. Here’s a typical setup for Incredible PBX 2021:
- Name: MyPBX
- Priority: 1
- IP Address: PBX-Public-IP-Address
- Port: 5060
- Protocol: UDP
- Description: my.incrediblepbx.com
To receive incoming PSTN calls, you’ll need at least one DID. On the Skyetel site, you acquire DIDs under the Phone Numbers tab. You have the option of Porting in Existing Numbers (free for the first 60 days after you sign up for service) or purchasing new ones under the Buy Phone Numbers menu option.
Once you have acquired one or more DIDs, navigate to the Local Numbers or Toll Free Numbers tab and specify the desired SIP Format and Endpoint Group for each DID. Add SMS/MMS and E911 support, if desired. Call Forwarding and Failover are also supported. That completes the VoIP setup on the Skyetel side. System Status is always available here.
Configuring VoIP.ms for Incredible PBX 2021
To sign up for VoIP.ms service, may we suggest you use our signup link so that Nerd Vittles gets a referral credit for your signup. Once your account is set up, you’ll need to set up a SIP SubAccount and, for Authentication Type, choose Static IP Authentication and enter your Incredible PBX 2021 server’s public IP address. For Transport, choose UDP. For Device Type, choose Asterisk, IP PBX, Gateway or VoIP Switch. Order a DID in their web panel, and then point the DID to the SubAccount you just created. Be sure to specify atlanta1.voip.ms as the POP from which to receive incoming calls. In the Incredible PBX GUI, be sure to enable the VoIP.ms trunk.
Configuring V1VoIP for Incredible PBX 2021
To sign up for V1VoIP service, sign up on their web site. Then login to your account and order a DID under the DIDs tab. Once the DID has been assigned, choose View DIDs and click on the Forwarding button beside your DID. For Option #1, choose Forward to IP Address/PBX. For the Forwarding Address, enter the public IP address of your server. For the T/O (timeout) value, set it to 2o seconds. Then click the Update button. Under the Termination tab, create a new Endpoint with the public IP address of your server so that you can place outbound calls through V1VoIP. In the Incredible PBX GUI, be sure to enable all of the V1VoIP trunks.
Configuring Anveo Direct for Incredible PBX 2021
To sign up for Anveo Direct service, sign up on their web site and then login. After adding funds to your account, purchase a DID under Inbound Service -> Order DID. Next, choose Configure Destination SIP Trunk. Give the Trunk a name. For the Primary SIP URI, enter $[E164]$@server-IP-address. For Call Options, select your new DID from the list. You also must whitelist your public IP address under Outbound Service -> Configure. Create a new Call Termination Trunk and name it to match your server. For Dialing Prefix, choose six alphanumeric characters beginning with a zero. In Authorized IP Addresses, enter the public IP address of your server. Set an appropriate rate cap. We like $0.01 per minute to be safe. Set a concurrent calls limit. We like 2. For the Call Routing Method, choose Least Cost unless you’re feeling extravagant. For Routes/Carriers, choose Standard Routes. Write down your Dialing Prefix and then click the Save button.
Before you can make outbound calls through Anveo Direct from your PBX, you first must configure the Dialing Prefix that you wrote down in the previous step. Log into the GUI as admin using a web browser and edit the Anveo-Out trunk in Connectivity -> Trunks. Enable the Trunk. Then click on the custom-Settings tab and replace anveo-pin with your actual Dialing Prefix. Click Submit and Apply Config to complete the setup. In the Incredible PBX GUI, be sure to enable all of the remaining Anveo trunks.
By default, incoming Anveo Direct calls will be processed by the Default inbound route on your PBX. If you wish to redirect incoming Anveo Direct calls using DID-specific inbound routes, then you’ve got a bit more work to do. In addition to creating the inbound route using the 11-digit Anveo Direct DID, enter the following commands after logging into your server as root using SSH/Putty:
cd /etc/asterisk
echo "[from-anveo]" >> extensions_custom.conf
echo "exten => _.,1,Ringing" >> extensions_custom.conf
echo "exten => _.,n,Goto(from-trunk,\\${SIP_HEADER(X-anveo-e164)},1)" >> extensions_custom.conf
asterisk -rx "dialplan reload"
Configuring Extensions with Incredible PBX GUI
Extensions are created using the Incredible PBX GUI: Applications:Extensions. Many SIP phones expect extensions to communicate on UDP port 5060. If this is the case with your SIP phone or softphone, then always create Chan_SIP extensions which communicate on UDP 5060. If your SIP phone or softphone provide port flexibility, then you have a choice in the type of SIP extension to create: Chan_SIP or the more versatile PJSIP (UDP 5061). Just remember to always configure SIP extensions with NAT Mode=YES in the Advanced tab. If your VoIP phones or softphones support IAX connectivity, you may wish to consider IAX extensions which avoid NAT problems.
When you create a new Extension, a new entry is automatically created in the PBX Internal Directory. If you wish to allow individual users to manage their extensions or use the WebRTC softphone, then you will also have to create a (very) secure password for User Control Panel (UCP) access. Choose Admin:User Management and click on the key icon of the desired extension to assign a password for UCP and WebRTC access.
Configuring a Desktop Softphone for Incredible PBX
We’re in the home stretch now. You can connect virtually any kind of telephone to your new PBX. Plain Old Phones require an analog telephone adapter (ATA) which can be a separate board in your computer from a company such as Digium. Or it can be a standalone SIP device such as ObiHai’s OBi100 or OBi110 (if you have a phone line from Ma Bell to hook up as well). SIP phones can be connected directly so long as they have an IP address. These could be hardware devices or software devices such as the YateClient softphone. We’ll start with a free one today so you can begin making calls. You can find dozens of recommendations for hardware-based SIP phones both on Nerd Vittles and the PIAF Forum when you’re ready to get serious about VoIP telephony.
We recommend YateClient for Windows which is free. Download it from here. Run YateClient once you’ve installed it and enter the credentials for the 701 extension on Incredible PBX. You can find them by running /root/show-passwords. You’ll need the IP address of your server plus your extension 701 password. In the YateClient, fill in the blanks using the IP address of your Server, 701 for your Username, and whatever Password was assigned to the extension when you installed Incredible PBX. Click OK to save your entries.
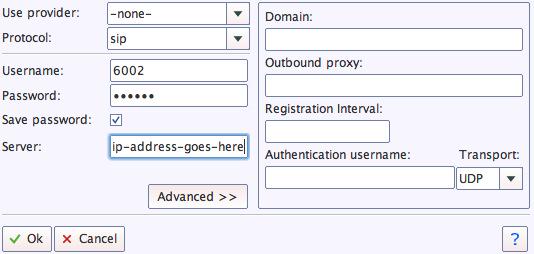
Once you are registered to extension 701, close the Account window. Then click on YATE’s Telephony Tab and place some test calls to the numerous apps that are preconfigured on Incredible PBX. Dial a few of these to get started:
DEMO - Apps Demo 123 - Reminders 947 - Weather by ZIP Code 951 - Yahoo News TODAY - Today in History LENNY - The Telemarketer's Worst Nightmare
If you are a Mac user, another great no-frills softphone is Telephone. Just download and install it from the Mac App Store. For Android users, check out the terrific new VitalPBX Communicator. Works flawlessly with Incredible PBX.
Configuring a Softphone Extension on a Smartphone
Adding an Incredible PBX extension to your smartphone gets a little trickier. Whether you’re an iPhone or Android lover, all smartphones use batteries, and you don’t want to drain your battery by running a softphone as a foreground app all the time. Fortunately, you now have some choices in softphones engineered to work without draining your battery. While they all cost money, it’s not much money. We’ve written about all the choices, and you’ll find the links in our Softphone Provider Recommendations on the new Incredible PBX Wiki.
With PJsip extensions, you’re not limited to a single phone connection at a time, and we’ve preconfigured extension 701 to support five simultaneous connections. The setup on the softphone side is simple. For the server, enter the actual IP address of your PBX in the following format: 22.33.44.55:5061. Then enter 701 for the username and enter the password assigned to the 701 extension on your PBX. When an incoming call arrives, all the phones registered to extension 701 will ring simultaneously. Simply answer the call on the phone that is most convenient.
Configuring Outbound Routes in Incredible PBX GUI
Outbound Routes serve a couple of purposes. First, they assure that calls placed by users of your PBX are routed out through an appropriate trunk to reach their destination in the least costly manner. Second, they serve as a security mechanism by either blocking or restricting certain calls by requiring a PIN to complete the calls. Never authorize recurring charges on credit cards registered with your VoIP providers and, if possible, place pricing limits on calls with your providers. If a bad guy were to break into your PBX, you don’t want to give the intruder a blank check to make unauthorized calls. And you certainly don’t want to join the $100,000 Phone Bill Club.
To create outbound routes in the Incredible PBX GUI, navigate to Connectivity:Outbound Routes and click Add Outbound Route. In the Route Settings tab, give the Outbound Route a name and choose one or more trunks to use for the outbound calls. In the Dial Patterns tab, specify the dial strings that must be matched to use this Outbound Route. NXXNXXXXXX would require only 10-digit numbers with the first and fourth digits being a number between 2 and 9. Note that Outbound Routes are searched from the top entry to the bottom until there is a match. Make certain that you order your routes correctly and then place test calls watching the Asterisk CLI to make sure the calls are routed as you intended.
Configuring Inbound Routes in Incredible PBX GUI
Inbound Routes, as the name implies, are used to direct incoming calls to a specific destination. That destination could be an extension, a ring group, an IVR or AutoAttendant, or even a conference or DISA extension to place outbound calls (hopefully with a very secure password). Inbound Routes can be identified by DID, CallerID number, or both. To create Inbound Routes, choose Connectivity:Inbound Routes and then click Add Inbound Route. Provide at least a Description for the route, a DID to be matched, and the Destination for the incoming calls that match. If you only want certain callers to be able to reach certain extensions, add a CallerID number to your matching criteria. You can add Call Recording and CallerID CNAM Lookups under the Other tab.
Audio Issues with Incredible PBX 2021
If you experience one-way or no audio on some calls, add your external IP address and LAN subnet in the GUI by navigating to Settings -> Asterisk SIP Settings. In the NAT Settings section, click Detect Network Settings. Click Submit and Apply Settings to save your changes.
Security Considerations with Incredible PBX 2021
Incredible PBX 2021 includes a rock-solid firewall that limits access to preferred providers and individuals whose IP addresses you have whitelisted. Unfortunately, this may not insulate your server from FreePBX 15 irregularities if, in fact, Sangoma’s signing key was compromised in the October 2020 Ransomware Attack. Sangoma either doesn’t know or isn’t telling. Keep in mind that Sangoma didn’t mention the October breach either until someone else exposed it. Sangoma’s latest press release is available here.
The good news is Incredible PBX 2020 and 2021 platforms include a unique ClearlyIP feature that lets us manage which modules and versions can be installed. It works exactly like what ClearlyIP has documented in their must-read blog post, and we’ve built a locked version that rolls back all of the modules to dates before the Sangoma breach. The good news is, with Incredible PBX, you don’t have to jump through all the hoops covered in the ClearlyIP article to fully insulate your server from the Ransomware breach. We’ve done the work for you.
For those with mission-critical platforms, we’d recommend immediate implementation of what follows. For everyone else, it’s your choice whether to wait and see if there is a breach of the signing certificate with malicious modules. If you opt to wait and see, MAKE FREQUENT BACKUPS.
Here’s how to roll back all of your modules to dates before the breach. Login to the FreePBX GUI as admin and navigate to Settings > Advanced Settings. Drop down to the Lock Version field and change 15.19.11.001 to 15.19.11.003. Save your changes and reload your dialplan. Then use Module Admin to roll back any installed modules that are newer than the safe versions shown.
Our extra special thanks goes to Tony Lewis and the ClearlyIP team for providing this invaluable resource. Somehow we knew it would come in handy sooner or later. Unfortunately, that day has come.
Adding Incredible PBX 2021 to an OpenVPN Network
We previously have documented the procedure for creating an OpenVPN server as well as OpenVPN client templates (.ovpn). If you need a refresher, the tutorial is here. To add your Incredible PBX 2021 server to an existing OpenVPN network, begin by creating an incrediblepbx2021.ovpn template on your OpenVPN server. Be sure to comment out or delete the setenv line in the template. Then copy this template to /etc on your Incredible PBX 2021 server. Next, issue the following commands to put the remaining pieces in place:
cp -p /root/openvpn-start /etc/. echo "[Unit] Description=openvpn2021 ConditionPathExists=/etc/openvpn-start After=rclocal.service [Service] Type=forking ExecStart=/etc/openvpn-start /etc/incrediblepbx2021.ovpn TimeoutSec=0 StandardOutput=tty RemainAfterExit=yes PermissionsStartOnly=true SysVStartPriority=99 [Install] WantedBy=multi-user.target" > /etc/systemd/system/openvpn2021.service
Finally, enable the new openvpn2021.service and reboot your server. The OpenVPN IP address should now appear on the LAN line in pbxstatus:
systemctl enable openvpn2021.service reboot
Incredible PBX 2021 Administration
We’ve eased the pain of administering your new PBX with a collection of scripts which you will find in the /root folder after logging in with SSH or Putty. Here’s a quick summary of what each of the scripts does.
add-fqdn is used to whitelist a fully-qualified domain name in the firewall. Because Incredible PBX 2021 blocks all traffic from IP addresses that are not whitelisted, this is what you use to authorize an external user for your PBX. The advantage of an FQDN is that you can use a dynamic DNS service to automatically update the IP address associated with an FQDN so that you never lose connectivity.
add-ip is used to whitelist a public IP address in the firewall. See the add-fqdn explanation as to why this matters.
del-acct is used to remove an IP address or FQDN from the firewall’s whitelist.
admin-pw-change is used to set the admin password for access to the FreePBX/Incredible PBX web GUI using a browser pointed to the local IP address of your server.
apache-pw-change is used to set the admin password for access to Apache/Incredible PBX apps including AsteriDex and Reminders. This provides a password layer of protection for access to these applications.
avantfax-email-change is used to change the destination email address for incoming faxes.
avantfax-pw-change is used to change your admin password for the AvantFax web console.
iaxmodem-restart is used to restart the modems used to send and deliver faxes. The pbxstatus display will tell you whether the IAXmodems are down.
incrediblebackup2021 makes a backup of critical components on your PBX to a tarball saved in /backup. This should be copied to safe location off-site for a rainy day.
incrediblerestore2021 restores a backup file which has been copied to the /backup folder.
ipchecker is a script which deciphers the public IP addresses associated with whitelisted FQDNs created with add-fqdn on your server. If any of the addresses have changed, the firewall is restarted after updating the IP addresses. By default, it is executed every 10 minutes by /etc/crontab.
licenses.sh displays the license associated with each of the FreePBX modules on your server.
logos-b-gone removes proprietary artwork from your PBX and is no longer necessary with the included IncrediblePBX FreePBX module.
mime-construct is a command-line utility to send emails with attachments.
neorouter-login is a script to add your PBX to a NeoRouter VPN. Tutorial here.
odbc-gen.sh is a script that was run to generate the ODBC settings for Asterisk. Do NOT use it.
openvpn-start is a script to add your PBX to an existing OpenVPN network using an .ovpn config file. Tutorial here.
pbxstatus displays status of all major components of Incredible PBX 2021.
pptp-install is a script to create a PPTP network connection for your PBX. Tutorial here.
purge-cdr-cel-records removes all CDR and CEL records from the MySQL database.
reset-conference-pins is a script that automatically and randomly resets the user and admin pins for access to the preconfigured conferencing application. Dial C-O-N-F from any registered SIP phone to connect to the conference.
reset-extension-passwords is a script that automatically and randomly resets ALL of the SIP passwords for extensions 701-705. Be careful using this one, or you may disable existing registered phones and cause Fail2Ban to blacklist the IP addresses of those users. HINT: You can place a call to the Ring Group associated with all five extensions by dialing 777.
reset-reminders-pin is a script that automatically and randomly resets the pin required to access the Telephone Reminders application by dialing 123. It’s important to protect this application because a nefarious user could set up a reminder to call a number anywhere in the world assuming your SIP provider’s account was configured to allow such calls.
show-feature-codes is a cheat sheet for all of the feature codes which can be dialed from any registered SIP phone. It documents how powerful a platform Incredible PBX 2021 actually is. A similar listing is available in the GUI at Admin -> Feature Codes.
show-passwords is a script that displays most of the passwords associated with Incredible PBX 2021. This includes SIP extension passwords, voicemail pins, conference pins, telephone reminders pin, and your Anveo Direct outbound calling pin (if configured). Note that voicemail pins are configured by the user of a SIP extension the first time the user accesses the voicemail system by dialing *97.
sig-fix disables Module Signature Checking in the FreePBX GUI. This should not be necessary unless you have added or edited FreePBX Modules with missing module signatures.
sms-skyetel is a script to send SMS messages using a Skyetel trunk.
sms-voip.ms is a script to send SMS messages using a VoIP.ms trunk.
sms-blast, sms-blaster, and sms-dictator are scripts for message blasting. Tutorial here.
switch-to-php5.6 is a script to disable PHP 7.3 and set PHP 5.6 as the default version for your PBX. PHP 5.6 is required to use AvantFax. It is the default configuration for Incredible PBX 2021. The current default PHP version is displayed in the Apache listing of pbxstatus.
switch-to-php7.3 is a script to disable PHP 5.6 and set PHP 7.3 as the default version for your PBX. You cannot use AvantFax when PHP 7.3 is the default.
timezone-setup is a script to set the timezone for your PBX.
update-IncrediblePBX is a script that runs the Automatic Update Utility whenever you login to your server as root. These updates typically resolve bugs and security issues with your PBX. Do NOT remove it.
upgrade-asterisk16 is a script that runs on Asterisk 16 platforms to upgrade your PBX to the latest release of Asterisk 16.
upgrade-asterisk18 is a script that runs on both Asterisk 16 and 18 platforms to upgrade your PBX to the latest release of Asterisk 18.
wolfram is a script to deploy Wolfram Alpha on your PBX. Tutorial here.
Forwarding Calls to Your Cellphone. Keep in mind that inbound calls to your DIDs automatically ring all five SIP extensions, 701-705. The easiest way to also ring your cellphone is to set one of these five extensions to forward incoming calls to your cellphone. After logging into your PBX as root, issue the following command to forward calls from extension 705 to your cellphone: asterisk -rx "database put CF 705 6781234567"
To remove call forwarding: asterisk -rx "database del CF 705"
Keeping FreePBX 15 Modules Current
We strongly recommend that you periodically update all of your FreePBX modules to eliminate bugs and to reduce security vulnerabilities. From the Linux CLI, log into your server as root and issue the following commands:
rm -rf /tmp/* fwconsole ma upgradeall fwconsole reload /root/sig-fix systemctl restart apache2 /root/sig-fix
Ready to turn Incredible PBX 2021 into a PUBLIC-Facing PBX? Here’s how.

Originally published: Friday, January 1, 2021

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

Deploying an Incredible PBX 2021 PUBLIC Server

With the almost overnight popularity of the new Clearly Anywhere softphone which provides Incredible PBX connectivity from virtually anywhere, we wanted to add a missing piece to our Incredible PBX 2021 release. Because softphones need connectivity on both cellular networks and using Wi-Fi with dynamic IP addresses in multiple locations, exclusive whitelist-based access to Incredible PBX platforms simply was no longer feasible. Additionally, due to Clearly Anywhere’s tight integration with the FreePBX® User Control Panel (UCP), remote access to UCP for mobile users has become more important particularly with the new QR Code auto-configuration option for Clearly Anywhere clients.
Safely deploying a public-facing Asterisk® server with full FreePBX functionality has become the Holy Grail for Nerd Vittles in 2020. Today we tackle it with the new Incredible PBX® 2021 Debian platform featuring the latest releases of Asterisk 16 and FreePBX 15. The icing on today’s cake is an additional offer from Skyetel that supplements the current Nerd Vittles BOGO offer of up to $500 in half-priced VoIP services. Skyetel now starts you off with a $10 credit just for opening an account here. Then, after you have had an opportunity to kick the tires and perhaps purchase a DID for a buck, you can make $9 worth of phone calls before deciding whether to take advantage of the BOGO special by making a purchase of up to $250 and having Skyetel match your contribution. Once you have funded your account, you then can also take advantage of Skyetel’s free number porting offer for the next 60 days. To get your $10 credit, just open a ticket and request the $10 Nerd Vittles credit once you’ve signed up. To get the Nerd Vittles BOGO price match and take advantage of free number porting, simply open another ticket once you have added up to $250 to your account. Effective 10/1/2023, $25/month minimum spend required.
Making the Case for a Public-Facing PBX
We’ve had folks using our Incredible PBX PUBLIC implementation for over a year, and today we expand the offering to support the new Incredible PBX 2021 with Debian 10. Early on, the first question we got was why anyone would want to do this. After all, PBX in a Flash 3 and Incredible PBX for the better part of a decade have been deployed with a whitelist using the Travelin’ Man 3 firewall, and there’s never been a security issue. So why switch horses now? The short answer is mobile users with dynamic IP addresses. If all the users of your PBX are sitting behind the same NAT-based router with static IP addresses, the Travelin’ Man 3 design is perfect. The bad guys could never even see your server. But if some of your users either reside or travel outside your home base or if you want calls to follow you on your smartphone with Clearly Anywhere when you leave home or the office, then Travelin’ Man 3 blocked SIP access from these remote phones until their new IP addresses were whitelisted. Multiply this by dozens or hundreds of users, and network management suddenly became a full-time job. Yes, we’ve had tools such as dynamic DNS and PortKnocker to ease the pain, but it still was a knuckle-drill for mobile users. And, in today’s Covid world, much of the workforce is quickly morphing into mobile users without a traditional desk at any office. What we were also beginning to see were homegrown "improvements" to the IPtables firewall where users that didn’t appreciate the risks were exposing their servers to SIP attacks simply to ease the pain of connecting remotely.
The world also is becoming more SIP savvy. Just as folks are learning that a $35 antenna can provide an awesome collection of 4K Ultra HD TV channels without the expense of a monthly cable bill, others are learning that a SIP telephone or softphone app on your smartphone can provide free calls to and from anybody with a SIP URI without sharing your communications with Facebook or Microsoft. A public-facing PBX makes free worldwide SIP calling a reality.
Building the Base Platform for Incredible PBX PUBLIC
To get started today, begin by installing Incredible PBX 2021 using our latest tutorial. We strongly recommend a cloud-based KVM platform with a static IP address on the Internet.
Once you have set up your Incredible PBX 2021 server, the next step is to assign one or two fully-qualified domain names (FQDNs) to your server. You can have one FQDN for registering SIP extensions and a different one for anonymous SIP (invite) access to your server, or you can use the same FQDN for both. Security through obscurity provides an extra layer of protection for your server so choose your FQDNs carefully. sip.yourname.com provides almost no protection while f246g.yourname.com pretty much assures that nobody is going to guess your domain name. This is particularly important with the FQDN for SIP registrations because registered extensions on your PBX can obviously make phone calls that cost money. If you don’t have your own domain, you can always obtain a free FQDN from a service such as NoIP.com.
By default, Incredible PBX 2021 configures five extensions (701-705) and a Ring Group for those extensions (777) as well as four trunks. With Skyetel, your PBX is ready to make and receive calls as soon as you sign up. With the other three trunk providers, you only need to enable the trunk. You can add as many additional providers and extensions as you like and modify the ring group to meet your needs. To get started, be sure to configure the correct time zone for your server as this affects delivery of reminders. Run /root/timezone-setup. Next, set a secure password for admin access to the FreePBX GUI modules. Run /root/admin-pw-change. Then set a secure password for admin access to web applications such as AsteriDex, Reminders, and User Control Panel. Run /root/apache-pw-change. In addition to reviewing your extensions and ring group, review the default inbound route and choose the destination for the incoming calls from your provider. Finally, configure the outbound route to use the provider sequence desired. By default, it uses Skyetel for outbound calls.
If you plan to use Clearly Anywhere, you’ll need to add at least one PJsip extension on your PBX or use the preconfigured PJsip extension 701. Simply navigate to Applications -> Extensions in the FreePBX GUI. Choose Add Extension -> Add PJsip Extension. In the General tab, insert an extension number in User Extension and Display Name, e.g. 707. In the Advanced tab, set Max Contacts to 11 which will let you connect up to 5 Clearly Anywhere softphones to the extension. Click Submit and Reload Dialplan when prompted. Go back into the new extension and make note of your new credentials for User Manager. You’ll need these for Clearly Anywhere. Remember to also add the PJsip extension to the Inbound Route for your incoming calls.
Going Public with Incredible PBX 2021
Once you’ve tested making and receiving calls with your new server, you’re ready to convert it into a public-facing PBX. Before proceeding, remove any whitelist entries you’ve added using add-ip and add-fqdn by running del-acct. These can be added back after the GO-PUBLIC-2021 install script is run. In order to run the install script below, you’ll need your FQDNs that you chose above, plus a port number for future SSH/Putty access to your server, plus a list of the extensions you wish to make available for public access to your PBX. These whitelisted extensions can be reached via SIP URI from anywhere in the world by anybody. It works just like your old MaBell phone. Anybody, anywhere can dial your number. What’s changed is now the calls are free. So choose your list carefully. We recommend using the year you were born for your SSH port to keep things simple for you. Once the GO-PUBLIC-2021 script has been run, you can only access your PBX via SSH/Putty at the new port, for example: ssh -p 1990 root@yourFQDN.com
Now we’re ready to run the install script. It takes less than a minute. Before you begin, log out of ALL SIP extensions you have previously registered with Incredible PBX 2021 and change the server destination from an IP address to the FQDN you plan to assign to SIP registrations. Otherwise, these IP addresses will get banned while the install script is running below!
cd /root wget http://incrediblepbx.com/go-public-2021.tar.gz tar zxvf go-public-2021.tar.gz rm -f go-public-2021.tar.gz ./GO-PUBLIC-2021
A Few Words About Incredible PBX PUBLIC Security
As with all Incredible PBX servers, Incredible PBX 2021-PUBLIC includes the Automatic Update Utility. Please don’t disable it. It’s our only way to push updates to you if some vulnerability is discovered down the road. It gets run whenever you login to your server as root using SSH/Putty. Do so regularly and follow us on Twitter for security alerts. There’s also an Incredible PBX RSS Feed that is displayed when you login to the Incredible PBX GUI with a browser. It, too, includes security alerts and should be checked regularly. It’s your phone bill.
Incredible PBX 2021-PUBLIC uses the ipset utility in conjunction with the IPtables firewall to block several countries that have inordinately high concentrations of folks that try to break into VoIP servers. In addition, your public PBX includes the VoIP Blacklist which includes another 100,000 bad guys from around the globe. These blacklists get updated every night by a script which is run from /etc/crontab. For your own safety, don’t disable or delete /etc/update-voipbl.sh or the other components upon which it relies.
Here are some other things you should do regularly to assure that your server remains secure. Login via SSH/Putty as root and check pbxstatus after the Automatic Update Utility is run. With the exception of the fax components, all the other items should be green all the time. From the Linux CLI, run: iptables -nL. This will show your firewall rules and whether any IP addresses have been banned by Fail2Ban. If there are banned IP addresses that are not your own, please open a thread on the VoIP-Info Forum and let us know about it. If there are dozens of banned IP addresses, shutdown your server immediately until the problem is identified and resolved. If the IP addresses happen to be your own users because of using incorrect passwords or because of using a server IP address instead of its FQDN for SIP registrations, unban the IP address:
fail2ban-client set asterisk unbanip xxx.xxx.xxx.xxx
Finally, watch the Asterisk CLI periodically for abnormal activity: asterisk -rvvvvvvvvvv
Tightening Up SSH Server Access
You obviously need a very secure root password for access to your server using SSH/Putty. Changing the TCP port for SSH access avoids the script kiddies, but it doesn’t offer much protection from a determined cracker. SSH login attempts are monitored by Fail2Ban, but Fail2Ban has issues when a determined intruder is using a powerful computing platform such as Amazon EC2. The prudent solution is to disable SSH password access and use SSH Public Key Authentication as documented in the linked tutorial. Always, always use ssh-copy-id to copy your credentials to more than one desktop machine so that you don’t inadvertently lock yourself out of your PBX in case of a hardware failure. Then set PasswordAuthentication no in /etc/ssh/sshd_config and restart SSH: systemctl restart sshd.
Web Access to Incredible PBX 2021 PUBLIC
By default, web access to all apps including FreePBX, UCP, AvantFax, AsteriDex, and Reminders is limited to whitelisted IP addresses. For some implementations, particularly those using Clearly Anywhere, this may not be ideal as UCP can assist with user management of the PBX as well as QR code provisioning of Clearly Anywhere. The Apache web server can be used to manage web access so long as you understand the need to apply Apache security patches in a timely manner.
Assign the same FQDN that you use for SIP access to port 80 for the UCP application. Deploy OpenVPN on your server and use the PBX’s OpenVPN IP address for general access to all web applications we listed above. If you’d like public access to the FreePBX GUI, assign web access for it to another random port, e.g. 8080 in our example below. Block web access to your server from the public IP address of your PBX on both port 80 and 8080 in our example below. Here’s how to accomplish that. Create a new file in /etc/pbx/httpdconf. Create public.conf with the following contents:
Listen 8080 <virtualhost *:80> ServerAdmin you@gmail.com ServerName 111.112.113.114 Redirect 403 / UseCanonicalName Off UserDir disabled </virtualhost> <virtualhost *:8080> ServerAdmin you@gmail.com ServerName 111.112.113.114 Redirect 403 / UseCanonicalName Off UserDir disabled </virtualhost> <virtualhost *:80> ServerAdmin you@gmail.com ServerName server-fqdn.com DocumentRoot /var/www/html/ucp ErrorLog /var/log/httpd/error_log CustomLog /var/log/httpd/access_log common </virtualhost> <virtualhost *:80> ServerAdmin you@gmail.com ServerName 10.8.0.123 DocumentRoot /var/www/html ErrorLog /var/log/httpd/error_log CustomLog /var/log/httpd/access_log common </virtualhost> <virtualhost *:8080> ServerAdmin you@gmail.com ServerName server-fqdn.com DocumentRoot /var/www/html ErrorLog /var/log/httpd/error_log CustomLog /var/log/httpd/access_log common </virtualhost> <virtualhost 127.0.0.1:80> ServerAdmin you@gmail.com ServerName 127.0.0.1 ServerAlias localhost DocumentRoot /var/www/html </virtualhost>
In the ServerAdmin lines, insert your email address. Replace 111.112.113.114 with the public IP address of your server. Replace server-fqdn.com with the FQDN assigned for SIP registration access to your PBX. Replace 10.8.0.123 with the OpenVPN private IP address of your PBX. Replace 8080 with the port you chose for FreePBX access to your server. Save the file and then restart Apache: systemctl restart httpd.
Now it should be safe to open TCP port 80 and 8080 (or whatever port you chose) for web access to your server. Let’s also whitelist TCP 2267 for Clearly Anywhere access while we’re at it. On the Debian 10 platform, here are the commands:
cd /etc/iptables sed -i 's/10000:20000 -j ACCEPT/&\\n-A INPUT -p tcp -m tcp --dport 8080 -j ACCEPT/' rules.v4 sed -i 's/10000:20000 -j ACCEPT/&\\n-A INPUT -p tcp -m tcp --dport 80 -j ACCEPT/' rules.v4 sed -i 's/10000:20000 -j ACCEPT/&\\n-A INPUT -p tcp -m tcp --dport 2267 -j ACCEPT/' rules.v4 iptables-restart
Be sure to test all three access methods to verify that you haven’t left a security hole.
Keeping FreePBX 15 Modules Current
We strongly recommend that you periodically update all of your FreePBX modules to eliminate bugs and to reduce security vulnerabilities. From the Linux CLI, log into your server as root and issue the following commands:
rm -f /tmp/* fwconsole ma upgradeall fwconsole reload /root/sig-fix systemctl restart apache2 /root/sig-fix
Special Thanks: We want to give an extra special tip of the hat to the VoIP-Info Forum members who assisted in working the kinks out of the Incredible PBX 2021 PUBLIC offering. We also wish to thank JavaPipe LLC for a number of DDOS tips and tricks in securing Linux with IPtables.
Originally published: Monday, December 21, 2020

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

A New Day: Introducing Incredible PBX 2021 Beta for Debian

Shifting gears is never easy, and sometimes it takes an ill-advised corporate blunder to move the needle. But IBM’s decimation of the CentOS project last week was just the motivation we needed to begin exploring alternatives for the Incredible PBX project. We are delighted to introduce the beta release of Incredible PBX 2021 for Debian 10 for those with a pioneering spirit that would like to participate in development of this promising new platform.
Before we get started, a few cautionary notes. This is not production-ready software. It’s been in development for less than a week by a single individual. As much as we believe in miracles, this probably is not one of them. Having said that, many talented individuals on the VoIP-Info.org Forum have taken this for a spin and offered numerous suggestions. You, too, can follow our progress and participate. With a little luck, we’ll have a production-ready release before the end of 2020. We’ve successfully built a fully-functional version of Incredible PBX 2021 with on-premise hardware using VirtualBox and VMware ESXi. And we’ve deployed virtual machines at Vultr and Digital Ocean without a hiccup.
For those that would like to roll up your sleeves and contribute to this open source project, here’s how to get started. If you’re using on-premise hardware, begin by downloading the netinst ISO image of Debian 10.7 for amd64. Follow our previous tutorials for tips on installation with VirtualBox or VMware ESXi. If you’d prefer to experiment in the cloud for about a penny an hour, open an account at Vultr or Digital Ocean using our referral links that support the Nerd Vittles project. You’ll also get some free credit to try out the service. Then create a new $5/month Debian 10, 64-bit instance in your favorite city.
Once your Debian 10 platform is up and running, login as root using SSH or Putty and issue the following commands:
wget http://incrediblepbx.com/IncrediblePBX2021.sh chmod +x IncrediblePBX2021.sh ./IncrediblePBX2021.sh
At about 5 minutes into the install procedure, you’ll be prompted for your telephone country code. It’s 1 for Canada and the United States. Just before the install completes, you’ll be prompted to save your default IPtables setup. Once the installation completes, reboot and you should be good to go. For tips on next steps, review the Incredible PBX 2020 CentOS 7 tutorial.
After you log back in following a reboot, check the version of Debian 10 in the pbxstatus display. If it’s less than 10.7, issue the following commands to bring your server up to Debian 10.7. Do NOT do this before the base install is finished, or Asterisk may fail to install properly.
apt-get update apt-get upgrade -y
Next Steps with Incredible PBX 2021
Before you can manage your PBX through a web browser, you first will need to set the admin passwords for FreePBX, Apache web apps such as Reminders and AsteriDex, and AvantFax (if you are using Incredible Fax). These all can be set by logging into your server as root and issuing the following commands: admin-pw-change, apache-pw-change, and avantfax-pw-change. The AvantFax password can also be reset with a browser by first logging in as admin with a password of password.
Outbound mail functionality needs to be working so that you can receive voicemail messages and faxes by email. To prevent SPAM, most ISPs and ITSPs block messages from downstream mail servers. That would be you. The easiest way to resolve this is to configure SendMail using Gmail as an SMTP Smarthost. You obviously need a Gmail account to implement this and, if you have turned on two-factor authentication for your Gmail account, you also will need to obtain an App password for your Gmail account, and use that in lieu of your regular Gmail password when configuring SendMail. With your Gmail username and password in hand, log into your server as root and run: /root/enable-gmail-smarthost-for-sendmail.
If your Incredible PBX 2021 is hosted with a cloud provider, be advised that many providers do not include a swap file as part of their offering. FreePBX requires a swap file. To add one, issue this command after logging into your server as root: /root/create-swapfile-DO.
To correctly set the time on your PBX, run: /root/timezone-setup.
By default, the voicemail password for each of the configured extensions (701-705) is set to the extension number. This means the user will be prompted to set a voicemail password on the first login to voicemail for each extension. A phone must be registered to the actual extension to access its voicemail account. For example, once a phone is registered to extension 701, the voicemail setup can be accessed by dialing *98701.
If you want to send and receive faxes with Incredible PBX 2021, run the following script while logged into your server as root: /root/incrediblefax2020-debian10.sh. When prompted, accept all the defaults. Once the HylaFax and AvantFax components are installed, reboot your server. To send faxes, click on the AvantFax tab in the FreePBX GUI and enter your login credentials (default: admin/password). To receive incoming faxes once you have configured a trunk and DID for your PBX, login to the FreePBX GUI as admin. Navigate to Connectivity -> Inbound Routes. For each of your DIDs on which you wish to receive faxes, select the inbound route and click the Fax tab. Review the Default Inbound Route Fax settings for proper setup.
NOTE: If you get a database error when you attempt to access AvantFax from a web browser, log into your server as root and reinstall the AvantFax database: ./avantfax-db-replace.
Audio Issues with Incredible PBX 2021
If you experience one-way or no audio on some calls, add your external IP address and LAN subnet in the GUI by navigating to Settings -> Asterisk SIP Settings. In the NAT Settings section, click Detect Network Settings. Click Submit and Apply Settings to save your changes.
Adding Incredible PBX 2021 to an OpenVPN Network
We previously have documented the procedure for creating an OpenVPN server as well as OpenVPN client templates (.ovpn). If you need a refresher, the tutorial is here. To add your Incredible PBX 2021 server to an existing OpenVPN network, begin by creating an incrediblepbx2021.ovpn template on your OpenVPN server. Be sure to comment out or delete the setenv line in the template. Then copy this template to /etc on your Incredible PBX 2021 server. Next, issue the following commands to put the remaining pieces in place:
cp -p /root/openvpn-start /etc/. echo "[Unit] Description=openvpn2021 ConditionPathExists=/etc/openvpn-start After=rclocal.service [Service] Type=forking ExecStart=/etc/openvpn-start /etc/incrediblepbx2021.ovpn TimeoutSec=0 StandardOutput=tty RemainAfterExit=yes PermissionsStartOnly=true SysVStartPriority=99 [Install] WantedBy=multi-user.target" > /etc/systemd/system/openvpn2021.service
Finally, enable the new openvpn2021.service and reboot your server. The OpenVPN IP address should now appear on the LAN line in pbxstatus:
systemctl enable openvpn2021.service reboot
Incredible PBX 2021 Administration
We’ve eased the pain of administering your new PBX with a collection of scripts which you will find in the /root folder after logging in with SSH or Putty. Here’s a quick summary of what each of the scripts does.
add-fqdn is used to whitelist a fully-qualified domain name in the firewall. Because Incredible PBX 2021 blocks all traffic from IP addresses that are not whitelisted, this is what you use to authorize an external user for your PBX. The advantage of an FQDN is that you can use a dynamic DNS service to automatically update the IP address associated with an FQDN so that you never lose connectivity.
add-ip is used to whitelist a public IP address in the firewall. See the add-fqdn explanation as to why this matters.
del-acct is used to remove an IP address or FQDN from the firewall’s whitelist.
admin-pw-change is used to set the admin password for access to the FreePBX/Incredible PBX web GUI using a browser pointed to the local IP address of your server.
apache-pw-change is used to set the admin password for access to Apache/Incredible PBX apps including AsteriDex and Reminders. This provides a password layer of protection for access to these applications.
avantfax-email-change is used to change the destination email address for incoming faxes.
avantfax-pw-change is used to change your admin password for the AvantFax web console.
iaxmodem-restart is used to restart the modems used to send and deliver faxes. The pbxstatus display will tell you whether the IAXmodems are down.
incrediblebackup2021 makes a backup of critical components on your PBX to a tarball saved in /backup. This should be copied to safe location off-site for a rainy day.
incrediblerestore2021 restores a backup file which has been copied to the /backup folder.
ipchecker is a script which deciphers the public IP addresses associated with whitelisted FQDNs created with add-fqdn on your server. If any of the addresses have changed, the firewall is restarted after updating the IP addresses. By default, it is executed every 10 minutes by /etc/crontab.
licenses.sh displays the license associated with each of the FreePBX modules on your server.
logos-b-gone removes proprietary artwork from your PBX and is no longer necessary with the included IncrediblePBX FreePBX module.
mime-construct is a command-line utility to send emails with attachments.
neorouter-login is a script to add your PBX to a NeoRouter VPN. Tutorial here.
odbc-gen.sh is a script that was run to generate the ODBC settings for Asterisk. Do NOT use it.
openvpn-start is a script to add your PBX to an existing OpenVPN network using an .ovpn config file. Tutorial here.
pbxstatus displays status of all major components of Incredible PBX 2021.
pptp-install is a script to create a PPTP network connection for your PBX. Tutorial here.
purge-cdr-cel-records removes all CDR and CEL records from the MySQL database.
reset-conference-pins is a script that automatically and randomly resets the user and admin pins for access to the preconfigured conferencing application. Dial C-O-N-F from any registered SIP phone to connect to the conference.
reset-extension-passwords is a script that automatically and randomly resets ALL of the SIP passwords for extensions 701-705. Be careful using this one, or you may disable existing registered phones and cause Fail2Ban to blacklist the IP addresses of those users. HINT: You can place a call to the Ring Group associated with all five extensions by dialing 777.
reset-reminders-pin is a script that automatically and randomly resets the pin required to access the Telephone Reminders application by dialing 123. It’s important to protect this application because a nefarious user could set up a reminder to call a number anywhere in the world assuming your SIP provider’s account was configured to allow such calls.
show-feature-codes is a cheat sheet for all of the feature codes which can be dialed from any registered SIP phone. It documents how powerful a platform Incredible PBX 2021 actually is. A similar listing is available in the GUI at Admin -> Feature Codes.
show-passwords is a script that displays most of the passwords associated with Incredible PBX 2021. This includes SIP extension passwords, voicemail pins, conference pins, telephone reminders pin, and your Anveo Direct outbound calling pin (if configured). Note that voicemail pins are configured by the user of a SIP extension the first time the user accesses the voicemail system by dialing *97.
sig-fix disables Module Signature Checking in the FreePBX GUI. This should not be necessary unless you have added or edited FreePBX Modules with missing module signatures.
sms-skyetel is a script to send SMS messages using a Skyetel trunk.
sms-voip.ms is a script to send SMS messages using a VoIP.ms trunk.
sms-blast, sms-blaster, and sms-dictator are scripts for message blasting. Tutorial here.
switch-to-php5.6 is a script to disable PHP 7.3 and set PHP 5.6 as the default version for your PBX. PHP 5.6 is required to use AvantFax. It is the default configuration for Incredible PBX 2021. The current default PHP version is displayed in the Apache listing of pbxstatus.
switch-to-php7.3 is a script to disable PHP 5.6 and set PHP 7.3 as the default version for your PBX. You cannot use AvantFax when PHP 7.3 is the default.
timezone-setup is a script to set the timezone for your PBX.
update-IncrediblePBX is a script that runs the Automatic Update Utility whenever you login to your server as root. These updates typically resolve bugs and security issues with your PBX. Do NOT remove it.
wolfram is a script to deploy Wolfram Alpha on your PBX. Tutorial here.
Forwarding Calls to Your Cellphone. Keep in mind that inbound calls to your DIDs automatically ring all five SIP extensions, 701-705. The easiest way to also ring your cellphone is to set one of these five extensions to forward incoming calls to your cellphone. After logging into your PBX as root, issue the following command to forward calls from extension 705 to your cellphone: asterisk -rx "database put CF 705 6781234567"
To remove call forwarding: asterisk -rx "database del CF 705"
Keeping FreePBX 15 Modules Current
We strongly recommend that you periodically update all of your FreePBX modules to eliminate bugs and to reduce security vulnerabilities. From the Linux CLI, log into your server as root and issue the following commands:
rm -f /tmp/* fwconsole ma upgradeall fwconsole reload /root/sig-fix systemctl restart apache2 /root/sig-fix
Originally published: Monday, December 14, 2020

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

Introducing OpenVPN for Incredible PBX

We’ve been wrestling with virtual private networks for more than 22 years now. Here’s a quick walk down memory lane. Our adventure began with the Altiga 3000 series VPN concentrators which we introduced in the federal courts in 1999. It was a near perfect plug-and-play hardware solution for secure communications between remote sites using less than secure Windows PCs. Cisco quickly saw the potential, gobbled up the company, and promptly doubled the price of the rebranded concentrators. Over a decade ago, we introduced Hamachi® VPNs to interconnect Asterisk® and PBX in a Flash servers. At the time, Hamachi was free, but that was short-lived when they were subsequently acquired by LogMeIn®. What followed was a short stint with PPTP VPNs which worked great with Macs, Windows PCs, and many phones but suffered from an endless stream of security vulnerabilities. Finally, in April 2012, we introduced the free NeoRouter® VPN. Version 2 still is an integral component in every Incredible PBX® platform today, and PPTP still is available as well. While easy to set up and integrate into multi-site Asterisk deployments, the Achilles’ Heel of NeoRouter remains its inability to directly interconnect many smartphones and stand-alone SIP phones, many of which now support the OpenVPN platform.

The main reason we avoided OpenVPN® over the years was its complexity to configure and deploy.1 In addition, it was difficult to use with clients whose IP addresses were frequently changing. Thanks to the terrific work of Nyr, Stanislas Angristan, and more than a dozen contributors, OpenVPN now has been tamed. And the new server-based, star topology design makes it easy to deploy for those with changing or dynamic IP addresses. Today we’ll walk you through building an OpenVPN server as well as the one-minute client setup for almost any Asterisk deployment and most PCs, routers, smartphones, and VPN-compatible soft phones and SIP phones including Yealink, Grandstream, Snom, and many more. And the really great news is that OpenVPN clients can coexist with your current NeoRouter VPN.
Finally, a word about the OpenVPN Client installations below. We’ve tested all of these with current versions of Incredible PBX 13-13 and 16-15 as well as Incredible PBX 2020 and Incredible PBX 2021. They should work equally well with other server platforms which have been properly configured. However, missing dependencies on other platforms are, of course, your responsibility.
Building an OpenVPN Server Platform
There are many ways to create an OpenVPN server platform. The major prerequisites are a supported operating system, a static IP address for your server, and a platform that is extremely reliable and always available. If the server is off line, all client connections will also fail. While we obviously have not tested all the permutations and combinations, we have identified a platform that just works™. It’s the CentOS 7, 64-bit cloud offering from Vultr. If you use our referral link at Vultr, you not only will be supporting Nerd Vittles through referral revenue, but you also will be able to take advantage of their $100 free credit for new customers. For home and small business deployments, we have found the $5/month platform more than adequate, and you can add automatic backups for an additional $1 a month. Cheap insurance!
A more recent and less costly hosting alternative is the $25/year Crown Cloud offering that we introduced several weeks ago. It includes a free snapshot backup in the $25 annual price.
To get started, create your CentOS 7 instance and login as root using SSH or Putty. Immediately change your password and update and install the necessary CentOS 7 packages. Be sure to turn off SELinux if it is installed by default.
passwd setenforce 0 # edit /etc/selinux/config # insert: SELINUX=disabled # save the SELinux config file yum -y update yum -y install net-tools nano wget tar iptables-services systemctl stop firewalld systemctl disable firewalld systemctl enable iptables
We recommend keeping your OpenVPN server platform as barebones as possible to reduce the vulnerability risk. By default, this installer routes all client traffic through the VPN server which wastes considerable bandwidth. The sed commands below modify this design to only route client VPN traffic through the OpenVPN server.
#!/bin/bash ##filename # openvpn-install-mod echo " Fix script /root/openvpn-install.sh to ensure internet traffic doesn't use vpn-tunnel." echo " " read -p " Press 'Enter' to continue at your own risk, or Ctrl+c to abort." ##trap user non root if [ "$(id -u)" -ne 0 ]; then echo "" echo "Must be run as root user: sudo $0" echo "" exit 1 fi # cd /root echo " Fetching latest copy of install script /root/openvpn-install.sh from github.com/Angristan" curl -O https://raw.githubusercontent.com/Angristan/openvpn-install/master/openvpn-install.sh chmod +x openvpn-install.sh echo " running 3 sed commands to ensure only local traffic uses vpn-tunnel :-" echo ' 1st commenting-out line 857' #### fails to complete with \\"redirect-gateway ## sed -i "s|\\techo 'push \\"redirect-gateway|#\\techo 'push \\"redirect-gateway|" openvpn-install.sh sed -e '/redirect-gateway d/s/^/#/' -i openvpn-install.sh echo '2nd commenting-out line 865' ###sed -i "s|push \\"redirect-gateway|#push \\"redirect-gateway|" openvpn-install.sh sed -e '/redirect-gateway ipv6/s/^/#/' -i openvpn-install.sh echo '3rd after line 1042 ; newline 1043 pull-filter ignore redirect-gateway' ###sed -i 's|tls-client|tls-client\\npull-filter ignore "redirect-gateway"|' openvpn-install.sh sed -i 's|tls-client|tls-client\npull-filter ignore "redirect-gateway"|' openvpn-install.sh
Here are the recommended entries in running the OpenVPN installer:
- Server IP Address: using FQDN strongly recommended to ease migration issues
- Enabled IPv6 (no): accept default
- Port (1194): accept default
- Protocol (UDP): accept default
- DNS (3): change to 9 (Google)
- Compression (no): accept default
- Custom encrypt(no): accept default
- Generate Server
- Client name: firstclient
- Passwordless (1): accept default
NOTE: On CentOS 7 platforms, edit /usr/lib/systemd/system/openvpn@.service. Scroll down to the ExecStart= line and change %i.conf to %I.conf. Then save the file. Special thanks to @mattburris for catching the error.
In the following steps, we will use IPtables to block all server access except via SSH or the VPN tunnel. Then we’ll start your OpenVPN server:
cd /etc/sysconfig wget http://incrediblepbx.com/iptables-openvpn.tar.gz tar zxvf iptables-openvpn.tar.gz rm -f iptables-openvpn.tar.gz echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf sysctl -p systemctl -f enable openvpn@server.service systemctl start openvpn@server.service systemctl status openvpn@server.service systemctl enable openvpn@server.service systemctl restart iptables
Once OpenVPN is enabled, the server can be reached through the VPN at 10.8.0.1. OpenVPN clients will be assigned by DHCP in the range of 10.8.0.2 through 10.8.0.254. You can list your VPN clients like this: cat /etc/openvpn/ipp.txt. You can list active VPN clients like this: cat /var/log/openvpn/status.log | grep 10.8. And you can add new clients or delete old ones by rerunning /root/openvpn-install.sh.
For better security, change the SSH access port replacing 1234 with desired port number:
PORT=1234 sed -i "s|#Port 22|Port $PORT|" /etc/ssh/sshd_config systemctl restart sshd sed -i "s|dport 22|dport $PORT|" /etc/sysconfig/iptables systemctl restart iptables
We’ve made changes in the Angristan script to adjust client routing. By default, all packets from every client flowed through the OpenVPN server which wasted considerable bandwidth. Our preference is to route client packets destined for the Internet directly to their destination rather than through the OpenVPN server. The sed commands added to the base install above do this; however, if you’ve already installed and run the original Angristan script, your existing clients will be configured differently. Our recommendation is to remove the existing clients, make the change below, and then recreate the clients again by rerunning the script. In the alternative, you can execute the command below to correct future client creations and then run it again on each existing client platform substituting the name of the /root/.ovpn client file for client-template.txt and then restart each OpenVPN client.
cd /etc/openvpn sed -i 's|tls-client|tls-client\\npull-filter ignore "redirect-gateway"|' client-template.txt
Creating OpenVPN Client Templates
In order to assign different private IP addresses to each of your OpenVPN client machines, you’ll need to create a separate client template for each computer. You do this by running /root/openvpn-install.sh again on the OpenVPN server. Choose option 1 to create a new .ovpn template. Give each client machine template a unique name and do NOT require a password for the template. Unless the client machine is running Windows, edit the new .ovpn template and comment out the setenv line: #setenv. Save the file and copy it to the /root folder of the client machine. Follow the instructions below to set up OpenVPN on the client machine and before starting up OpenVPN replace firstclient.ovpn in the command line with the name of .ovpn you created for the individual machine.

Renewing OpenVPN Server’s Expired Certificate
The server certificate will expire after 1080 days, and clients will no longer be able to connect. Here’s what to do next:
systemctl stop openvpn@server.service cd /etc/openvpn/easy-rsa ./easyrsa gen-crl cp /etc/openvpn/easy-rsa/pki/crl.pem /etc/openvpn/crl.pem systemctl start openvpn@server.service
Installing an OpenVPN Client on CentOS/RHEL
cd /root yum -y install epel-release yum --enablerepo=epel install openvpn -y # copy /root/firstclient.ovpn from server to client /root # and then start up the VPN client openvpn --config /root/firstclient.ovpn --daemon # adjust Incredible PBX firewall below iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT cd /usr/local/sbin echo "iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT" >> iptables-custom
Running ifconfig should now show the VPN client in the list of network ports:
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.2 P-t-P:10.8.0.2 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:9 errors:0 dropped:0 overruns:0 frame:0
TX packets:39 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:855 (855.0 b) TX bytes:17254 (16.8 KiB)
And you should be able to login to the VPN server using its VPN IP address:
# enter actual SSH port replacing 1234 PORT=1234 ssh -p $PORT root@10.8.0.1
Installing an OpenVPN Client on Debian and Ubuntu
cd /root apt-get update apt-get install openvpn unzip dpkg-reconfigure tzdata # copy /root/firstclient.ovpn from server to client /root # and then start up the VPN client openvpn --config /root/firstclient.ovpn --daemon # adjust Incredible PBX firewall below iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT cd /usr/local/sbin echo "iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT" >> iptables-custom
Running ifconfig should now show the VPN client in the list of network ports:
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.2 P-t-P:10.8.0.2 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:9 errors:0 dropped:0 overruns:0 frame:0
TX packets:39 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:855 (855.0 b) TX bytes:17254 (16.8 KiB)
And you should be able to login to the VPN server using its VPN IP address:
# enter actual SSH port replacing 1234 PORT=1234 ssh -p $PORT root@10.8.0.1
Installing an OpenVPN Client on Raspbian
The OpenVPN client now is easy to install on the latest Incredible PBX builds for the Raspberry Pi. Log into your server as root and issue the following commands to set your time zone and install the OpenVPN client. pbxstatus should then show the 10.8.0.x VPN address in the Private IP listing.
dpkg-reconfigure tzdata apt-get install openvpn unzip # copy your .ovpn template into /root # edit template and comment out setenv line # start up the client using actual .ovpn filename openvpn --config /root/raspi.ovpn --daemon # adjust Incredible PBX firewall iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT cd /usr/local/sbin echo "iptables -A INPUT -s 10.8.0.0/24 -j ACCEPT" >> iptables-custom iptables-restart pbxstatus

Installing an OpenVPN Client on a Mac
While there are numerous OpenVPN clients for Mac OS X, none hold a candle to Tunnelblick in terms of ease of installation and use. First, create a new client config on your server and copy it (/root/*.ovpn) to a folder on your Mac where you can find it. Download Tunnelblick and install it. Run Tunnelblick and then open Finder. Click and drag your client config file to the Tunnelblick icon in the top toolbar. Choose Connect when prompted. Done.
Installing an OpenVPN Client for Windows 10
The installation procedure for Windows is similar to the Mac procedure above. Download the OpenVPN Client for Windows. Double-click on the downloaded file to install it. Create a new client config on your server and copy it (/root/*.ovpn) to a folder on your PC where you can find it. Start up the OpenVPN client and click on the OpenVPN client in the activity tray. Choose Import File and select the config file you downloaded from your OpenVPN Server. Right-click on the OpenVPN icon again and choose Connect. Done.
Installing an OpenVPN Client for Android
Our favorite OpenVPN client for Android is called OpenVPN for Android and is available in the Google Play Store. Download and install it as you would any other Android app. Upload a client config file from your OpenVPN server to your Google Drive. Run the app and click + to install a new profile. Navigate to your Google Drive and select the config file you uploaded.
Installing an OpenVPN Client for iOS Devices
The OpenVPN Connect client for iOS is available in the App Store. Download and install it as you would any other iOS app. Before uploading a client config file, open the OpenVPN Connect app and click the 4-bar Settings icon in the upper left corner of the screen. Click Settings and change the VPN Protocol to UDP and IPv6 to IPV4-ONLY Tunnel. Accept remaining defaults.
To upload a client config file, the easiest way is to use Gmail to send yourself an email with the config file as an attachment. Open the message with the Gmail app on your iPhone or iPad and click on the attachment. Then choose the Upload icon in the upper right corner of the dialog. Next, choose Copy to OpenVPN in the list of apps displayed. When the import listing displays in OpenVPN Connect, click Add to import the new profile. Click ADD again when the Profile has been successfully imported. You’ll be prompted for permission to Add VPN Configurations. Click Allow. Enter your iOS passcode when prompted. To connect, tap once on the OpenVPN Profile. To disconnect, tap on the Connected slider. When you reopen the OpenVPN Connect app, the OVPN Profiles menu will display by default. Simply tap once on your profile to connect thereafter.
Installing a Web Interface to Display Available Clients
One advantage of NeoRouter is a simple way for any VPN client to display a listing of all VPN clients that are online at any given time. While that’s not possible with OpenVPN, we can do the next best thing and create a simple web page that can be accessed using a browser but only from a connected OpenVPN client pointing to http://10.8.0.1.
To set this up, log in to your OpenVPN server as root and issue the following commands:
yum --enablerepo=epel install lighttpd -y systemctl start lighttpd.service systemctl enable lighttpd.service chown root:lighttpd /var/log/openvpn/status.log chmod 640 /var/log/openvpn/status.log cd /var/www rm -rf lighttpd wget http://incrediblepbx.com/lighttpd.tar.gz tar zxvf lighttpd.tar.gz ln -s /var/log/openvpn/status.log /var/www/lighttpd/status.log sed -i 's|#server.bind = "localhost"|server.bind = "10.8.0.1"|' /etc/lighttpd/lighttpd.conf systemctl restart lighttpd.service
UPDATE: On some cell phones and on Windows PCs, you may observe that you can no longer reach your favorite web sites after enabling the OpenVPN client. Luckily there’s a simple fix that allows 10.8.0.x traffic to be sent through the OpenVPN tunnel while all other traffic is routed out of your standard network connection. Here’s the fix. Make sure the .ovpn client config file includes the following lines:
pull-filter ignore redirect-gateway route-nopull route 10.8.0.0 255.255.255.0
Originally published: Monday, July 20, 2020 Updated: Saturday, June 25, 2022

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

- Our discussion today is focused on the free, MIT-licensed version of OpenVPN. For details on their commercial offerings, follow this link. [↩]
Turning Incredible PBX into a Lean, Mean Asterisk Machine

Mexican Food isn’t for everyone and once in a while we get asked for a tutorial showing how to take the Whole Enchilada version of Incredible PBX® 2020 back to its roots as a Lean, Mean Asterisk® Machine. Still others want to better understand how all the Incredible PBX 2020 pieces are put in place so that unused components can be removed easily. So today’s your lucky day as we roll back the shroud of secrecy surrounding the open source Incredible PBX 2020 installer. We’re being facetious, of course, because the source code has always been available for everyone to examine and modify to your heart’s content. But we appreciate that some may not be comfortable tackling this independently for fear of breaking something.
The short answer is that most of the Incredible PBX additions to Asterisk and FreePBX® are housed in the extensions_custom.conf file in /etc/asterisk and the collection of files in /var/lib/asterisk/agi-bin. But deleting those files would be a very bad idea and most certainly would break much of the functionality of the underlying Asterisk and FreePBX platform.
Our approach today is to document how to delete each piece of the Incredible PBX puzzle so that you can keep the features you like and remove the rest. We’ve resisted documenting some of this previously because these components don’t typically hurt anything or consume processing resources if they’re not used. But we appreciate there are purists that want a pristine clean platform to call their own. So… here goes.
Before we get started, let me document how most of the Incredible PBX contexts in extensions_custom.conf were designed so that they could easily be removed or updated. At the top and bottom of each context, you’ll find two lines that look something like this:
;# // BEGIN Redialer ; Asterisk dialplan code goes here ;# // END Redialer
Using the label Redialer, the entire context can be removed with a single sed command:
sed -i '\:// BEGIN Redialer:,\:// END Redialer:d' extensions_custom.conf
As we walk through the various functions and contexts below, we’ll use sed Label:d as a short-hand notation for the context removal procedure in the steps that follow.
Finally, before you make any changes to your server, please MAKE A BACKUP. For the latest scripts, issue the following commands after logging into the Linux CLI as root:
cd /root wget http://incrediblepbx.com/incrediblebackup2020.tar.gz tar zxvf incrediblebackup2020.tar.gz rm -f incrediblebackup2020.tar.gz ./incrediblebackup2020
Removing Telephone & Web Reminder Apps
1. From /etc/asterisk/extensions_custom.conf, sed Reminders:d
2. From /var/lib/asterisk/agi-bin, remove checktime.php, checkdate.php, reminder.php, run_*
3. From /var/lib/asterisk/sounds/en/custom, rm -f remind*
4. From /var/www/html, rm -rf reminders
5. From /var/spool/asterisk, rm -rf recurring AND rm -rf reminders
6. fwconsole ma delete reminders
7. fwconsole reload
8. asterisk -rx "dialplan reload"
9. fwconsole restart
Much of the Telephone Reminders code is more than a decade old and was installed long before the current sed design with labels was implemented. So the final step in removing all of the reminders contexts is to edit extensions_custom.conf and manually delete all commands within the following contexts and then reload the Asterisk dialplan in the usual way: asterisk -rx "dialplan reload"
[reminder] [reminder2] [reminder3] [reminder4] [reminder5] [reminder6] [reminder7] [reminder8] [reminder9] [reminder9a] [remindem]
Removing AsteriDex & AsteriDex SpeedDialer Apps
1. From /etc/asterisk/extensions_custom.conf, sed AsteriDex SpeedDial:d
2. From /etc/asterisk/extensions_custom.conf, sed Call by Code:d
3. From /etc/asterisk/extensions_custom.conf, sed Call by Name:d
4. From /var/lib/asterisk/agi-bin, remove asteridex.php
5. From /var/lib/asterisk/agi-bin, remove nv-call*
6. mysql -u root -ppassw0rd -e "drop database asteridex"
7. From /var/www/html, rm -rf asteridex4
8. fwconsole ma delete asteridex
9. fwconsole reload
10. asterisk -rx "dialplan reload"
11. fwconsole restart
Removing SMS Dictator App
1. From /etc/asterisk/extensions_custom.conf, sed SMS Dictator:d
2. From /var/lib/asterisk/agi-bin, rm -f sms*
3. asterisk -rx "dialplan reload"
Removing Travelin’ Man 4 Dialer App
1. From /etc/asterisk/extensions_custom.conf, sed Travelin’ Man 4 Dialer:d
2. From /etc/asterisk, rm -rf tm4
3. mysql -u root -ppassw0rd -e "drop database TravMan4″
4. asterisk -rx "dialplan reload"
Removing Wolfram Alpha App
1. From /etc/asterisk/extensions_custom.conf, sed Wolfram Alpha:d
2. From /var/lib/asterisk/agi-bin, rm -f wolfram.sh
3. From /var/lib/asterisk/agi-bin, rm -f 4747*
4. asterisk -rx "dialplan reload"
Removing Yahoo News App
1. From /etc/asterisk/extensions_custom.conf, sed nv-news-yahoo:d
2. From /var/lib/asterisk/agi-bin, rm -f nv-news*
3. asterisk -rx "dialplan reload"
Removing Weather Apps
1. From /etc/asterisk/extensions_custom.conf, sed Weather by ZIP:d
2. From /var/lib/asterisk/agi-bin, rm -f nv-weather*
3. From /var/lib/asterisk/agi-bin, rm -f zipcod*
4. asterisk -rx "dialplan reload"
Removing Today in History App
1. From /etc/asterisk/extensions_custom.conf, sed Today in History:d
2. From /var/lib/asterisk/agi-bin, rm -f nv-today*
3. rm -f /tmp/today
4. asterisk -rx "dialplan reload"
Removing Tides App
1. From /etc/asterisk/extensions_custom.conf, sed xTide:d
2. From /var/lib/asterisk/agi-bin, rm -f xtide*
3. mysql -u root -ppassw0rd -e "drop database tides"
4. asterisk -rx "dialplan reload"
Removing SIP URI App
1. From /etc/asterisk/extensions_custom.conf, sed SIP URI Mod1:d
2. From /etc/asterisk/extensions_custom.conf, sed SIP URI Mod2:d
3. asterisk -rx "dialplan reload"
Removing Redialer App
1. From /etc/asterisk/extensions_custom.conf, sed Redialer:d
2. asterisk -rx "dialplan reload"
Removing Google TTS Apps
1. From /var/lib/asterisk/agi-bin, rm -f googletts*
Removing Stocks App
1. From /var/lib/asterisk/agi-bin, rm -f nv-stock*
Removing Dictionary App
1. From /var/lib/asterisk/agi-bin, rm -f nv-dict*
Removing the ODBC Demo Apps
As installed, Incredible PBX reserves extensions 222 and 223 for a couple of applications demonstrating the use of ODBC connections with Asterisk. Some may prefer to use these extensions for other purposes so you have two choices. You can either renumber the extensions, or you can delete the demo applications entirely. To renumber the extensions, edit /etc/asterisk/odbc.conf. Then search and replace the 222 and 223 entries. To remove the applications entirely, simply rename the odbc.conf file to odbc.conf.orig. Then reload the dialplan: asterisk -rx "dialplan reload"
We recommend you revisit this article in a week or two to see if other additions and corrections have been made. If so, they will appear below here. Enjoy!
Originally published: Monday, June 1, 2020

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.

The Next Best Thing to (formerly free) Google Voice

Today we want to once again shine the spotlight on LocalPhone, an oft-overlooked VoIP service that’s been around forever. You can call to and be called from any LocalPhone user at no cost. They also offer phone numbers (DIDs) of your choice almost anywhere in the world with free or almost free incoming calls. For those wanting a U.S. DID, the cost is 99¢ a month with a $3 setup fee. That gets you up to 100 free incoming calls a day to your PBX or any SIP phone. Additional calls are a penny per call. There are no limitations on the duration of the calls. If you prefer to forward the calls to your cellphone number in the contiguous U.S., there’s an additional fee of 0.5¢ per minute. But there’s little reason to do that when sending the calls to a SIP softphone on your Android device or iPhone is free. And now the mobile LocalPhone app supports PUSH Notifications. We’ll show you how.
FYI: Nerd Vittles receives a referral credit to keep the lights on when you sign up for service.
Deciphering Your SIP Credentials with LocalPhone
Once you have signed up for a LocalPhone account, the first thing you’ll want to do is make note of your Internet Phone credentials under My Account. These are what we typically refer to as SIP credentials consisting of a SIP ID, SIP password, and SIP server (localphone.com). That’s all you’ll need to configure an incoming LocalPhone trunk on any Incredible PBX® server. And these are the same settings you’d use to configure any SIP phone running on any Android or iOS device. As we noted, you and any other LocalPhone user can call any Internet Phone number worldwide at no cost without limitation. For world travelers, you’ll want to download the LocalPhone app for your smartphone (Android or iOS) and take advantage of their extremely competitive international calling rates.1
Ordering Incoming Numbers (DIDs) from LocalPhone
Begin by funding your account under My Account -> Add Credit. $10 will last you a long time.
The next step is to order one or more incoming phone numbers from LocalPhone.2 If you have friends in far away places that call you frequently, you can purchase DIDs in those locations to eliminate the cost of incoming calls both to them and to you. If you only want a dirt cheap U.S. DID for your home or small office, then LocalPhone is also a perfect fit. Navigate to My Account -> Incoming Numbers and choose the United States as the desired Country. Next, pick the State and City for the desired DID. For free incoming calls, set Call Forwarding and Caller ID for Internet Phone to your assigned Internet Phone SIP ID. You can also elect to forward calls to a SIP URI, if desired. Agree to the terms of use and make your purchase.
Configuring a LocalPhone Trunk with Incredible PBX
We’ve previously covered the LocalPhone trunk setup with Wazo. Most other releases of Incredible PBX include preconfigured LocalPhone trunks for incoming and outgoing calls. Login to the Incredible PBX GUI as admin using your favorite browser and navigate to Connectivity -> Trunks and edit the LocalPhone-In trunk. Set Disable Trunk to NO. Then click the sip-Settings tab. Insert your LocalPhone SIP ID in the username, fromuser, and authuser fields. Insert your LocalPhone SIP Password in the secret field. Change the context field entry to from-trunk. Click on the Incoming tab, and modify the Register String 9999999:yourpassword@localphone.com/9999999 replacing 9999999 with your LocalPhone SIP ID and yourpassword with your LocalPhone SIP Password. Click the Submit button and reload your dialplan when prompted.
Navigate to Connectivity -> Inbound Routes and create a new Inbound Route for LocalPhone using your SIP ID as the DID Number and choosing a desired Destination for incoming calls from your LocalPhone DID. Save your settings and reload the dialplan when prompted.
Configuring a LocalPhone Trunk with VitalPBX
Login to the VitalPBX GUI as admin using your favorite browser and navigate to PBX -> External -> Trunks. Create a new SIP trunk with the following settings replacing 999999 with your LocalPhone SIP ID and 1234 with the LocalPhone SIP Password. Leave the Device for Incoming Calls (User) section blank. Then click SAVE and reload your dialplan.
- Description: LocalPhone
- Codecs: ulaw,alaw
- Local Username: 999999
- Remote Host: localphone.com
- Remote Port: 5060
- Local Secret: 1234
- Insecure: Port,Invite
- Allow Inbound Calls: YES
- Username: [leave blank]
- Host: [leave blank]
- Local Secret: [leave blank]
- Remote Username: 999999
- Remote Secret: 1234
- From User: 999999
- From Domain: localphone.com
- Qualify: YES
- Insecure: [leave blank]
- IP Authentication: NO
- Qualify: [leave default]
- Register String: 999999:1234@localphone.com/999999
Navigate to PBX -> External -> Inbound Routes. Create a new Inbound Route for LocalPhone using your SIP ID as the DID Number and choosing a desired Destination for incoming calls from your LocalPhone DID. Save your settings and reload the dialplan when prompted.
Configuring a LocalPhone Trunk with FreePBX
Login to the FreePBX® GUI as admin using your favorite browser and navigate to Connectivity -> Trunks. Add a new chan_sip trunk named localphone. Then click on the sipSettings tab and enter the following replacing 999999 with your LocalPhone SIP ID and 1234 with the LocalPhone SIP Password.
- username=9999999
- type=friend
- secret=1234
- nat=no
- insecure=port,invite
- host=localphone.com
- fromuser=9999999
- fromdomain=localphone.com
- dtmfmode=rfc2833
- disallow=all
- context=from-trunk
- canreinvite=no
- authuser=9999999
- allow=ulaw&alaw
Next, click on the Incoming tab and enter the following Register String replacing 999999 with your LocalPhone SIP ID and 1234 with the LocalPhone SIP Password:
9999999:1234@localphone.com/9999999
Then click SUBMIT and reload your dialplan.
Navigate to Connectivity -> Inbound Routes and create a new Inbound Route for LocalPhone using your SIP ID as the DID Number and choosing a desired Destination for incoming calls from your LocalPhone DID. Save your settings and reload the dialplan when prompted.
Using Local Numbers for International Calls
LocalPhone has a unique feature that lets you dial a local number from a phone number you have whitelisted in your country and reach almost anyone in the world that you’ve added to your Contacts List. You only pay LocalPhone’s discounted international calling rate for the calls. For example, to call a landline in the U.K. from the U.S. using a LocalPhone-provided U.S. phone number, the calling rate is less than a penny a minute. A call to Cyprus by dialing a U.S. number assigned to your account for your whitelisted phone numbers is 4.5 cents per minute. To get started setting up your whitelisted phone numbers and contacts list, navigate to My Account -> Local Numbers in your LocalPhone account. In your Local Numbers list, first add and verify phone numbers you want to authorize to make calls on your nickel. Next, add the names and phone numbers of international destinations you wish to reach by dialing a local number. LocalPhone will immediately assign a local number for each destination. Simply add these local numbers to the contacts list on your smartphone, and you can call from anywhere in your country at the discounted LocalPhone international calling rates. There are no double-dialing or call menus to navigate. Dialing the assigned local number transparently connects you directly to your destination with no intermediate hurdles.
Using LocalPhone with Other Trunk Providers
So long as your PBX doesn’t have more than two incoming calls to a single DID at the same time, the most economical PBX design is to use LocalPhone DIDs as your published DIDs. This reduces the cost of incoming calls to less than a dollar a month per DID for up to 3,000 incoming calls of unlimited duration. Then use one of our Platinum Sponsors, Skyetel or our soon-to-be-available ClearlyIP SIP trunking service for outbound calls and spoof the outbound CallerID on those other trunks using your LocalPhone DID.
Enjoying the Best of All Worlds with LocalPhone
If you have an iPhone or Android smartphone in addition to a PBX, you can take advantage of LocalPhone’s ability to send incoming calls to multiple destinations. Just make sure your PBX isn’t routing the incoming calls to a destination that is automatically answered, e.g. an IVR. On your Android phone, download the VitalPBX Communicator from the Google Play Store and configure a SIP connection using your LocalPhone SIP credentials. Incoming calls from your LocalPhone DIDs and Internet Phone Number now will be sent to both destinations.
If you have followed one of our previous tutorials that document making SIP URI calls from either a PBX or a SIP client such as LinPhone on your smartphone, then you can take advantage of LocalPhone’s incoming SIP URI feature.3 Just dial 9999999@localphone.com where 9999999 is any LocalPhone SIP ID. You also can add Custom Extensions in Incredible PBX much like the Lenny extension using a Dial string of SIP/9999999@localphone.com to reach worldwide LocalPhone destinations from any PBX extension at no cost. Enjoy!
Originally published: Monday, December 9, 2019

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here. The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI. VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive! Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
- Rates are based on the lowest pay as you go per-minute price to call a landline or a mobile. Skype is a registered trademark of Microsoft Corporation. [↩]
- LocalPhone advises that DID fulfillment can take up to 14 days although our orders always have been completed in less than an hour. [↩]
- LocalPhone offers call filtering for your Internet Phone number using either a blacklist or whitelist in addition to offering the option of blocking anonymous calls. [↩]
Interconnect Incredible PBX 16-15 to the Asterisk Mothership

The Holy Grail for a mobile VoIP solution is a simple way to connect back to your primary Asterisk® PBX via Wi-Fi from anywhere in the world to make and receive calls as if you never left. Let’s tick off the potential problems. First, many home-based PBXs are sitting behind NAT-based routers. Second, almost all remote Wi-Fi connections are made through a NAT-based router. Third, chances are the remote hosting platform blocks outgoing email from downstream servers such as a mobile PBX. Fourth, deciphering the IP address of your remote connection can be problematic. Fifth, the chances of experiencing one-way audio or no audio on your VoIP calls is high because of NAT-based routers at both ends of your connection.
For those that travel regularly and want to avoid the complexity of configuring OpenVPN, here is a quick thumbnail of the setup we recommend as your mobile companion. You’ll never have a one-way audio problem again. In terms of hardware, you’ll need a Raspberry Pi 4B or 3B+ with its native WiFi support plus a Windows or Mac notebook computer for traveling. You’ll also need a NeoRouter VPN server to make this process seamless. If you’ve already set up an OpenVPN server platform, it will work equally well. One advantage of NeoRouter is that clients can be added from the client side without having to create a config file on the VPN server. All you need is a username and password. But the choice of VPN platform is totally a matter of preference. The objective using either OpenVPN or NeoRouter is secure communications to your home base. We don’t want to have to reconfigure either your home PBX or your traveling Raspberry Pi or your notebook PC based upon changes in your public and private IP addresses.
Today we’ll walk you through the easiest way to set up a (free) NeoRouter server on the Internet. It can be used to connect up to 254 devices on an encrypted private LAN. We’re delighted to have finally found a perfect use for the (free) Google Cloud instance.

Using a Raspberry Pi, build an Incredible PBX 16-15 platform by following our previous tutorial. We’ll set this up on your home WiFi network so that you only have to throw the Raspberry Pi and its power supply in your suitcase when you travel. As part of the setup, we’ll download NeoRouter and activate private IP addresses for your notebook computer as well as both of your PBXs (using nrclientcmd). Next, we’ll interconnect the two PBXs using SIP trunks and the NeoRouter private LAN IP addresses. We’ll take advantage of a neat little Raspberry Pi trick by storing a wpa_supplicant.conf template on your PC for the remote WiFi setup even though we don’t yet know anything about the remote LAN. Once we know the SSID and password at the remote destination, we’ll use your notebook computer to edit the template and transfer the file to the /boot folder of your RasPi’s microSD card. When the card then is inserted and the RasPi is booted, it will automatically move the template to the proper /etc/wpa_supplicant folder to successfully activate your WiFi connection. We’ll also load links, a fast text-based browser, just in case you encounter a hotel that requires some sort of acknowledgement or password before establishing your WiFi connection to the Internet.

Setting Up a (free) NeoRouter Server in the Cloud
Because NeoRouter uses a star-based VPN architecture, that means the NeoRouter Server must always be available at the same IP address for all of the NeoRouter Clients (aka Nodes) to talk to. If you already have a cloud-based server that has a static IP address and can handle the traffic cop duties of NeoRouter Server, then that’s an ideal place to install NeoRouter Server. Simply download the Free flavor of NeoRouter Server that matches your existing platform and install it. Add an FQDN for your server’s IP address, and you’re all set. A detailed summary of available management options is included in our previous NeoRouter v2 article.
We devoted a couple weeks to Google Cloud instances, and it turned out to be a pretty awful platform for hosting Asterisk. But the free offering looks to be a perfect fit as a hosting platform for NeoRouter Server. You also won’t have to worry about Google going out of business anytime soon. So let us walk you through an abbreviated setup process on the Google Cloud platform. If you’re just getting started with Google Cloud, read our previous article to take advantage of Google’s generous $300 offer to get you started and to generally familiarize yourself with the mechanics of setting up an instance in the Google Cloud.
For NeoRouter Server, navigate to https://console.cloud.google.com. Click the 3-bar image ![]() in the upper left corner of your Dashboard. This exposes the Navigation Menu. In the COMPUTE section of the Dashboard, click Compute Engine -> VM Instances. Then click CREATE PROJECT and name it. Now click CREATE INSTANCE and Name it nrserver. The instance name becomes the hostname for your virtual machine. If you want to remain in the Free Tier, choose f1-micro instance as the Machine Type and choose a U.S. Region (us-central1, us-east1 or us-west1). For the Boot Disk, choose CentOS 6 and expand the disk storage to at least 20GB (30GB is available with the Free Tier). For the Firewall setting, leave HTTP and HTTPS disabled. Check your entries carefully and then click the Create button.
in the upper left corner of your Dashboard. This exposes the Navigation Menu. In the COMPUTE section of the Dashboard, click Compute Engine -> VM Instances. Then click CREATE PROJECT and name it. Now click CREATE INSTANCE and Name it nrserver. The instance name becomes the hostname for your virtual machine. If you want to remain in the Free Tier, choose f1-micro instance as the Machine Type and choose a U.S. Region (us-central1, us-east1 or us-west1). For the Boot Disk, choose CentOS 6 and expand the disk storage to at least 20GB (30GB is available with the Free Tier). For the Firewall setting, leave HTTP and HTTPS disabled. Check your entries carefully and then click the Create button.
When your virtual machine instance comes on line, jot down the assigned public IP address. We’ll need it in a minute. Now click on the SSH pull-down tab and choose Open in a Browser Window. Now we need to set a root password and adjust the SSH settings so that you can login from your desktop computer using SSH or Putty:
sudo passwd root su root nano -w /etc/ssh/sshd_config
When the editor opens the SSH config file, add the following entries. Then save the file and restart SSH: service sshd restart
PermitRootLogin yes PasswordAuthentication yes
You now should be able to log in to your instance as root from your desktop computer using SSH or Putty. Test it to be sure: ssh root@server-IP-address
Before we leave the Google Cloud Dashboard, let’s make the assigned public IP address permanent so that it doesn’t get changed down the road. Keep in mind that, if you ever delete your instance, you also need to remove the assigned static IP address so you don’t continue to get billed for it. From Home on the Dashboard, scroll down to the NETWORKING section and choose VPS Network -> External IP Addresses. Change the Type of your existing address to Static and Name it staticip. Next, choose Firewall Rules in the VPS Network section and click CREATE FIREWALL RULE. Fill in the template like the following leaving the other fields with their default entries. Then click CREATE.
- Name: neorouter
- Target Tags: neorouter
- Source IP Range: 0.0.0.0/0
- Protocols/Ports: check tcp: 32976
CAUTION: Before this firewall rule will be activated for your instance, it also must be specified in the Network Tags section for your instance. Shut down your instance and add the neorouter tag by editing your instance. Then restart your instance.
Now we’re ready to install NeoRouter Free v2 Server on your instance. Be sure to choose the Free v2 variety. Log back into your server as root using SSH/Putty and issue these commands:
yum -y update yum -y install nano wget http://download.neorouter.com/Downloads/NRFree/Update_2.3.1.4360/Linux/CentOS/nrserver-2.3.1.4360-free-centos-x86_64.rpm rpm -Uvh nrserver-2.3.1.4360-free-centos-x86_64.rpm /etc/rc.d/init.d/nrserver.sh restart nrserver -setdomain <DOMAINNAME> <DOMAINPASSWORD> nrserver -adduser <USERNAME> <PASSWORD> admin nrserver -enableuser <USERNAME> nrserver -showsettings
Finally, add the following command to /etc/rc.local so that NeoRouter Server gets started whenever your instance is rebooted:
echo "/etc/rc.d/init.d/nrserver.sh start" >> /etc/rc.local
Installing Incredible PBX 16-15 on a Raspberry Pi

Configuring NeoRouter Client on Your Computers
On Linux-based (non-GUI) platforms, setting up the NeoRouter Client is done by issuing the command: nrclientcmd. You’ll be prompted for your NeoRouter Server FQDN as well as your username and password credentials. Perform this procedure on both your home PBX and the Raspberry Pi.
To add your Windows or Mac notebook to the NeoRouter VPN, download the appropriate client and run the application which will prompt for your NeoRouter Server FQDN as well as your NeoRouter credentials. Once completed, you should see all three machines in your NeoRouter Free Client Dashboard: your PC as well as your home PBX and Raspberry Pi-based Incredible PBX. Make note of the private VPN addresses (10.0.0.X) of both your home PBX and your Raspberry Pi. These VPN addresses never change, and we’ll need them to interconnect your PBXs and to set up a softphone on your notebook computer.
Admininistrative Tools to Manage NeoRouter
Here are a few helpful commands for monitoring and managing your NeoRouter VPN.
To access your NeoRouter Linux client: nrclientcmd
To restart NeoRouter Linux client: /etc/rc.d/init.d/nrservice.sh restart
To restart NeoRouter Linux server: /etc/rc.d/init.d/nrserver.sh restart
To set domain: nrserver -setdomain YOUR-VPN-NAME domainpassword
For a list of client devices: nrserver -showcomputers
For a list of existing user accounts: nrserver -showusers
For the settings of your NeoRouter VPN: nrserver -showsettings
To add a user account: nrserver -adduser username password user
To add admin account: nrserver -adduser username password admin
For a complete list of commands: nrserver –help

Interconnecting Your Raspberry Pi and Home PBX
To keep things simple, our setup examples below assume the following NeoRouter VPN addresses: Home PBX (10.0.0.1) and Raspberry Pi (10.0.0.2). Using a browser, you’ll need to login to the GUI of your Home PBX and Raspberry Pi and add a Trunk to each PBX. Be sure to use the same secret on BOTH trunk setups. We don’t recommend forwarding incoming calls from your Home PBX to your Raspberry Pi because most folks won’t be sitting in their hotel room all day to answer incoming calls. Instead, add the number of your smartphone to a Ring Group on the Home PBX and don’t forget the # symbol at the end of the number. On the Raspberry Pi side, we are assuming that whenever a call is dialed from a registered softphone with the 9 prefix, the call will be sent to the Home PBX for call processing (without the 9). For example, 98005551212 would send 800-555-1212 to the Home PBX for outbound routing and 9701 would send 701 to the Home PBX for routing to the 701 extension. You can obviously adjust your dialplan to meet your own local requirements.
On the Home PBX, the chan_sip trunk entries should look like this:
Trunk Name: raspi-remote PEER DETAILS host=10.0.0.2 type=friend context=from-internal username=home-pbx fromuser=home-pbx secret=some-password canreinvite=no insecure=port,invite qualify=yes nat=yes
On the Raspberry Pi, the chan_sip trunk entries should look like this:
Trunk Name: home-pbx PEER DETAILS host=10.0.0.1 type=friend context=from-internal username=raspi-remote fromuser=raspi-remote secret=some-password canreinvite=no insecure=port,invite qualify=yes nat=yes
On the Raspberry Pi, add an Outbound Route named Out9-home-pbx pointed to home-pbx Trunk with the following Dial Patterns. For each Dial Pattern, prepend=blank and prefix=9:
dial string: 1NXXNXXXXXX dial string: NXXNXXXXXX dial string: *98X. dial string: XXX dial string: XXXX dial string: XXXXX
Tweaking Your Raspberry Pi for WiFi Mobility
wpa_supplicant.conf config file to the /boot directory on the card once you arrive at your destination and know the SSID and password of the local WiFi network. When the Raspberry Pi is subsequently booted, the operating system will move the config file to the /etc/wpa_supplicant directory so that your WiFi network will come on line. Here’s what a typical wpa_supplicant.conf file should look like using your actual credentials. The last network section handles open WiFi network connections (think: McDonald’s) if you want to enable them:
country=US
update_config=1
network={
ssid="your-SSID"
psk="your-SSID-password"
key_mgmt=WPA-PSK
scan_ssid=1
priority=5
}
network={
key_mgmt=NONE
priority=1
}
The other gotcha is that some public WiFi networks require some type of web login procedure before you can actually access the Internet even though an IP address may have been assigned to your Raspberry Pi. To handle this situation, you’ll need a text-based web browser on the Raspberry Pi that can be accessed through your notebook PC using SSH and your Raspberry Pi’s VPN address. Our favorite is links which can be installed on your Raspberry Pi before you pack up.
apt-get install links -y
Once you arrive at your destination, connect both your notebook PC and Raspberry Pi to the same WiFi network, login to the RasPi with SSH at the VPN address assigned to your RasPi, and run links to start the browser. Press <esc> to access the links menu options. If you can’t access your RasPi at the VPN IP address, try its WiFi-assigned local IP address.
Adding a Softphone to Your Notebook PC
For Windows PCs, we recommend VitalPBX Communicator. It’s a free download from here.

Another good choice is YateClient which also is free. Download it from here. Run YateClient once you’ve installed it and enter the credentials for an extension on your Raspberry Pi. Then enter the VPN IP address of your server plus your extension’s password. Click OK to save your entries.

If you are a Mac user, another great no-frills softphone is Telephone. Just download and install it from the Mac App Store.
Adding a Softphone to Your Smartphone
Enjoy your pain-free traveling!
Originally published: Monday, September 9, 2019

Need help with Asterisk? Visit the VoIP-info Forum.
Special Thanks to Our Generous Sponsors
FULL DISCLOSURE: ClearlyIP, Skyetel, Vitelity, DigitalOcean, Vultr, VoIP.ms, 3CX, Sangoma, TelecomsXchange and VitalPBX have provided financial support to Nerd Vittles and our open source projects through advertising, referral revenue, and/or merchandise. As an Amazon Associate and Best Buy Affiliate, we also earn from qualifying purchases. We’ve chosen these providers not the other way around. Our decisions are based upon their corporate reputation and the quality of their offerings and pricing. Our recommendations regarding technology are reached without regard to financial compensation except in situations in which comparable products at comparable pricing are available from multiple sources. In this limited case, we support our sponsors because our sponsors support us.
 BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
BOGO Bonaza: Enjoy state-of-the-art VoIP service with a $10 credit and half-price SIP service on up to $500 of Skyetel trunking with free number porting when you fund your Skyetel account. No limits on number of simultaneous calls. Quadruple data center redundancy. $25 monthly minimum spend required. Tutorial and sign up details are here.
 The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
The lynchpin of Incredible PBX 2020 and beyond is ClearlyIP components which bring management of FreePBX modules and SIP phone integration to a level never before available with any other Asterisk distribution. And now you can configure and reconfigure your new Incredible PBX phones from the convenience of the Incredible PBX GUI.
 VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
VitalPBX is perhaps the fastest-growing PBX offering based upon Asterisk with an installed presence in more than 100 countries worldwide. VitalPBX has generously provided a customized White Label version of Incredible PBX tailored for use with all Incredible PBX and VitalPBX custom applications. Follow this link for a free test drive!
 Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.
Special Thanks to Vitelity. Vitelity is now Voyant Communications and has halted new registrations for the time being. Our special thanks to Vitelity for their unwavering financial support over many years and to the many Nerd Vittles readers who continue to enjoy the benefits of their service offerings. We will keep everyone posted on further developments.



 JUST RELEASED: Visit the Incredible PBX Wiki
JUST RELEASED: Visit the Incredible PBX Wiki